Oracle has quietly fixed a zero-day vulnerability (CVE-2025-61884) in its E-Business Suite after the ShinyHunters extortion group leaked a functional exploit. The patch arrives amid confusion over multiple active exploit chains and Oracle's failure to disclose active attacks despite evidence of server breaches. Security teams scramble to untangle mismatched advisories while urging immediate patching.
The Silent Oracle Patch: Untangling the E-Business Suite Exploit Chaos

Oracle has deployed a stealth security update for a critical vulnerability in its widely used E-Business Suite (EBS) platform, closing a backdoor that extortion groups actively weaponized. The flaw, tracked as CVE-2025-61884, enables unauthenticated attackers to perform Server-Side Request Forgery (SSRF) attacks, potentially accessing sensitive resources. The patch arrived without fanfare over the weekend—despite proof that threat actors exploited it in live attacks and the public release of a functional exploit by the ShinyHunters cybercriminal group.
Oracle’s sparse advisory acknowledges the flaw’s severity but omits crucial context:
"This vulnerability is remotely exploitable without authentication... If successfully exploited, this vulnerability may allow access to sensitive resources."
Multiple researchers and customers confirmed to BleepingComputer that the update finally addresses the SSRF vulnerability exploited in ShinyHunters’ leaked proof-of-concept (PoC). The exploit targets the /configurator/UiServlet endpoint, enabling attackers to manipulate server requests and bypass security controls.
The Extortion Tangle: Clop, ShinyHunters, and Confusing Advisories
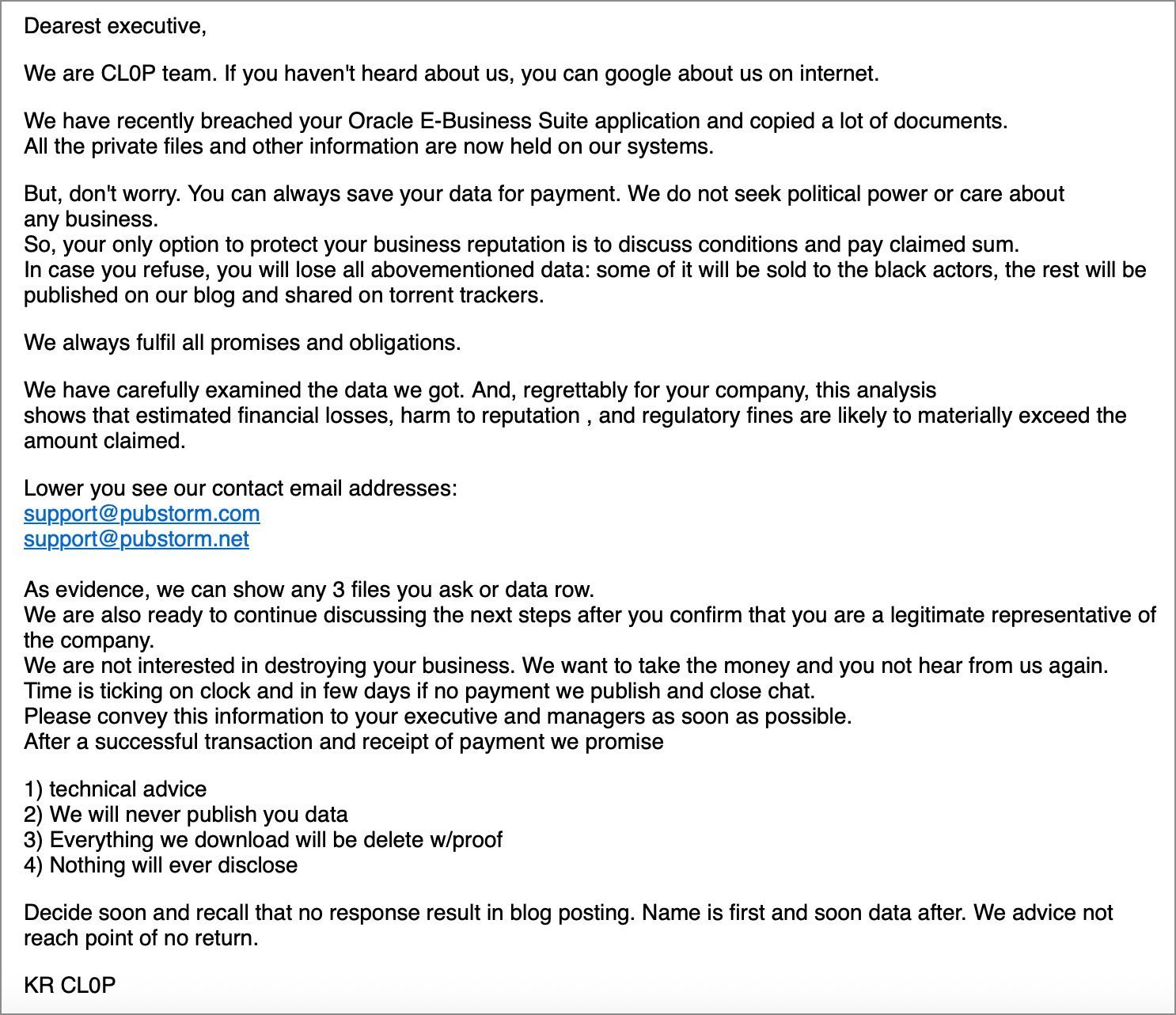 Clop's extortion email targeting Oracle EBS customers (Source: BleepingComputer)
Clop's extortion email targeting Oracle EBS customers (Source: BleepingComputer)
The patch arrives amid a convoluted extortion campaign involving multiple threat actors:
- Clop ransomware operators began emailing victims in early October, claiming theft of Oracle EBS data via a "new" zero-day. They bragged to BleepingComputer: “Oracle bugged up their core product... once again, the task is on clop to save the day.”
- ShinyHunters (Scattered Lapsus$ Hunters) soon after leaked a functional EBS exploit on Telegram—the one exploiting CVE-2025-61884.
Oracle initially attributed Clop’s attacks to a flaw patched in July 2025 (CVE-2025-61882), urging customers to update. Days later, it issued an emergency patch for CVE-2025-61882, oddly listing ShinyHunters’ UiServlet exploit as an indicator of compromise (IoC)—even though its patch didn’t fix it.
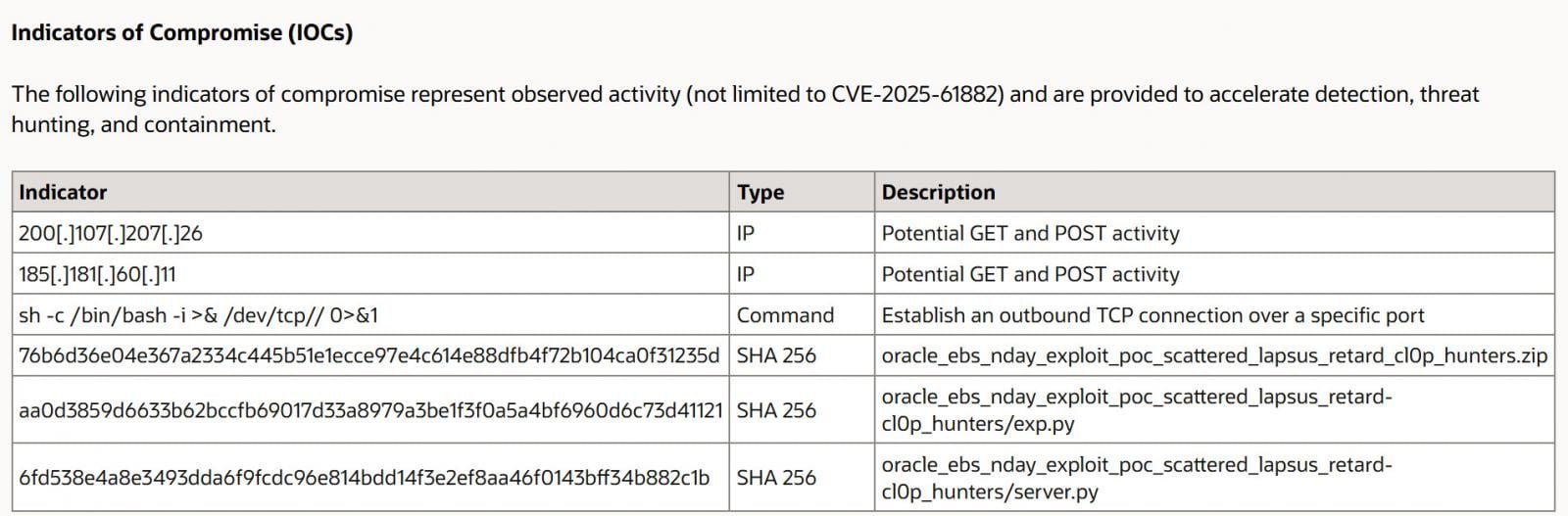 Oracle’s mismatched IoC listing for CVE-2025-61882 (Source: Oracle)
Oracle’s mismatched IoC listing for CVE-2025-61882 (Source: Oracle)
Why the Silence Matters
Researchers at watchTowr Labs confirmed ShinyHunters’ exploit could achieve remote code execution, while Mandiant and CrowdStrike identified a separate SyncServlet endpoint exploit (/OA_HTML/SyncServlet) used by Clop. This created a perfect storm:
- Oracle’s October 4 patch for CVE-2025-61882 broke Clop’s SyncServlet chain but left ShinyHunters’ UiServlet exploit functional.
- Customers reported the SSRF component remained exploitable even after patching CVE-2025-61882.
- The new patch (CVE-2025-61884) finally adds regex validation to block malicious
return_urlpayloads in UiServlet requests.
Oracle declined repeated requests from BleepingComputer to clarify the discrepancies or acknowledge active exploitation. Mandiant noted dryly: "It's currently unclear which specific vulnerabilities/exploit chains correspond to CVE-2025-61882."
The Urgent Takeaway for DevSecOps Teams
The technical disarray underscores critical lessons:
- Patch Immediately: Install both CVE-2025-61882 and CVE-2025-61884 updates. Exploit chains are now public.
- Temporary Mitigation: If patching is delayed, block access to
/configurator/UiServletvia mod_security rules. - Assume Breach: Extortion groups possess multiple exploit chains. Audit EBS environments for unusual activity.
As exploit kits evolve and extortion gangs weaponize silences in vendor disclosures, Oracle’s opaque response leaves enterprises navigating a minefield blindfolded. In the absence of clarity, proactive defense isn’t just best practice—it’s survival.
Source: BleepingComputer

Comments
Please log in or register to join the discussion