A newly patched heap-based buffer overflow (CVE-2025-53149) in Windows' Kernel Streaming WOW Thunk Service (ksthunk.sys) could enable kernel memory corruption. Discovered by Crowdfense researchers, the flaw highlights persistent risks in driver-level code handling legacy compatibility layers.
The Hidden Danger in Windows' Multimedia Backbone
Buried within Windows' multimedia infrastructure lies a critical vulnerability that could enable kernel memory corruption. CVE-2025-53149, a heap-based buffer overflow in the Kernel Streaming WOW Thunk Service Driver (ksthunk.sys), was patched by Microsoft in August 2025 after discovery by Crowdfense researchers. This driver facilitates crucial 32/64-bit compatibility for real-time multimedia streams – a legacy requirement still relevant for specialized hardware.

Anatomy of the Flaw
The vulnerability resides in CKSAutomationThunk::HandleArrayProperty(), triggered when handling KSPROPERTY_VPCONFIG_DDRAWSURFACEHANDLE requests. Researchers found that when processing property "get" operations:
// Simplified vulnerable logic
NTSTATUS HandleArrayProperty(...) {
ULONG BytesReturned;
KsSynchronousIoControlDevice(..., &BytesReturned); // Query needed size
PVOID TempBuffer = ExAllocatePool(NonPagedPool, BytesReturned);
KsSynchronousIoControlDevice(..., TempBuffer); // Retrieve data
// Critical flaw: No bounds check before copy
for (int i=0; i<elementCount; i++) {
SystemOutputBuffer[i] = TempBuffer[i]; // Heap overflow occurs here
}
}
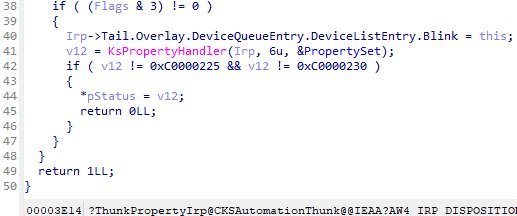
The vulnerable loop lacking proper bounds validation (Source: Crowdfense)
As Crowdfense noted: "OutputBufferLength is not correctly checked against BytesReturned... enabling a non-paged heap overflow." This could allow attackers to corrupt adjacent kernel memory structures if successfully exploited.
Exploitation Constraints and Significance
Triggering requires specific hardware:
- A device supporting
KSPROPSETID_VPConfigorKSPROPSETID_VPVBIConfig - With the
KSPROPERTY_VPCONFIG_DDRAWSURFACEHANDLEproperty
"While we couldn't find vulnerable devices in our test environments, systems with specialized multimedia hardware—particularly legacy capture cards or broadcast equipment—are potentially at risk," the researchers cautioned.
Microsoft's patch introduced a critical bounds check:
if (OutputBufferLength < RequiredSize) {
RtlLogUnexpectedCodepath(); // Triggers crash to prevent overflow
}
The Bigger Picture: Driver Security Matters
This vulnerability underscores enduring challenges:
- Legacy Code Risks: Thunk layers bridging 32/64-bit environments remain fertile ground for flaws
- Hardware-Specific Threats: Vulnerabilities tied to niche hardware often linger undetected
- Defense Depth: Kernel heap overflows remain valuable exploit primitives for privilege escalation
The disclosure timeline reveals vendor friction—Microsoft awarded then rejected Crowdfense's bounty claim, highlighting ongoing tensions in vulnerability disclosure economics.
As Windows continues supporting legacy multimedia stacks through components like KSThunk, rigorous driver auditing remains non-negotiable for enterprises handling sensitive media workflows. This patch closes one door, but the architectural complexity ensuring backwards compatibility ensures others likely remain.
Source: Crowdfense Technical Disclosure

Comments
Please log in or register to join the discussion