A deep dive into KineMaster's surprisingly simple approach to detecting cracked clients reveals how even major apps can implement effective DRM with minimal effort.
When it comes to protecting digital content from piracy, developers often face a difficult choice: invest significant resources in sophisticated anti-tampering measures, or accept that some level of piracy is inevitable. However, a recent examination of KineMaster's backend source code reveals that sometimes the simplest solutions can be surprisingly effective.

KineMaster, once the go-to video editing app for mobile devices (before being largely replaced by CapCut), faced the same challenge as many freemium apps: how to prevent users from enjoying premium features without paying. The app was notorious for its watermark on exported videos and various in-app purchases, making it a prime target for modders and crackers.
Most developers would reach for sophisticated solutions like Google's Play Integrity API (formerly SafetyNet) or implement heavy obfuscation frameworks to deter tampering. These approaches require significant development effort and ongoing maintenance to stay ahead of determined attackers. But what if there was an easier way?
As it turns out, KineMaster discovered a remarkably simple approach that required virtually no additional security infrastructure. The key insight? Modders are rarely subtle about their modifications.
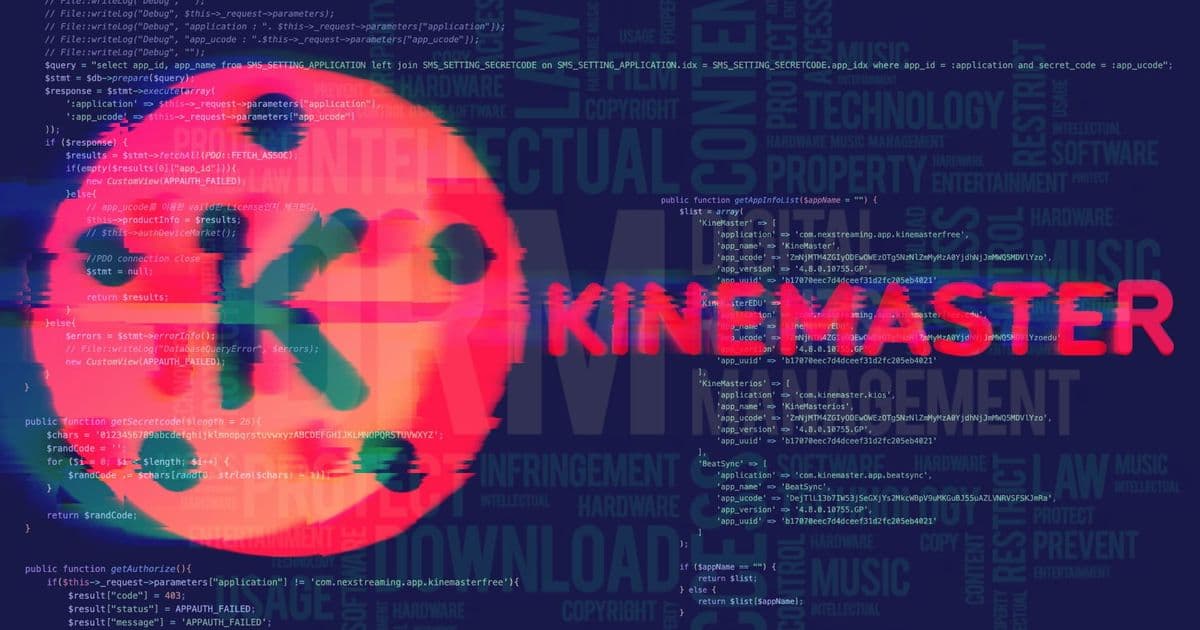
When examining the leaked source code, one particular function stands out for its elegant simplicity. The authentication system for KineMaster's asset store included a basic version check that compared the client's reported app version and name against a hardcoded list of known modded versions.
The implementation is straightforward: when a client attempts to authenticate with the asset store, it sends along its version number and application name. The server then checks these values against a list of known modded versions. If there's a match, access is denied with a simple 403 Forbidden response.
What makes this approach particularly clever is that it exploits a fundamental weakness in how most modders operate. Rather than trying to hide their modifications, many proudly display their names in the app's version string or application name. Names like "Mod V5," "Modded By Agoez Clemod," "KineMaster Pro Mod [AmanZz]," and "KineMaster Indonesia" are all explicitly blocked in the code.
This creates a fascinating dynamic in the cat-and-mouse game between developers and crackers. The very act of creating and distributing a mod often reveals its identity to the very systems it's trying to bypass. It's akin to a burglar wearing a name tag while attempting to break into a building.
The code snippet reveals a list of approximately 20 different modded versions that are explicitly blocked. Each entry requires both the version string and application name to match, though the reasoning behind this dual requirement isn't entirely clear from the available source code.
From a security perspective, this approach has several advantages:
First, it requires virtually no additional infrastructure. No complex encryption, no attestation APIs, no obfuscation frameworks. Just a simple conditional check against a list of strings.
Second, it's incredibly easy to maintain. When new modded versions appear, they can be added to the list with minimal effort. The server-side nature of the check means that updates can be deployed instantly without requiring users to update their apps.
Third, it's surprisingly effective against the majority of modded clients. Since most modders don't bother to change the default behavior of sending version and name information, they inadvertently reveal their identity to the server.
However, this approach isn't without its limitations. Sophisticated attackers could potentially bypass this check by modifying the client to send fake version information that mimics legitimate app versions. The source code suggests that some modders have indeed found ways to authenticate by faking license information, though the specifics aren't fully detailed in the available code.
A more robust implementation might store the list of blocked versions in a database rather than hardcoding them, allowing for easier updates and potentially more sophisticated matching algorithms. But even in its current form, the approach demonstrates how sometimes the simplest solutions can be remarkably effective.
The KineMaster case study offers several valuable lessons for developers facing similar challenges:
Leverage existing data flows: Rather than implementing entirely new security measures, look at what information your application already sends and see if it can be repurposed for security checks.
Exploit attacker behavior: Understanding how attackers typically operate can reveal simple vulnerabilities you can exploit. In this case, the tendency of modders to be obvious about their modifications became a security feature.
Server-side validation is powerful: By moving validation logic to the server, you can update security measures without requiring client updates, making it much harder for attackers to keep up.
Sometimes simple is better: Complex security measures can be expensive to implement and maintain. A simple solution that catches 80% of attackers might be more cost-effective than a complex one that catches 95%.
This approach also highlights an important reality in software security: perfect security is often impossible, but good enough security can be remarkably simple. KineMaster's solution won't stop the most determined attackers, but it provides a low-cost barrier that catches the majority of casual piracy attempts.
The broader implications extend beyond just video editing apps. Any application that communicates with a backend server and sends version information could potentially implement similar checks. This includes everything from mobile games to productivity apps to streaming services.
As the battle between developers and crackers continues to evolve, approaches like KineMaster's demonstrate that sometimes the most effective solutions aren't the most sophisticated ones. By understanding attacker behavior and leveraging existing data flows, developers can implement surprisingly effective anti-piracy measures with minimal additional effort.
The lesson here isn't that developers should abandon sophisticated security measures entirely, but rather that they should consider whether simpler solutions might be sufficient for their needs. In a world where development resources are always limited, the ability to implement effective security measures quickly and cheaply is a valuable skill.
For developers facing similar challenges, KineMaster's approach offers a compelling template: look at what information you're already collecting, consider how attackers typically behave, and ask whether a simple server-side check might be enough to solve your problem. Sometimes, the laziest solution is also the smartest one.
Comments
Please log in or register to join the discussion