Orchid Security launches platform to discover, analyze, and govern identity usage across enterprise applications, addressing the 'Identity Dark Matter' blind spot that traditional IAM tools miss.
Orchid Security has introduced a new platform for continuous identity observability across enterprise applications, addressing a critical blind spot that traditional identity and access management (IAM) tools miss. The company's approach targets what they call "Identity Dark Matter" - the identity logic, credentials, and access patterns that exist outside traditional IAM controls.
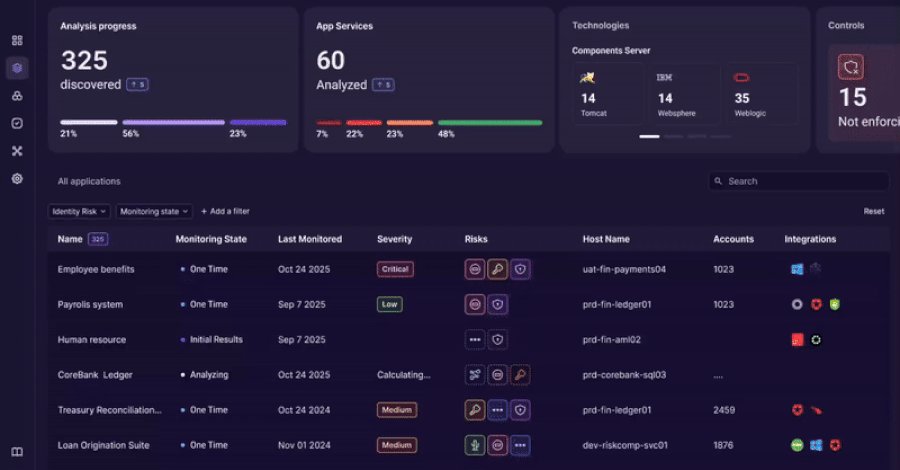
The Identity Visibility Gap
Modern enterprise environments have evolved beyond centralized identity directories. While IAM tools were designed to govern users and directories, identity logic has increasingly moved into application code, APIs, service accounts, and custom authentication layers. This shift creates significant security challenges.
"Identity and access management tools were built to govern users and directories," explains Orchid Security. "Modern enterprises run on applications. Over time, identity logic has moved into application code, APIs, service accounts, and custom authentication layers."
The result is a growing blind spot for security teams. Credentials become embedded in applications. Authorization is enforced locally within code. Usage patterns change without formal review. These identity paths often operate completely outside the visibility of IAM, privileged access management (PAM), and identity governance and administration (IGA) systems.
Why Traditional IAM Falls Short
Most identity tools rely on configuration data and policy models that work well for managed users but fail to address modern application architectures. Traditional approaches cannot effectively handle:
- Custom-built applications with embedded authentication logic
- Legacy authentication systems that bypass identity providers
- Embedded credentials and secrets within application code
- Non-human identities like service accounts and API keys
- Access paths that circumvent centralized identity controls
This limitation forces security teams to reconstruct identity behavior during audits or incident response - an approach that doesn't scale in modern enterprise environments.
Orchid's Four-Stage Operational Model
Orchid Security addresses this challenge through a continuous identity observability platform that follows a four-stage operational model aligned with how security teams actually work.
Discover: Identify Identity Usage Inside Applications
The platform begins by discovering applications and their identity implementations through lightweight instrumentation. This analysis identifies authentication methods, authorization logic, and credential usage across both managed and unmanaged environments.
Teams gain an accurate inventory of:
- Applications and services in use
- Identity types and their implementations
- Authentication flows and patterns
- Embedded credentials and secrets
This discovery establishes a baseline of identity activity across the entire environment, including areas traditional IAM tools cannot reach.
Analyze: Assess Identity Risk Based on Observed Behavior
Once discovery is complete, Orchid analyzes identity usage in context. The platform correlates identities, applications, and access paths to surface risk indicators based on actual observed behavior rather than assumed policy.
Key risk indicators include:
- Shared or hardcoded credentials
- Orphaned service accounts with active access
- Privileged access paths outside IAM controls
- Drift between intended and actual access patterns
This behavior-driven analysis allows teams to focus on identity risks that are actively in use rather than theoretical vulnerabilities.
Orchestrate: Act on Identity Findings
With analysis complete, Orchid enables teams to take action by integrating with existing IAM, PAM, and security workflows. The platform supports remediation efforts by:
- Prioritizing identity risks by potential impact
- Routing findings to appropriate control owners
- Tracking remediation progress over time
Importantly, Orchid doesn't replace existing controls but coordinates them using accurate identity context derived from actual application behavior.
Audit: Maintain Continuous Evidence of Identity Control
Because discovery and analysis run continuously, audit data is always available. Security and governance, risk, and compliance (GRC) teams can access:
- Current application inventories
- Evidence of identity usage patterns
- Documentation of control gaps and remediation actions
This transforms audit from a periodic scramble into an ongoing process with continuous evidence collection.
Practical Outcomes for Security Teams
Organizations implementing Orchid's platform gain several concrete benefits:
- Improved visibility into application-level identity usage
- Reduced exposure from unmanaged access paths
- Faster audit preparation with continuous evidence
- Clear accountability for identity risk ownership
Most importantly, teams can make decisions based on verified data rather than assumptions about how identity actually operates in their environment.
The Future of Identity Security
As identity continues to move beyond centralized directories, security teams need new approaches to understand and govern access. Orchid Security's continuous identity observability platform represents a shift toward monitoring how identity actually operates in modern enterprise environments rather than how it's supposed to work according to policy documents.
The platform's ability to discover, analyze, orchestrate, and audit identity usage across applications provides organizations with the tools needed to address the growing challenge of Identity Dark Matter - the invisible layer of identity risk that traditional controls cannot see.
For security teams struggling with application-level identity risks, Orchid's approach offers a path to comprehensive visibility and control in an increasingly complex identity landscape.
Comments
Please log in or register to join the discussion