A zero-day vulnerability in xml-crypto and popular Node.js SAML libraries allows attackers to forge authentication responses and hijack any user account—including admins—without user interaction. WorkOS patched the flaw within 24 hours, but thousands of applications remain exposed until updated.

A critical vulnerability dubbed SAMLStorm (CVE-2025-29775/CVE-2025-29774) has exposed widespread weaknesses in Node.js SAML implementations, enabling complete authentication bypass across applications using xml-crypto and dependent libraries. Researcher Alexander Tan discovered that attackers could forge SAML assertions to impersonate any user—including administrators—without credentials or user interaction, potentially compromising organizations relying on SAML-based single sign-on (SSO).
Anatomy of an Authentication Meltdown
At its core, SAMLStorm exploits a fundamental mismatch in how xml-crypto processes XML signatures:
<DigestValue><!-- forged_digest -->legitimate_digest</DigestValue>
During validation, the library's digest check reads the first child node of <DigestValue> (the attacker's forged digest in a comment), while the signature validation uses canonicalized XML (stripping comments) and sees only the legitimate digest. This breaks SAML's cryptographic chain of trust:
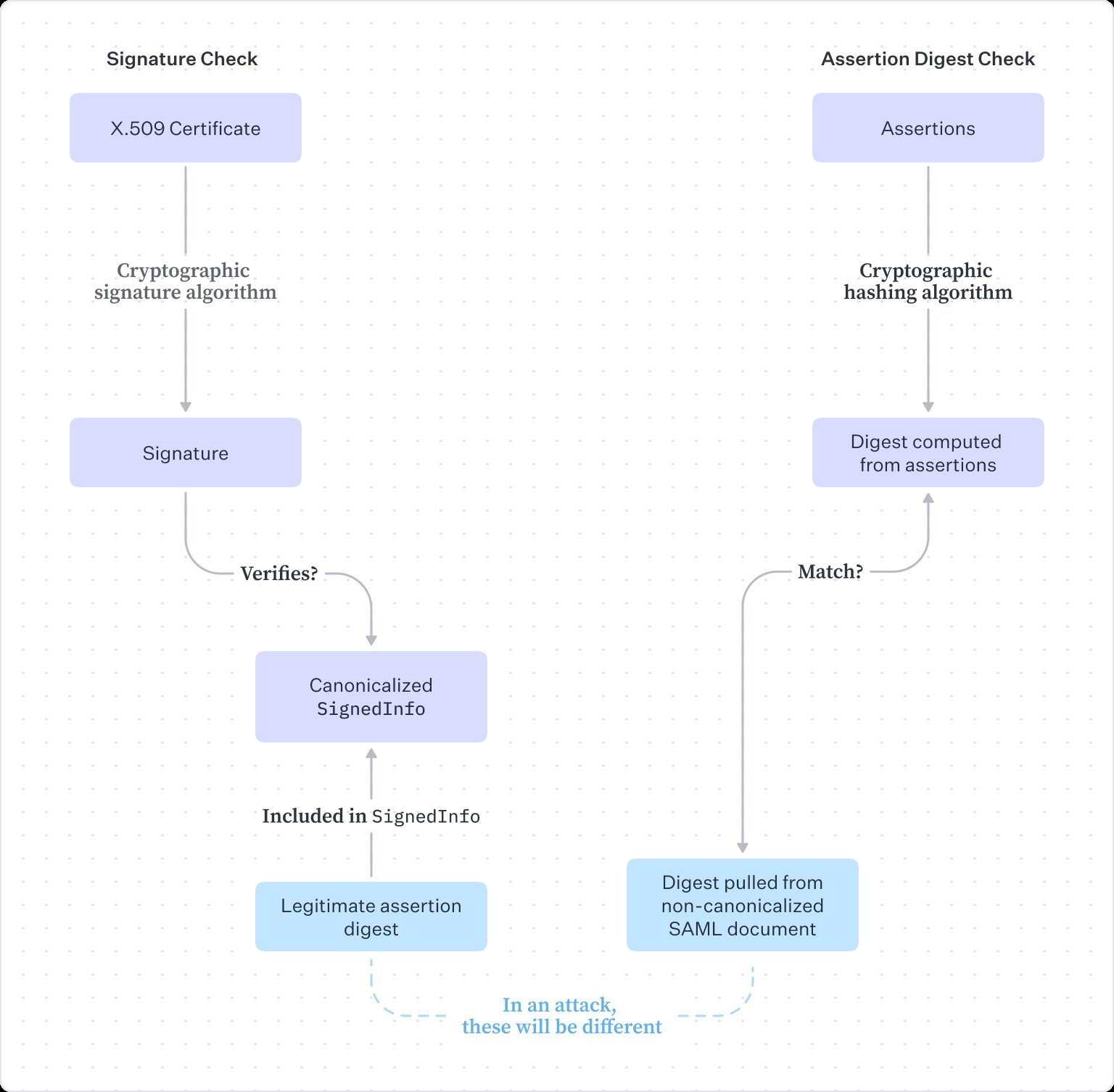 How SAMLStorm breaks the chain of trust
How SAMLStorm breaks the chain of trust
Attackers can exploit this via two primary paths:
Attack Path 1: Full Access Without an Account
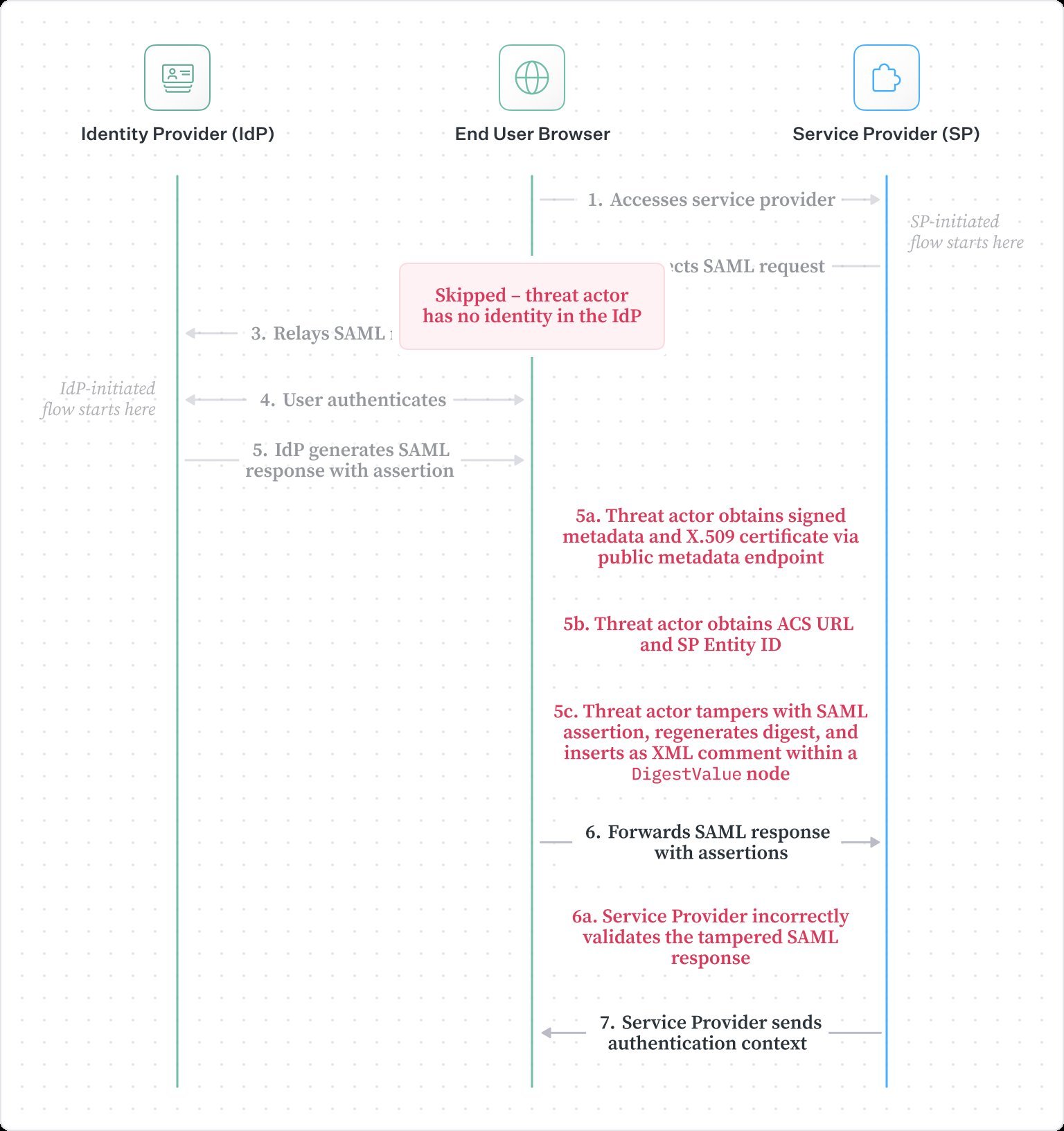
- Harvest SAML metadata from public IdPs (e.g., ACS URL, SP Entity ID)
- Craft malicious SAML response with forged assertion
- Insert recalculated digest as XML comment
- Send to service provider's ACS endpoint
Attack Path 2: Privilege Escalation
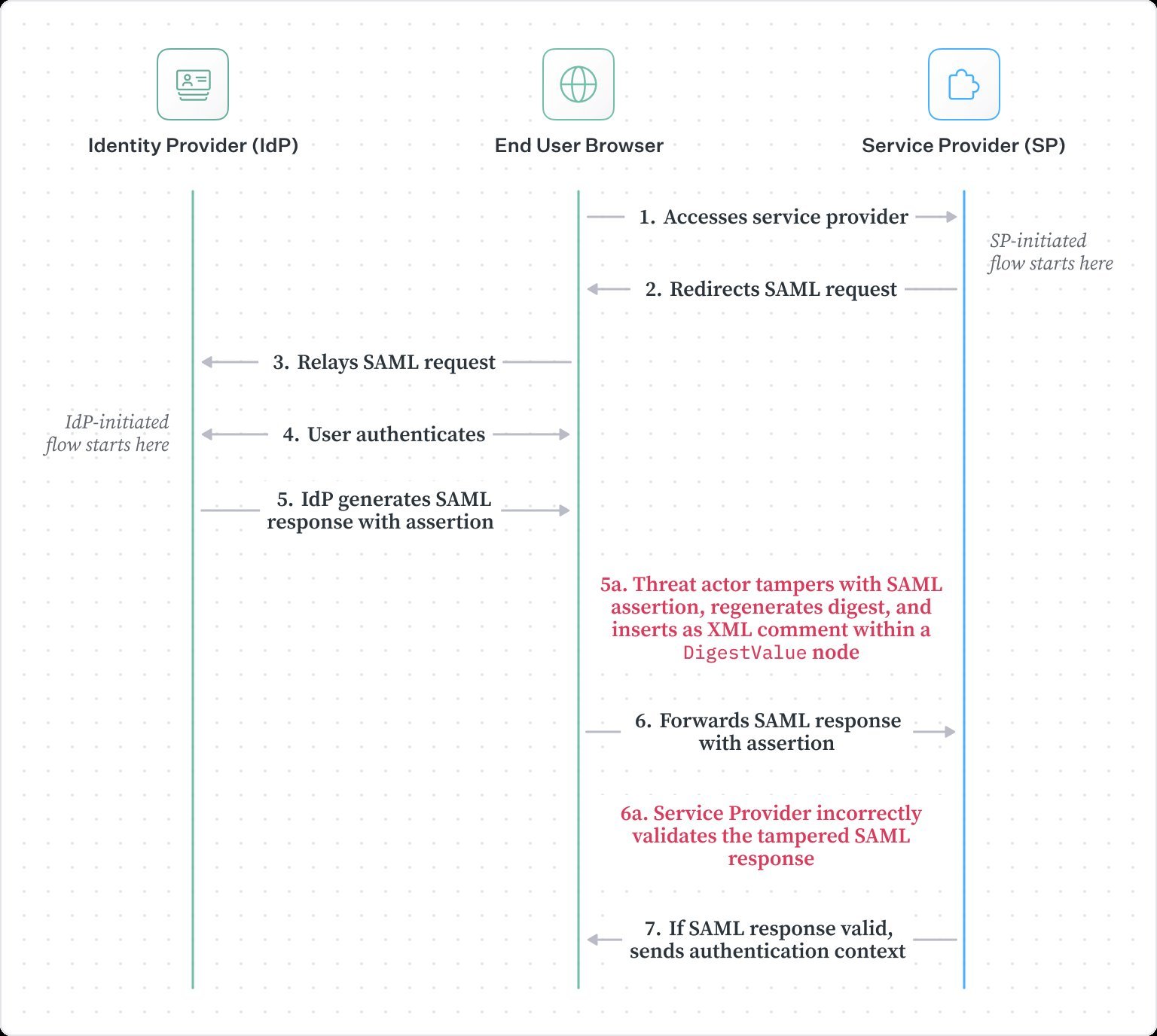
- Intercept legitimate user's SAML response
- Modify assertion attributes (e.g., elevate to admin)
- Inject new digest as comment
- Replay to service provider
Industry-Wide Impact
Affected libraries include:
xml-crypto(≤v6.0.0)@node-saml/node-samlsamlifysaml2-js
Collectively downloaded over 500,000 times weekly, these underpin authentication for countless applications. The flaw enables:
- Full account takeovers
- Cross-tenant access violations
- Privilege escalation via SAML attribute manipulation
Mitigation and Lessons Learned
WorkOS deployed patches within 24 hours of disclosure on March 4, 2025. Other organizations must:
npm update [email protected] # or patched versions
Critical actions for security teams:
- Audit SAML logs for XML comments in
<DigestValue>elements - Enforce strict XML schema validation before processing
- Implement IdP whitelisting and attribute verification
As authentication systems increasingly become attack surfaces, SAMLStorm underscores a harsh reality: Trust in cryptographic signatures is only as strong as the parser that validates them. This incident will likely catalyze long-overdue investments in hardened XML processing across the open-source ecosystem.
Source: WorkOS SAMLStorm Disclosure

Comments
Please log in or register to join the discussion