A critical AWS CodeBuild misconfiguration could have allowed attackers to compromise AWS's own GitHub repositories including the JavaScript SDK, putting millions of environments at risk.
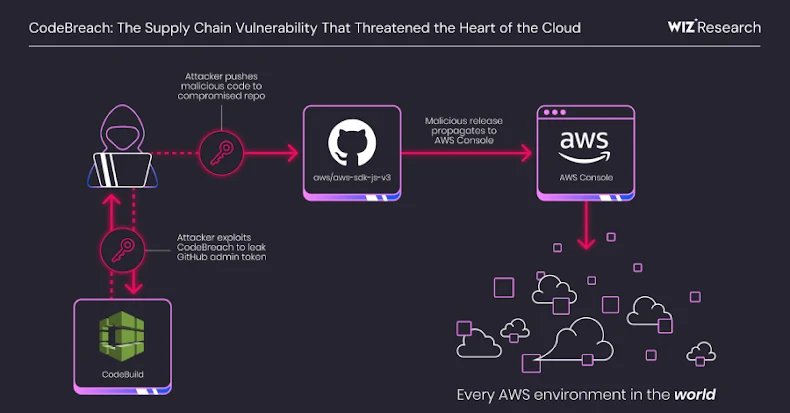
A critical misconfiguration in AWS CodeBuild could have enabled attackers to seize control of AWS's core GitHub repositories, including the widely used JavaScript SDK, potentially compromising millions of cloud environments. Dubbed CodeBreach by cloud security firm Wiz, this vulnerability represented a severe supply chain threat until AWS patched it in September 2025 following responsible disclosure.
According to Wiz researchers Yuval Avrahami and Nir Ohfeld, "By exploiting CodeBreach, attackers could have injected malicious code to launch a platform-wide compromise, potentially affecting not just the countless applications depending on the SDK, but the Console itself, threatening every AWS account."
The vulnerability stemmed from inadequate webhook filters in AWS CodeBuild's continuous integration pipelines. These filters, designed to restrict build triggers to trusted GitHub accounts, failed to implement proper regex anchoring (^ and $ characters) in four critical repositories:
This regex flaw allowed attackers to bypass protections by generating GitHub bot accounts with sequential IDs that contained trusted maintainer IDs as substrings. Wiz demonstrated how attackers could predict new 9-digit GitHub IDs that would eclipse trusted 6-digit IDs approximately every five days. By automating bot creation through GitHub Apps, attackers could generate IDs like 226755743 (containing the trusted 755743) to trigger unauthorized builds.
Successful exploitation would leak privileged GitHub tokens, including a Personal Access Token with admin rights to the aws-sdk-js-v3 repository. This would enable attackers to push malicious code directly to the main branch, approve pull requests, and exfiltrate secrets - creating a pathway for widespread supply chain compromise.
AWS confirmed in an advisory: "These were project-specific misconfigurations in webhook actor ID filters... not an issue in the CodeBuild service itself." The cloud provider implemented credential rotations and build process hardening, noting no evidence of in-the-wild exploitation.
Critical Mitigation Steps
Organizations should implement these measures to prevent similar CI/CD compromises:
- Enable Pull Request Comment Approval build gates to prevent untrusted contributions from triggering privileged pipelines
- Use CodeBuild-hosted runners for GitHub workflow triggers
- Anchor all regex patterns in webhook filters (e.g.,
^123456$instead of123456) - Generate unique, minimally-scoped Personal Access Tokens per CodeBuild project
- Employ dedicated unprivileged GitHub accounts for CodeBuild integration
This incident highlights broader CI/CD security challenges. Recent research from Sysdig and Orca Security revealed similar risks in GitHub Actions' pull_request_target trigger, dubbed "pull_request_nightmare," affecting major tech companies. As Wiz researchers noted, "This vulnerability exemplifies why adversaries target CI/CD environments: a subtle, easily overlooked flaw that can be exploited for massive impact."
Security teams should audit their CI/CD pipelines for:
- Overprivileged credentials in build environments
- Insufficient input validation in automation triggers
- Unanchored regex patterns in security filters
- Exposure of secrets during build processes
Regular pipeline reviews and principle of least privilege implementation remain critical defenses against evolving supply chain threats.

Comments
Please log in or register to join the discussion