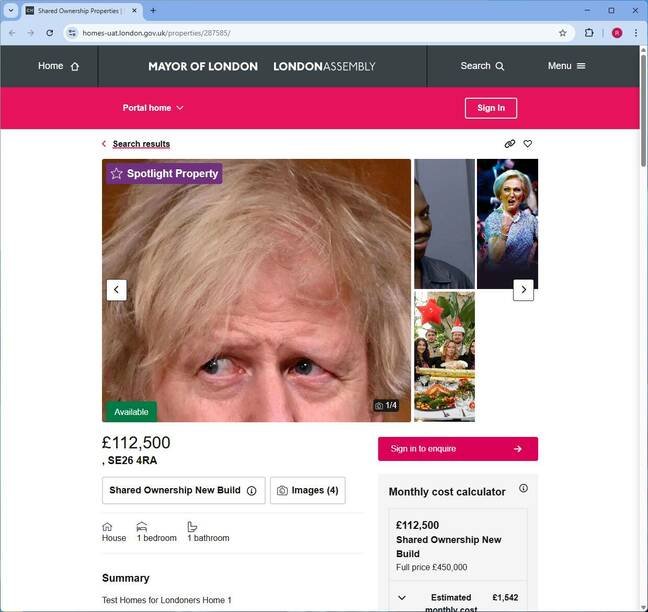
A London government website for affordable housing accidentally published its user acceptance testing environment, revealing placeholder content filled with internet memes and repetitive text instead of legitimate property listings.

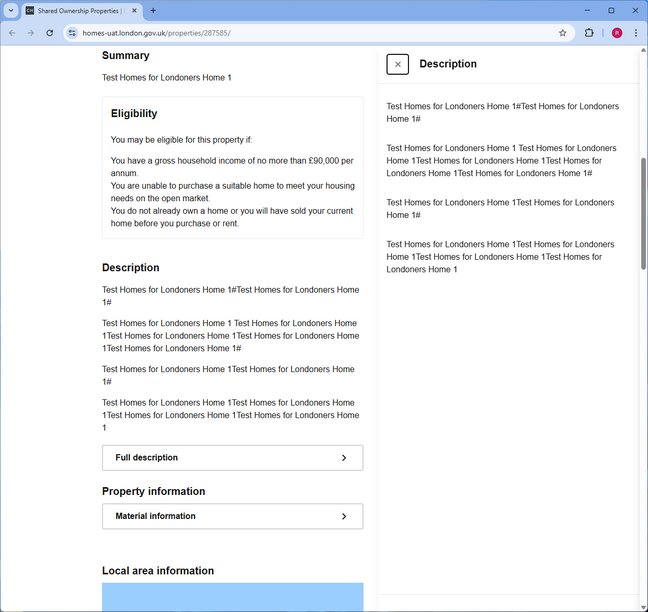
The Greater London Authority's affordable housing portal intended to help residents find below-market-rate properties instead became an unintentional showcase of developer humor when its user acceptance testing (UAT) environment became publicly accessible. Visiting homes-uat.london.gov.uk revealed placeholder listings populated with viral memes including a disheveled Boris Johnson, the 'tapping head' meme character, and festive holiday imagery - all accompanied by repetitive "Test Homes for Londoners Home 1" descriptions.
This exposure highlights critical oversights in environment management protocols. UAT environments typically mirror production infrastructure but contain synthetic datasets for final verification before public release. Best practice dictates these staging areas should be isolated behind authentication barriers or restricted IP access controls. The public exposure suggests either misconfigured network rules or inadequate deployment pipeline safeguards.
From a technical perspective, such environment leaks create multiple problems:
Resource Consumption: Publicly accessible UAT environments waste computational resources serving non-production traffic. Each visitor request consumes CPU cycles and bandwidth that should be reserved for legitimate testing.
Security Vulnerabilities: Exposed test environments often contain weaker security configurations than production systems, potentially providing attack vectors. Database connection strings, internal API endpoints, or debugging interfaces frequently remain enabled in UAT.
Data Integrity Risks: While this instance used harmless memes, test environments sometimes contain scrambled production data derivatives. Proper data sanitation protocols must be enforced to prevent potential GDPR violations.
Environment isolation checklist for development teams:
- Implement network-level separation between prod/non-prod environments
- Enforce mandatory authentication for all staging/UAT systems
- Automate environment audits with infrastructure-as-code tools
- Use DNS subdomains clearly labeled (e.g., uat.site.com)
- Schedule regular credential rotation for test environments
The incident underscores how easily development artifacts can surface publicly when environment management processes lack rigor. While no sensitive data was compromised here, the meme-filled placeholder content damages institutional credibility for a service addressing London's critical housing shortage. As of publication, the Mayor's office hasn't commented on remediation timelines or process changes.
For infrastructure teams, this serves as a reminder to validate environment access controls with the same rigor applied to performance benchmarks. Production-grade security shouldn't be an afterthought relegated only to live systems.

Comments
Please log in or register to join the discussion