New threat intelligence reveals one actor controls 83% of attacks against critical Ivanti vulnerabilities, using bulletproof hosting and automated tools across multiple targets.
A single threat actor is responsible for the overwhelming majority of active exploitation attempts against two critical vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM), according to new threat intelligence from GreyNoise. The actor controls 83% of the exploitation activity targeting CVE-2026-21962 and CVE-2026-24061, which allow unauthenticated remote code execution on vulnerable systems.
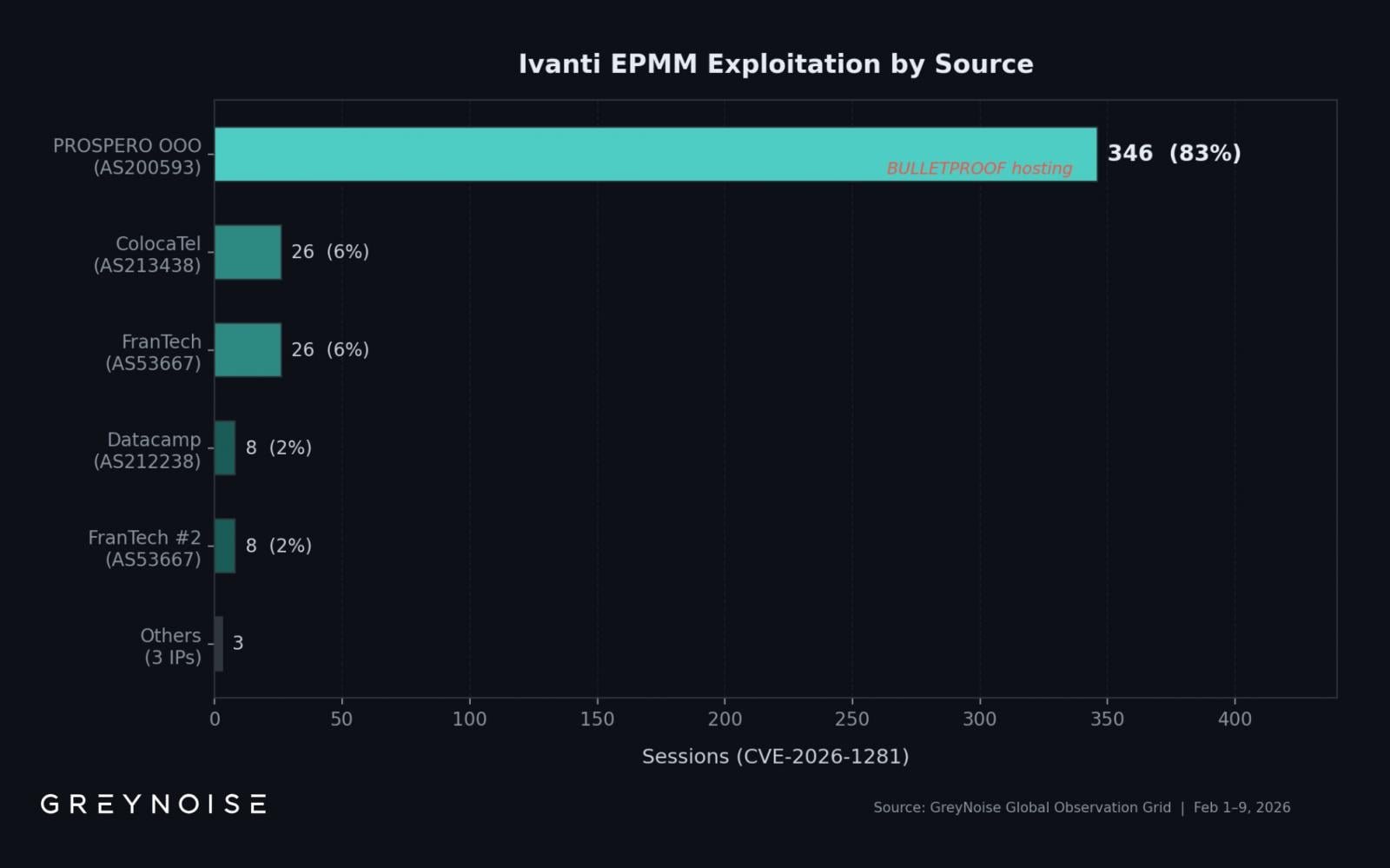
Attack source IPs Source: GreyNoise
Between February 1st and 9th, GreyNoise observed 417 exploitation sessions originating from eight unique source IP addresses. The dominant actor operates from 193.24.123.42, hosted by PROSPERO OOO (AS200593), an autonomous system that Censys analysts have identified as bulletproof infrastructure frequently used to target various software products.
The exploitation campaign shows clear signs of automation and sophistication. On February 8th alone, the monitoring platform recorded 269 exploitation sessions from this single IP address—nearly 13 times the daily average of 22 sessions. This sharp spike suggests coordinated, high-volume attack operations rather than opportunistic scanning.
Beyond Ivanti: A Multi-Target Campaign
The PROSPERO OOO infrastructure isn't limited to Ivanti targeting. The same IP address simultaneously exploited three additional vulnerabilities during the observation period:
- CVE-2026-21962 in Oracle WebLogic (2,902 sessions)
- CVE-2026-24061 in GNU Inetutils Telnetd (497 sessions)
- CVE-2025-24799 in GLPI
Oracle WebLogic exploitation dominated the actor's activity, dwarfing the other targets by volume. This pattern indicates a threat actor running a broad vulnerability exploitation platform rather than focusing on a single vendor or product.
Initial Access Broker Tactics
Of the 417 exploitation sessions targeting Ivanti vulnerabilities, 354 (85%) used OAST-style DNS callbacks to verify command execution capability. This technique is commonly associated with initial access brokers who probe for vulnerable systems before selling access to other threat actors or criminal groups.
GreyNoise researchers noted that the PROSPERO OOO IP address they observed "is not on widely published IOC lists, meaning defenders blocking only published indicators are likely missing the dominant exploitation source." This highlights a critical gap in many organizations' defensive postures, where reliance on publicly shared indicators leaves them vulnerable to the most active threat actors.
VPN Infrastructure and False Positives
Interestingly, several published indicators of compromise include IP addresses for Windscribe VPN (185.212.171.0/24), which GreyNoise telemetry shows were scanning Oracle WebLogic instances but not participating in Ivanti exploitation. This discrepancy between published IOCs and actual attack infrastructure underscores the importance of real-time threat intelligence rather than relying solely on static indicators.
Ivanti's Response and Mitigation
Ivanti has released hotfixes for the two critical vulnerabilities, but these are not permanent solutions. The company has promised complete patches with the release of EPMM version 12.8.0.0 in the first quarter of 2026.
Until then, Ivanti recommends:
- Using RPM packages 12.x.0.x for EPMM versions 12.5.0.x, 12.6.0.x, and 12.7.0.x
- Using RPM 12.x.1.x for EPMM versions 12.5.1.0 and 12.6.1.0
The vendor notes that the most conservative approach is to build a replacement EPMM instance and migrate all data there. Detailed instructions for this migration process are available in Ivanti's security advisory.
The Broader Context
This concentrated exploitation campaign reflects a growing trend in the threat landscape where sophisticated actors dominate vulnerability exploitation rather than distributing activity across many less capable groups. The use of bulletproof hosting, automation, and multi-target strategies suggests this is likely an initial access broker or a well-resourced criminal operation rather than opportunistic attackers.
Organizations running Ivanti EPMM should prioritize patching and consider the migration approach recommended by Ivanti, as the current hotfixes provide only temporary protection against what appears to be a determined and capable threat actor.

Comments
Please log in or register to join the discussion