Security researchers reveal that clicking disguised Telegram proxy links can expose users' real IP addresses, bypassing anonymity protections. Telegram confirms it will add warnings.

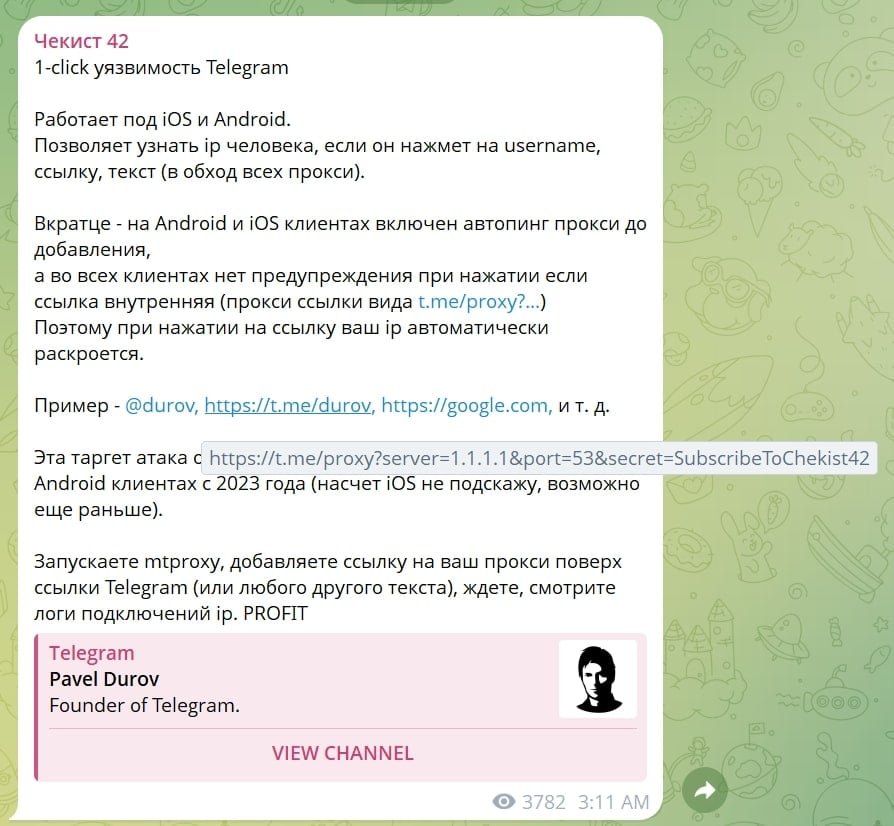
A single click on what appears to be an ordinary Telegram username or harmless link could expose your real IP address to attackers, bypassing privacy protections. This vulnerability stems from how Telegram handles proxy configuration links, potentially compromising anonymity with no additional user interaction required.
How the Exposure Works
Telegram's proxy links (t.me/proxy?server=[IP]&port=[port]&secret=[key]) are designed to help users bypass censorship by configuring MTProto proxies through a single click. When tapped in Telegram's Android or iOS apps, these links trigger an automatic connection test that bypasses existing proxies. Security researchers demonstrated that attackers can disguise these links as regular usernames (e.g., @durov) or website URLs.
"Telegram auto-pings the proxy before adding it, bypassing all configured proxies," explained the researcher who first disclosed the issue. "Your real IP is logged instantly." This occurs before users receive any proxy configuration prompt, creating a silent deanonymization risk.
Real-World Impact
Attackers hosting malicious MTProto proxies can:
- Log victims' IP addresses through connection attempts
- Determine approximate geographic locations
- Enable targeted denial-of-service attacks
- Compromise anonymity for journalists or activists in restrictive regions
As demonstrated by Telegram channel chekist42 and security researcher 0x6rss, the exploit requires minimal interaction—comparable to Windows NTLM hash leaks where a single action triggers unintended data exposure.
Telegram's Response
When contacted by BleepingComputer, Telegram downplayed the risk: "Any website or proxy owner can see the IP address of those who access it regardless of platform." However, the company confirmed plans to implement warnings for proxy links: "We're adding a warning that will show when clicking proxy links so users can be more aware of disguised links."
Telegram didn't specify a timeline for the security warning rollout. Until implemented, the current design allows IP exposure without user confirmation.
Protection Guidelines
- Verify link destinations: Hover over Telegram links to preview actual URLs before clicking
- Avoid unfamiliar proxy links: Especially those shared via unsolicited messages
- Use VPNs as primary protection: VPNs obscure IP addresses even if proxy links are triggered
- Monitor for Telegram updates: Enable automatic updates to receive the proxy warning feature
While IP exposure isn't unique to Telegram, the lack of user consent mechanisms distinguishes this risk. As noted by OSINT analysts, the exploit enables "silent and effective targeted attacks" against individuals relying on Telegram's anonymity features.
For technical details on MTProto proxy implementation, refer to Telegram's official documentation.

Comments
Please log in or register to join the discussion