VirusTotal's AI-powered Code Insight has uncovered a sophisticated phishing campaign hiding malicious JavaScript within seemingly benign SVG files. The attack impersonates Colombia's judicial system, delivering malware through password-protected archives that evade traditional antivirus detection. This discovery highlights both the growing threat of SVG-based attacks and AI's critical role in uncovering hidden threats.
In a striking demonstration of evolving cyber threats, VirusTotal has exposed a sophisticated phishing campaign weaponizing Scalable Vector Graphics (SVG) files to impersonate Colombia's judicial system and deliver malware. The discovery came shortly after VirusTotal expanded its AI Code Insight platform to analyze SVG files—a format traditionally considered safe for image rendering but increasingly exploited by threat actors.
The SVG Attack Vector: More Than Meets the Eye
SVG files use mathematical formulas to render crisp graphics at any scale, making them ideal for logos and illustrations. However, their ability to embed HTML via the <foreignObject> element and execute JavaScript upon loading has transformed them into potent attack vehicles. As VirusTotal noted, this functionality allows threat actors to create entirely functional phishing portals within what appears to be a simple image file.
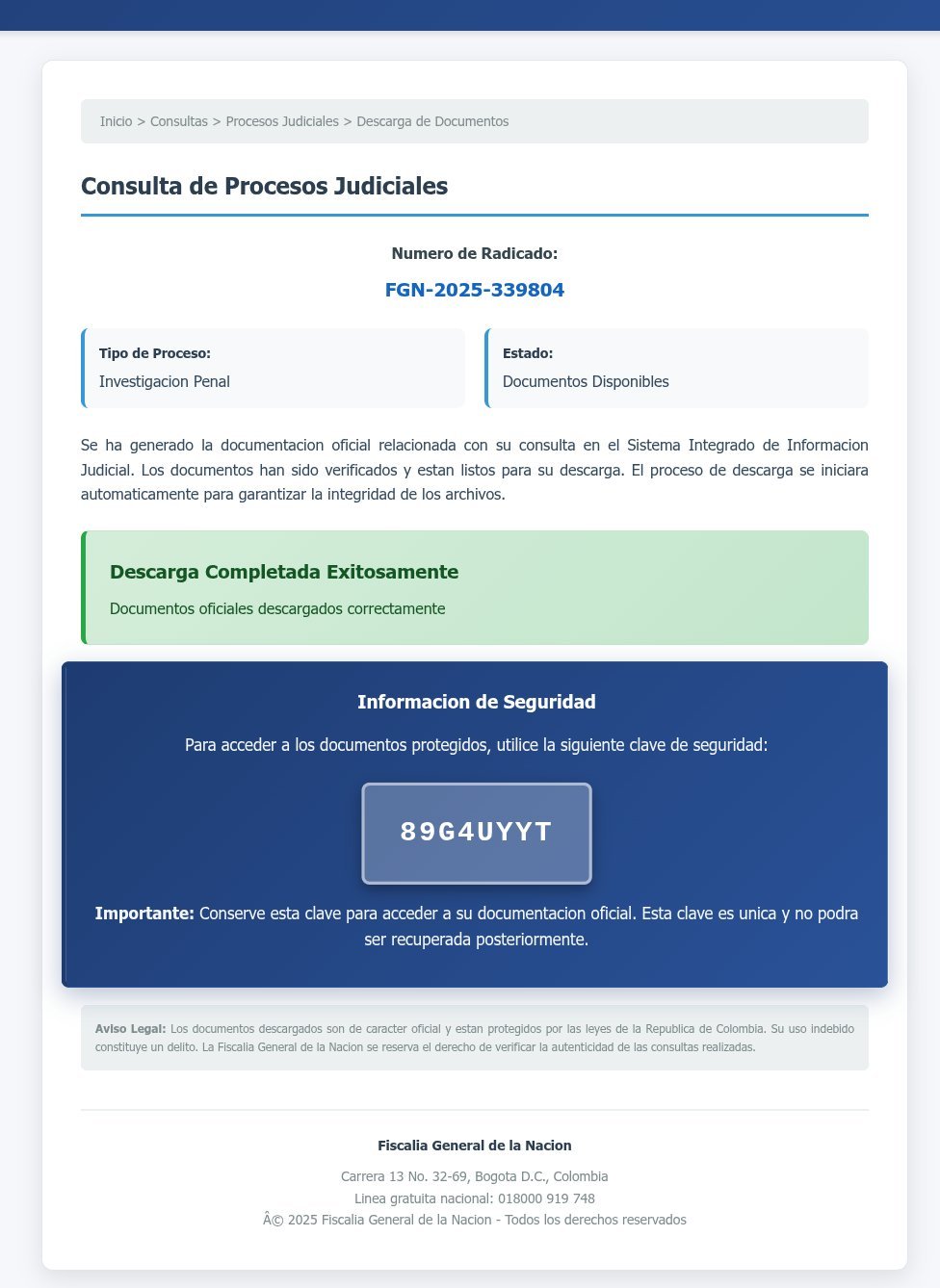 Fake judicial portal rendered entirely within an SVG file (Source: VirusTotal)
Fake judicial portal rendered entirely within an SVG file (Source: VirusTotal)
The discovered campaign used SVG files to generate convincing replicas of Colombia's judicial document portals. Victims encountered fake case numbers, security tokens, and progress bars that built false trust before prompting a download. The payload? A password-protected ZIP archive containing:
- A renamed legitimate Comodo Dragon browser executable
- A malicious DLL for sideloading
- Encrypted secondary payloads
When executed, the benign executable sideloads the malicious DLL, enabling further compromise. Critically, traditional antivirus scanners detected zero threats in the initial SVG sample.
AI Steps Where Traditional AV Fails
VirusTotal's breakthrough came through its AI Code Insight—a machine learning system that analyzes file behavior rather than relying solely on signature detection. Upon adding SVG support, the AI immediately flagged suspicious JavaScript activity in a previously overlooked file:
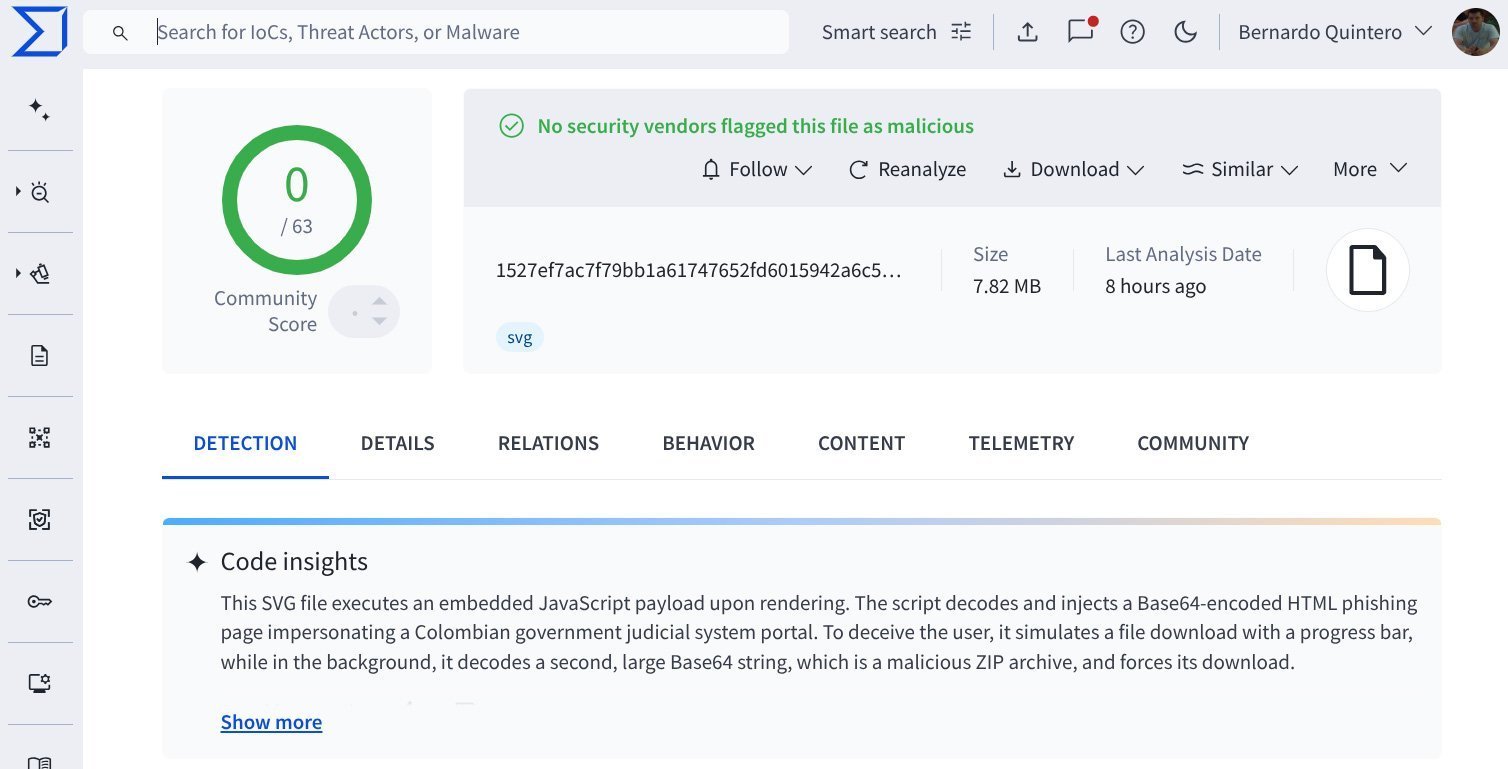 AI Code Insight exposing hidden JavaScript behavior in an SVG (Source: VirusTotal)
AI Code Insight exposing hidden JavaScript behavior in an SVG (Source: VirusTotal)
"Code Insight helps most by giving context, saving time, and helping focus on what really matters," VirusTotal emphasized. "It's not magic... but it's one more tool to cut through the noise."
The AI detection proved pivotal: VirusTotal later identified 523 related SVG files in its database—all part of the same campaign and all previously undetected by security software.
Implications: A New Frontier for Defense
This incident underscores three critical trends:
- File Format Weaponization: Attackers increasingly exploit "trusted" formats like SVG to bypass perimeter defenses
- Detection Gap: Static analysis fails against dynamic content-rendering techniques
- AI's Rising Role: Behavioral analysis through ML is becoming essential for identifying polymorphic threats
{{IMAGE:4}} Malicious payload extracted from the password-protected archive (Source: BleepingComputer)
As SVG adoption grows across web and document workflows, defenders must re-evaluate content inspection protocols. VirusTotal's discovery serves as both a warning and validation—showing how threat actors innovate while demonstrating AI's potential to illuminate the darkest corners of evolving attack surfaces. The silent war against hidden malware now increasingly depends on machines learning to interpret the intentions behind the code.
Comments
Please log in or register to join the discussion