Cybercriminals are exploiting unpatched vulnerabilities in commercial virtual private servers (VPS) to sustain the SystemBC proxy botnet, which processes massive volumes of malicious traffic for ransomware gangs and illicit services. With infected servers averaging 20 security flaws and remaining compromised for over a month, this high-stability network highlights critical gaps in cloud infrastructure security.
For years, SystemBC malware has operated in the shadows, but new research from Lumen Technology’s Black Lotus Labs reveals its staggering scale: an average of 1,500 infected virtual private servers (VPS) daily, transformed into a global proxy highway for cybercriminal traffic. This botnet, active since 2019, doesn’t just hide command-and-control communications—it fuels ransomware operations, credential theft, and black-market proxy services by exploiting servers riddled with unpatched vulnerabilities. As reported by BleepingComputer, the findings underscore a sobering reality: even commercial cloud infrastructure isn’t immune to weaponization when basic security hygiene falters.
The Anatomy of a High-Volume Threat
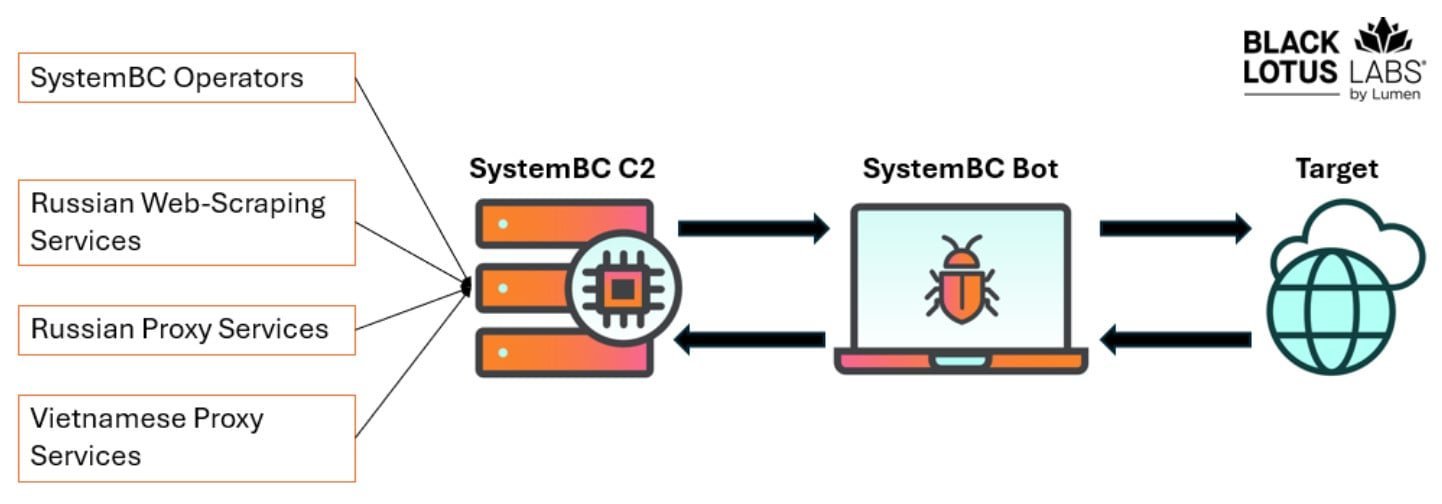
SystemBC thrives on neglect. Researchers found that nearly 80% of its botnet consists of compromised VPS systems from major providers, with infections persisting for weeks or months due to glaring security oversights. Each server averages 20 unpatched vulnerabilities, including at least one critical flaw. One egregious example in Alabama had a staggering 161 security gaps—a goldmine for attackers. Once infected, servers download a shell script (notably containing Russian-language comments) that deploys SystemBC payloads, turning them into proxies that silently relay malicious data.
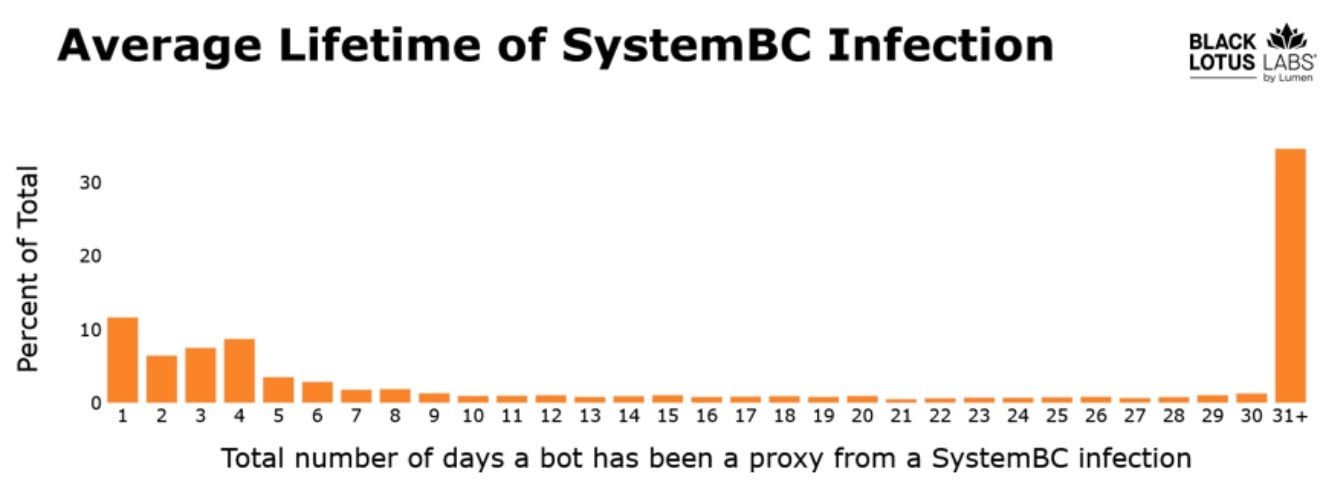
"This amount of data is an order of magnitude greater than what is commonly observed in typical proxy networks," noted Black Lotus Labs researchers, citing a test where a single IP generated over 16GB of traffic in 24 hours—far exceeding residential proxy botnets.
Criminal Ecosystem and Operational Brazenness
Unlike stealth-focused malware, SystemBC operates with alarming openness. Its operators and clients show little concern for detection, avoiding IP obfuscation while supporting services like:
- REM Proxy, which uses 80% of SystemBC bots for tiered illicit access.
- A Russian web-scraping service and Vietnam-based Shopsocks5, enabling fraud and data theft.
- Brute-force attacks on WordPress sites, where compromised credentials are sold to inject malicious code.
Why VPS Servers Are the Perfect Target
The shift from residential devices to VPS systems isn’t accidental. Commercial servers offer high bandwidth, reliability, and static IPs—ideal for stable, high-volume operations like ransomware payload delivery. This makes them more valuable than volatile SOHO-based botnets. Yet, their compromise stems from preventable issues: lax patch management and misconfigurations that attackers exploit at scale. For developers and cloud engineers, this is a wake-up call. Automated vulnerability scanning and zero-trust architectures aren’t optional; they’re essential to disrupt such threats.
Resilience Against Countermeasures
SystemBC’s endurance is chilling. It survived law enforcement operations like Operation Endgame, thanks to its decentralized C2 infrastructure—over 80 servers globally—and a core IP (104.250.164[.]214) that orchestrates new infections. Black Lotus Labs has released technical indicators of compromise to aid detection, but the malware’s longevity signals a broader trend: cybercriminals are investing in infrastructure-as-a-service models that mirror legitimate cloud economies.
As the line between enterprise and criminal tech blurs, securing VPS environments demands more than reactive fixes. It requires a cultural shift—where every unpatched server isn’t just a risk, but a potential cog in a global criminal machine. The SystemBC saga isn’t merely about malware; it’s a stark lesson in how neglected vulnerabilities become highways for chaos.
Source: Based on research by Lumen Technology’s Black Lotus Labs, as originally reported by BleepingComputer.

Comments
Please log in or register to join the discussion