Salesforce has publicly refused to negotiate with threat actors behind two massive data theft campaigns impacting nearly 40 major corporations. The attackers stole billions of records using OAuth exploits and social engineering, demanding ransom under threat of public leaks. The takedown of their data leak site raises questions about law enforcement involvement in this unprecedented supply chain attack.

In a landmark decision with far-reaching implications for enterprise security, Salesforce has confirmed it will not pay ransom demands to cybercriminals responsible for one of 2025's most extensive data theft campaigns. This stance comes as threat actors linked to groups like Scattered Lapsus$ Hunters and ShinyHunters claimed possession of nearly 2.5 billion stolen records from Salesforce customers including FedEx, Disney, Google, Toyota, and Cisco.
Anatomy of a Two-Pronged Attack
The breach unfolded through two sophisticated campaigns exploiting Salesforce's ecosystem:
Social Engineering Onslaught (Late 2024): Attackers impersonated IT staff, tricking employees into connecting malicious OAuth applications to corporate Salesforce instances. This granted access to sensitive databases at companies like Adidas, Louis Vuitton, and Allianz Life.
SalesLoft Supply Chain Compromise (August 2025): Threat actors weaponized stolen SalesLoft Drift OAuth tokens to pivot into customer CRM environments. This second wave targeted technical data—credentials, API tokens, and authentication secrets—impacting security giants like Palo Alto Networks, Cloudflare, and Zscaler.
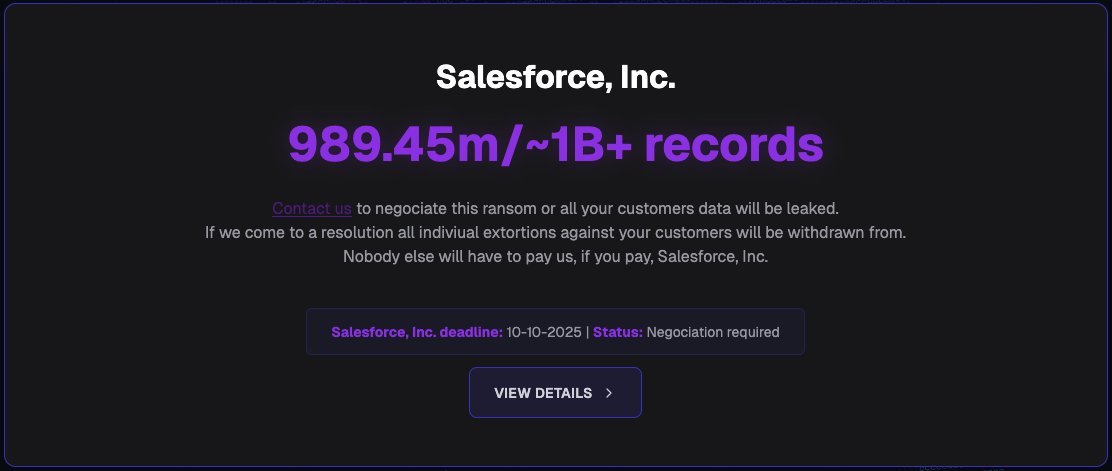 ShinyHunters' data leak site before takedown (Source: BleepingComputer)
ShinyHunters' data leak site before takedown (Source: BleepingComputer)
The Extortion Playbook
The attackers established a dedicated leak site modeled after BreachForums, threatening to release stolen data unless 39 companies paid individual ransoms or Salesforce paid a collective fee. In an email to customers, Salesforce stated:
"I can confirm Salesforce will not engage, negotiate with, or pay any extortion demand,"
citing "credible threat intelligence" about imminent data leaks. This principled refusal reflects growing industry consensus that ransom payments fuel future attacks.
Implications and Unanswered Questions
The sudden shutdown of the attackers' leak domain—now pointing to Cloudflare nameservers historically associated with FBI seizures—suggests potential law enforcement intervention. While unconfirmed, this development highlights the global stakes:
- OAuth's Expanding Attack Surface: These incidents demonstrate how compromised third-party integrations create supply chain vulnerabilities at scale
- Economic Calculus of Extortion: Salesforce's stance pressures other enterprises to adopt similar no-pay policies, potentially disrupting attacker business models
- Incident Response Precedents: The coordinated response could establish new playbooks for cross-company breach management in SaaS ecosystems
As forensic investigations continue, the incident underscores an uncomfortable truth: even cloud-native enterprises remain vulnerable when identity management systems and third-party integrations become attack vectors. The coming months will reveal whether Salesforce's refusal triggers a broader industry shift—or inspires more aggressive extortion tactics.
Source: BleepingComputer

Comments
Please log in or register to join the discussion