Oracle has linked ongoing Clop ransomware extortion attacks to critical vulnerabilities in its E-Business Suite patched in July 2025. The company confirms customers received ransom demands while urging immediate patching, as threat actors exploit flaws allowing remote access without credentials.

Oracle has officially connected an ongoing corporate extortion campaign to critical vulnerabilities in its E-Business Suite (EBS) platform—flaws the company patched in its July 2025 Critical Patch Update. The Clop ransomware gang, notorious for mass-exploitation of enterprise software, is demanding ransom payments from organizations allegedly compromised through these unpatched security holes.
Rob Duhart, Oracle's Chief Security Officer, confirmed in a public statement: "Oracle is aware that some Oracle E-Business Suite (EBS) customers have received extortion emails. Our ongoing investigation has found the potential use of previously identified vulnerabilities that are addressed in the July 2025 Critical Patch Update."
The July update resolved nine EBS security flaws, including three remotely exploitable vulnerabilities (CVE-2025-30745, CVE-2025-30746, and CVE-2025-50107) that require no user credentials for initial access. These weaknesses provide a direct path for attackers to infiltrate enterprise resource planning systems housing financial, HR, and operational data.
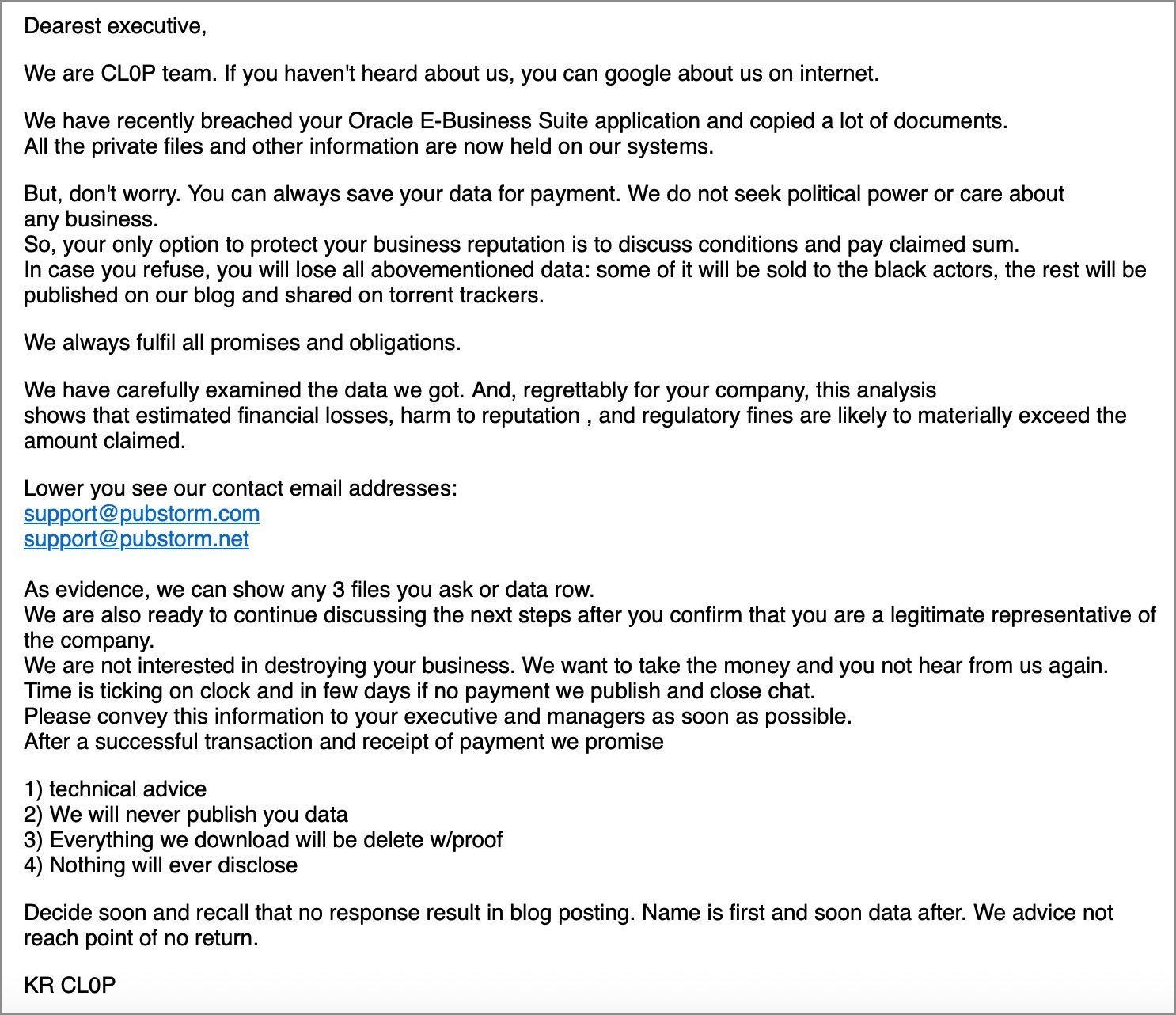
According to Mandiant and Google's Threat Intelligence Group (GTIG), corporate executives began receiving extortion emails in late September 2025. Genevieve Stark, head of GTIG's cybercrime unit, confirmed the campaign's timeline, noting investigations are ongoing. The emails—bearing Clop's signature—declare: "We have recently breached your Oracle E-Business Suite application and copied a lot of documents. All the private files and other information are now held on our system."
Clop representatives doubled down in communications with BleepingComputer, claiming: "Soon all will become obvious that Oracle bugged up their core product... We do not damage to systems and only expect payment for services we provide to protect hundreds of biggest companies in world."
This incident mirrors Clop's established playbook: exploiting zero-day vulnerabilities in widely used enterprise software to steal data for extortion. The group previously weaponized flaws in Accellion FTA, GoAnywhere MFT, and MOVEit Transfer—the latter impacting over 2,770 organizations globally. Their January 2025 campaign leveraged a Cleo secure file transfer zero-day (CVE-2024-50623).
Despite Clop's boasts, Mandiant CTO Charles Carmakal cautioned that evidence of actual data theft remains inconclusive. Nevertheless, the U.S. State Department now offers a $10 million reward for information linking Clop to foreign governments, underscoring the group's threat level.
Oracle's advisory leaves no ambiguity: Organizations must immediately apply the July 2025 patches to EBS environments. For enterprises managing complex ERP deployments, this incident is a stark reminder that delayed patching of business-critical systems creates low-hanging fruit for ransomware syndicates—especially when vulnerabilities bypass authentication controls. As supply chain attacks evolve, the window between patch release and weaponization shrinks relentlessly.
Source: BleepingComputer (Sergiu Gatlan)

Comments
Please log in or register to join the discussion