As cloud applications become central to business operations, browsers have emerged as the primary attack surface for cybercriminals. This analysis breaks down six browser-based threat vectors—from evolved phishing kits to malicious OAuth exploits—driving 2025's breach epidemic. Security teams must rethink traditional defenses as attackers bypass email and endpoint controls through sophisticated browser manipulation.
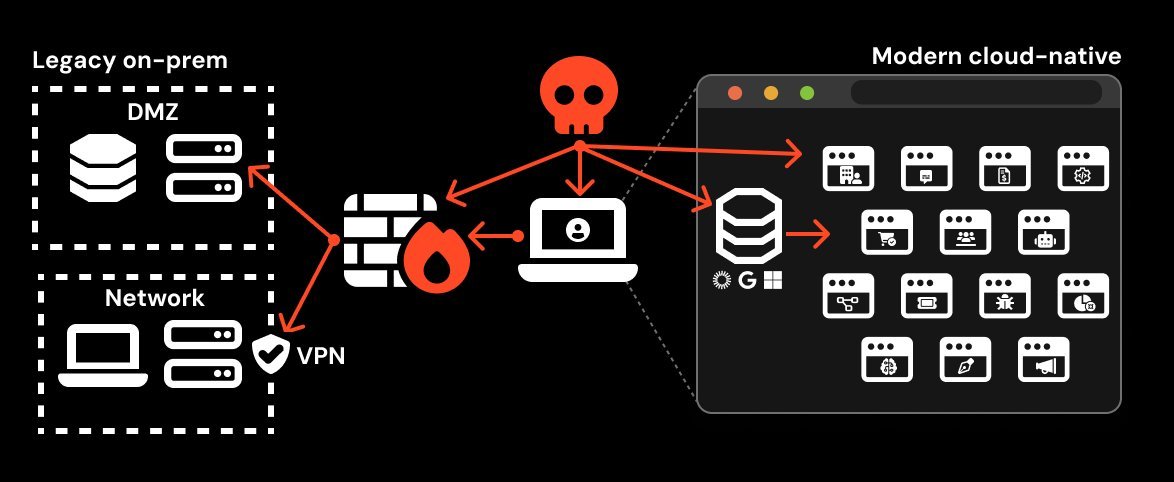
The New Frontline: Why Browsers Are the Attack Surface of Choice
"The browser is the new endpoint" isn't just industry jargon—it's the reality of modern cybersecurity. With business operations now running through SaaS applications accessed via browsers, attackers have pivoted from targeting local networks to exploiting browser vulnerabilities. As Push Security's analysis reveals, attackers compromise third-party apps (like Snowflake and Salesforce) by hijacking user sessions directly in the browser, where traditional email and endpoint defenses lack visibility.
Six Browser-Centric Threats Reshaping the Threat Landscape
- Phishing 3.0: The AitM Supremacy
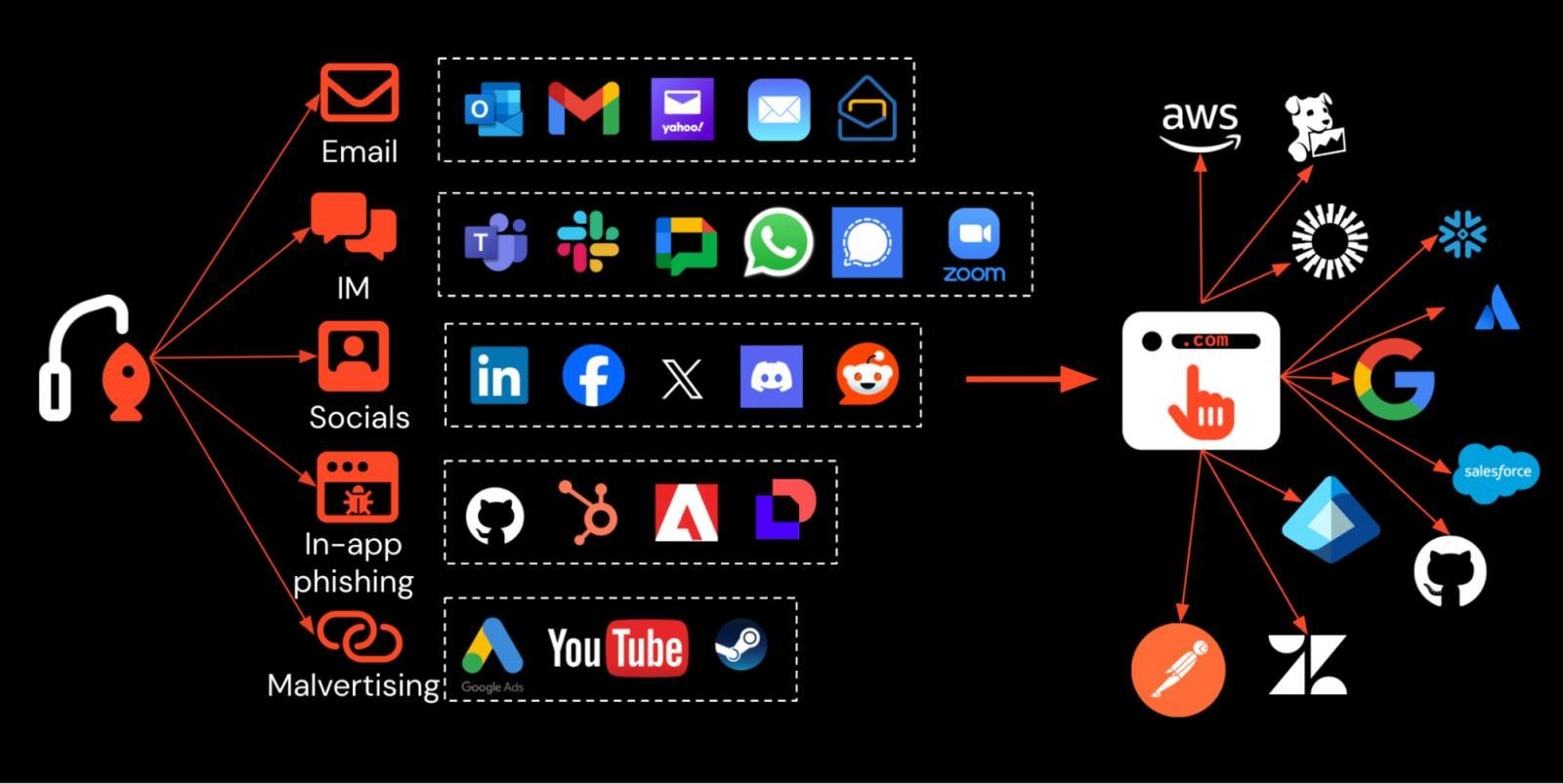
Modern phishing employs Attacker-in-the-Middle (AitM) kits that intercept sessions via reverse proxies, bypassing most MFA. These kits dynamically obfuscate code, leverage legitimate cloud services for hosting, and distribute lures across Slack, SMS, and malvertising. Legacy email security tools fail against these multi-vector attacks, which require real-time browser analysis to detect.
{{IMAGE:4}}
How AitM works: Malicious proxies relay credentials/MFA to legitimate sites while stealing sessions.
ClickFix/FileFix: The Social Engineering End-Run
Attackers trick users into executing OS commands via fake CAPTCHA or error messages. By convincing victims to paste malicious code into terminals (Windows/macOS), they deploy infostealers like Lumma Stealer. Browser-level detection of clipboard hijacking offers the last line of defense before endpoint compromise.Malicious OAuth: Bypassing Authentication Guards
Attackers weaponize OAuth integrations, tricking users into granting permissions to rogue apps. Recent Salesforce breaches exploited device code flows, where victims entered authorization codes granting attackers persistent access—sidestepping even passkeys. Browser monitoring can flag suspicious consent prompts across unmanaged SaaS apps.Trojan Extensions: The Silent Credential Harvesters
After the Cyberhaven breach (impacting 35+ extensions), malicious add-ons have surged. Attackers buy extensions or publish fake ones, requesting permissions like "read all site data" to steal sessions and passwords. Visibility into installed extensions and their permissions is critical.Weaponized Files: HTML/SVG Phishing Payloads
Malicious files delivered via ads or drive-by downloads now include HTML Applications (HTAs) and SVGs that render client-side phishing portals. These evade network proxies and sandboxes, requiring browser-level download analysis.Credential Reuse & MFA Gaps: The Low-Hanging Fruit
Stolen credentials from infostealers exploit weak MFA enforcement in SaaS apps. "Ghost logins" (local accounts bypassing SSO) remain prevalent, as seen in Snowflake attacks. Browser telemetry can identify unprotected logins in real time.
Why Traditional Defenses Are Failing
Security teams face three critical gaps:
- Visibility: Proxies and EDR can't analyze dynamically obfuscated browser content
- Scale: Hundreds of unmanaged apps create inconsistent security postures
- Control: Personal/BYOD devices lack endpoint security
As Push Security notes, detecting these threats demands observing user-browser interactions directly—analyzing page behaviors, clipboard access, OAuth grants, and extension permissions. The era of relying solely on network or email security is over; 2025's survival hinges on browser-centric defense.
Source: BleepingComputer (Sponsored by Push Security)

Comments
Please log in or register to join the discussion