A security researcher reveals how commit messages containing code diffs can be accidentally executed when applying patches, leading to potential vulnerabilities in software projects.
In a startling revelation that has sent ripples through the software development community, Michael Stapelberg has uncovered a dangerous vulnerability in how version control systems handle commit messages. The issue, which he describes as a serious security concern, demonstrates how seemingly innocuous commit messages can become vectors for malicious code execution.
The Core Problem
The fundamental issue lies in how patch tools like patch(1) and git-am(1) process input. These tools are designed to apply unified context diffs to source code, but they contain a critical flaw: they will execute any code that appears to be a valid patch, regardless of where it appears in the input stream. This means that if a commit message contains a properly formatted diff, the patch tool will attempt to apply it as if it were actual code.
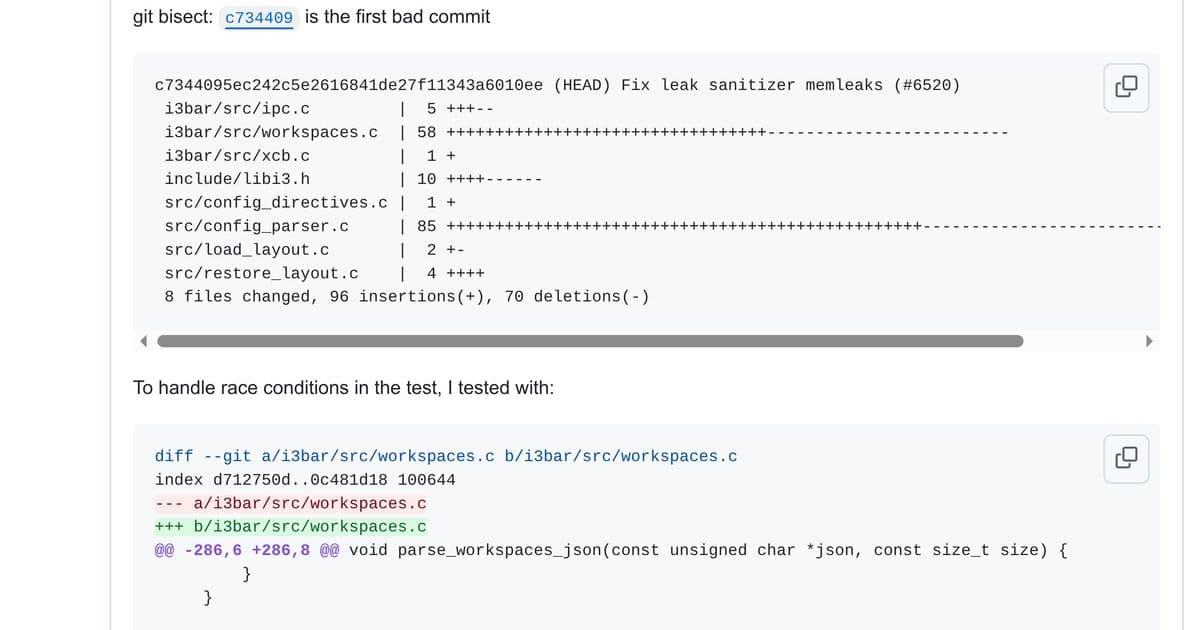
Stapelberg provides a concrete example from the i3 window manager project, where a sleep(1) command was inadvertently introduced into the codebase through this exact mechanism. The problematic commit, available at github.com/i3/i3/pull/6564, demonstrates how a code diff embedded in a commit message was applied during the patch process, resulting in unintended behavior.
How It Works
The vulnerability exploits the way unified diff format works. When tools like git format-patch generate patch files, they include the commit message followed by the actual diff. However, the patch tool doesn't distinguish between "metadata" and "actual patch content" - it simply looks for anything that matches the diff pattern and applies it.
This becomes particularly dangerous because:
- No Validation: The patch tool doesn't validate whether the diff should logically be applied at that point
- Automatic Application: Tools like
git-amautomatically process the entire input, including commit messages - Format Ambiguity: The diff format doesn't provide clear boundaries between different types of content
Real-World Impact
The consequences of this vulnerability extend far beyond theoretical concerns. As Stapelberg notes, this is how a sleep(1) command made its way into i3 version 4.25-2 in Debian unstable. While this particular instance may have been accidental, the same mechanism could be exploited intentionally to introduce malicious code into software projects.
Community Response
The discovery has sparked intense discussion within the developer community. Several key perspectives have emerged:
Tool Design Issues: Many developers point out that this is fundamentally a design flaw in how patch tools handle input. The current approach of treating any valid diff as executable code, regardless of context, creates an inherent security risk.
Git vs GitHub: Some initially blamed GitHub for the issue, but further investigation revealed that this is a problem with git itself. GitHub's patch generation follows the same patterns as standard git tools, meaning the vulnerability exists regardless of the platform used.
Historical Context: Experienced developers noted that this isn't the first time such issues have occurred. Similar problems have been documented in Debian bug reports, though often with less severe consequences.
Technical Analysis
Several developers have provided deeper technical analysis of the problem:
Format Limitations: The unified diff format was designed for a specific purpose - describing changes between file versions. It wasn't designed to handle arbitrary text content, yet it's being used in contexts where such content is common (like commit messages).
In-Band Signaling: The core issue is what security experts call "in-band signaling" - using the same channel for both control information and data. This creates ambiguity that can be exploited.
Tool Chain Dependencies: The problem cascades through the tool chain. git format-patch generates patches that include commit messages, git-am processes these patches, and patch applies whatever it finds, creating multiple opportunities for exploitation.
Potential Solutions
Developers have proposed several approaches to mitigate this vulnerability:
Content Escaping: One suggestion is for git tools to properly escape commit messages when generating patches, using mechanisms like leading spaces to indicate "garbage" data that shouldn't be processed.
Format Separation: Another approach would be to use MIME multipart/mixed format to clearly separate the commit message from the actual patch data, eliminating ambiguity.
Tool Behavior Changes: Some argue that patch tools should be more conservative in what they apply, perhaps requiring explicit markers or validation before processing any diff content.
Broader Implications
This vulnerability highlights several important lessons for software development:
Tool Chain Security: Even well-established tools can contain serious security flaws that go unnoticed for years. The fact that this issue persisted for decades through countless commits and repositories demonstrates the need for continuous security review.
Format Design: The incident underscores the importance of designing data formats with security in mind. Formats that allow ambiguous interpretation create opportunities for exploitation.
Development Practices: The vulnerability suggests that development workflows may need to be adjusted to account for these risks, particularly when dealing with external contributions or automated patch application.
Moving Forward
The discovery has already prompted action within the git community. Michael Stapelberg reported the issue to the git mailing list, and developers are discussing potential fixes. However, given the widespread use of these tools and the potential for breaking existing workflows, any changes will need to be carefully considered.
In the meantime, developers are advised to exercise caution when applying patches, particularly from untrusted sources. The incident serves as a reminder that even fundamental development tools can harbor hidden dangers, and vigilance is essential in maintaining software security.
The revelation about commit message vulnerabilities represents a significant moment in software security awareness. It demonstrates how seemingly minor design decisions can have far-reaching security implications, and highlights the ongoing need for security-conscious development practices in all aspects of software engineering.
Comments
Please log in or register to join the discussion