Microsoft 365's convenience creates a security blind spot: unmanaged sharing across Teams, OneDrive, and SharePoint leaves organizations vulnerable to data leaks. This article explores how access reviews for shared content can help security teams regain control without sacrificing collaboration speed.
Cloud collaboration has become a cornerstone of the modern workplace. Millions of companies rely on platforms like Microsoft 365 to enable seamless sharing for their staff. Microsoft Teams alone counts 320 million active users worldwide: a figure that comes close to the entire US population. It's easy to see what makes cloud suites so appealing. Send a presentation to your coworker and discuss their feedback. Hop on a video call with your team and drop the updated slide deck in the meeting chat – all while making lunch plans over Teams. It's never been easier to share documents on the fly.

The problem with making sharing so convenient for end users is that it's impossible for security teams to keep up. With hundreds of users sending links and inviting guests, organizations quickly lose track of what their employees are sharing. Cloud suites empower your staff to make decisions about access without any oversight from IT or security teams: Just click "Share" and tag in coworkers, business partners, contractors or anyone you feel like.
When Cloud Access Goes Too Far
Without suitable guardrails, the use of cloud suites like Microsoft 365 leads to oversharing: Content that is shared longer than necessary or with more people than actually need it. Whether this happens due to carelessness or is done with malicious intent, oversharing is a massive security risk that leaves cloud documents exposed and sensitive data vulnerable to theft, leaks, or breaches.
Problematic sharing often starts out innocent, with access that serves a clear business purpose but goes unchecked for too long. Here are just some examples of what oversharing can look like in practice. Perhaps you recognize similar scenarios from your own workplace.
What Oversharing in Microsoft 365 Looks Like:
- A freelancer receives access to certain files to assist with a project. When the project ends, nobody remembers to cut them out. They retain access indefinitely.
- You set up a spreadsheet to coordinate with your PR agency. You switch agencies the following year, but never delete the original sheet.
- New members join a Microsoft Teams channel. They receive access to everything shared through the Files tab, including sensitive documents you didn't realize were in there.
- You create a folder in SharePoint to share files with one of your suppliers. Over time, users begin storing other documents in the folder without considering who has access to it.
- Sharing links pasted into email chains, inactive accounts that are never removed from cloud documents, etc.
The list goes on. Each scenario represents a small failure in process that compounds into a significant security exposure over time.
The Visibility Problem with Native M365 Tools
Microsoft 365 makes it very easy for users to share documents, but almost impossible for organizations to figure out what their users are sharing. Microsoft 365's own tools offer no visibility into this problem. Information about what users are sharing is split across SharePoint sites, Teams channels and each user's personal OneDrive. There is no centralized reporting for cloud privileges, leaving organizations completely in the dark when it comes to oversharing.
The lack of suitable controls is one of the main drivers behind cloud access risks. Even third-party tools or paid add-ons are not up to the task. For example, while Entra ID Governance does include access reviews, they only cover accounts and group memberships – not shared content. The result is a huge security blind spot that leaves organizations vulnerable to both accidental leakage and targeted data exfiltration.
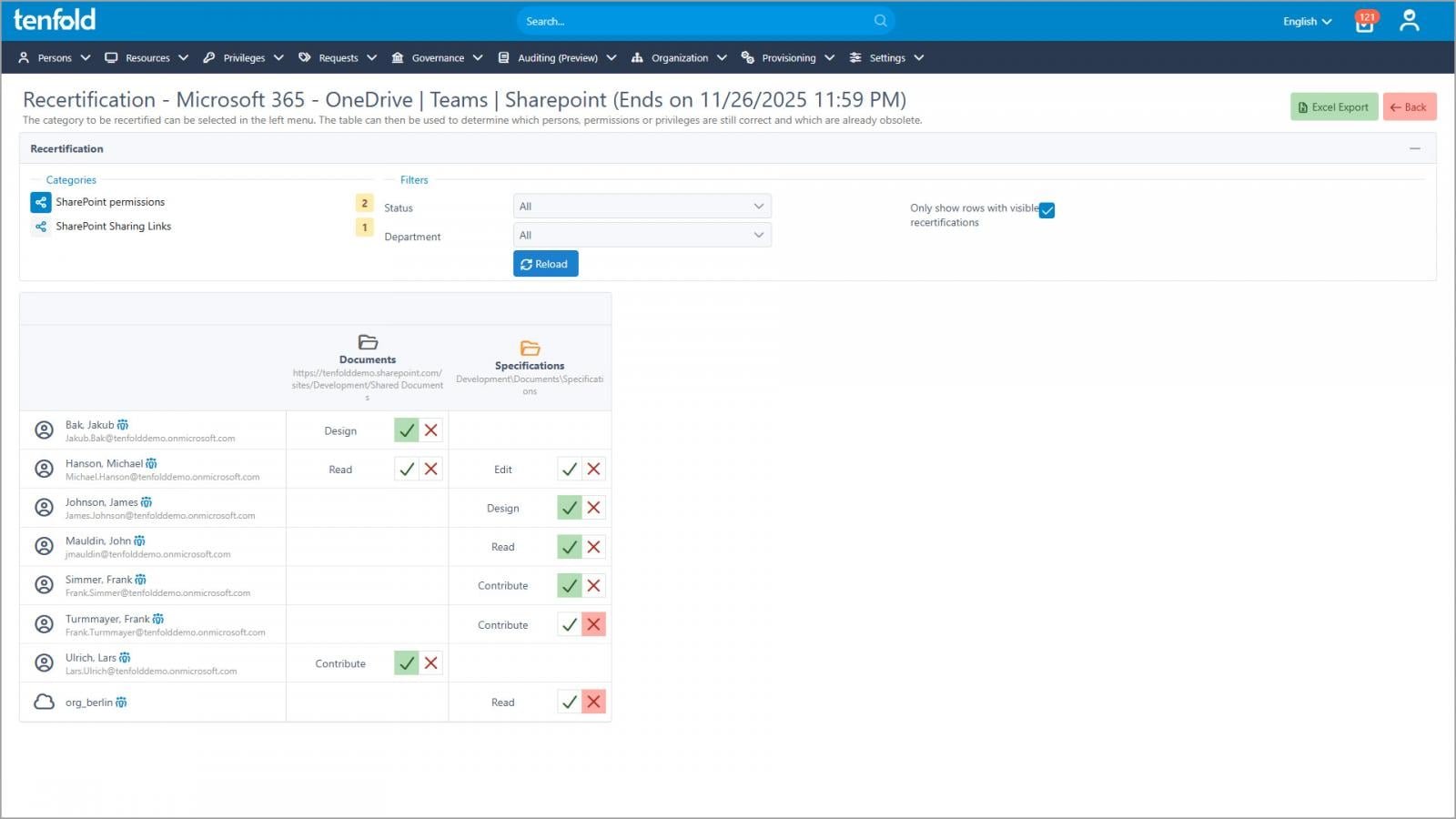
Access reviews for sharing content eliminate outdated and risky cloud privileges.
Addressing the Gap with In-Depth Governance
Only in-depth governance for cloud privilege and shared content can address this risk. If you're one of the many organizations struggling to control shared content, there is good news: Identity Governance solutions are emerging that offer access reviews specifically for shared content.
These solutions provide:
- Central overview of shared content across Teams, OneDrive, and SharePoint
- Access reviews for M365 users, groups, and shared content in one unified interface
- Streamlined review execution with personalized review dashboards
- Complete audit trail of requests, changes, and reviewer decisions
- Automated enforcement of review outcomes
Each user receives a link to their personal review dashboard, which shows all items they are currently sharing and allows them to confirm or remove them with a single click. The system automatically revokes any sharing links or permissions that do not pass the review.
Practical Takeaways for Security Teams
Start with Visibility
Before you can fix oversharing, you need to understand the scope of the problem. Look for tools that aggregate sharing information across all M365 services into a single view. You should be able to answer:
- What documents are shared externally?
- Which users have the most active sharing links?
- How many external users have access to your cloud data?
- Are there sharing links that have never been used?
Implement Regular Review Cycles
Access reviews shouldn't be a one-time event. Set up regular cycles (monthly or quarterly) where users review their own sharing activity. This distributes the workload and makes it manageable. Users are more likely to remember why they shared a document last month than last year.
Focus on High-Risk Scenarios First
Prioritize reviews for:
- External sharing links
- Documents containing sensitive data (PII, financial records, IP)
- Sharing that predates your current security policies
- Access granted to contractors and former employees
Measure and Report
Track metrics over time:
- Number of sharing links revoked per review cycle
- Percentage of users who complete reviews on time
- Reduction in externally shared documents
- Time from access grant to review completion
This data helps justify the program and demonstrates ROI to leadership.
The Path Forward
Oversharing in Microsoft 365 isn't a user education problem – it's a governance problem. No amount of training will eliminate the convenience factor that makes cloud collaboration effective. The solution is implementing systematic controls that maintain security without breaking the workflows your teams depend on.
Regular access reviews for shared content close the security gap created by unmanaged cloud access. They make it possible to use Microsoft 365's sharing features fully without worrying about leaks or breaches. The key is finding a solution that provides both the visibility to see the problem and the tools to fix it efficiently.
For organizations ready to take control of their cloud data, the path forward is clear: implement access reviews that cover not just user accounts, but the actual content those users can access and share.

Comments
Please log in or register to join the discussion