A seemingly simple Azure PostgreSQL Flexible Server deployment fails with 'Internal error' when VNets and Private DNS zones span multiple subscriptions, revealing a critical requirement for cross-subscription resource provider registration.
When deploying Azure Database for PostgreSQL – Flexible Server with private networking, enterprise customers often encounter a frustrating scenario: the deployment fails with a generic "Internal error" message, despite seemingly correct configuration of VNet injection, subnet delegation, and Private DNS zones. This issue, recently documented in a Microsoft Community Hub post, reveals a critical but often overlooked requirement in Azure's cross-subscription networking architecture.
The Hidden Dependency in Cross-Subscription Deployments
The case study involves a customer attempting to deploy PostgreSQL Flexible Server using private networking. Everything appeared correctly configured: the VNet was properly peered, subnet delegation was in place, and the Private DNS zone existed. Permissions seemed sufficient. Yet, the deployment consistently failed with that maddeningly vague "Internal error."
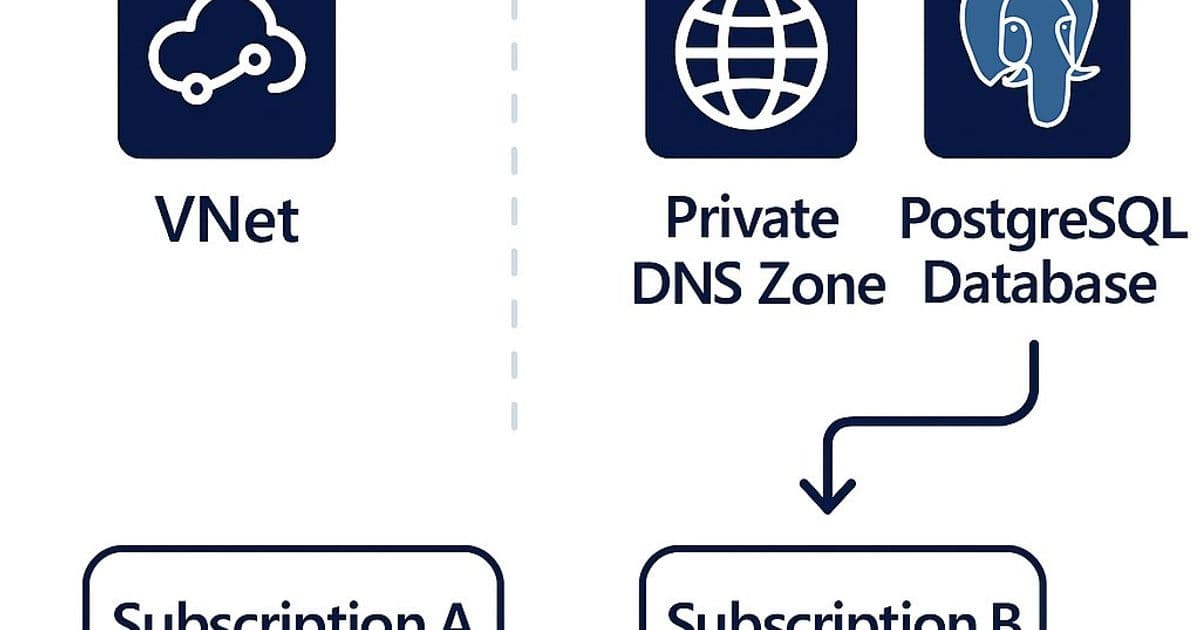
The root cause was unexpected: the Virtual Network and Private DNS zone were hosted in a different subscription than the PostgreSQL server. While the PostgreSQL subscription had Microsoft.DBforPostgreSQL registered, the subscription hosting the VNet and Private DNS zone did NOT.
This reveals a fundamental principle in Azure's architecture: cross-subscription networking for Azure PostgreSQL Flexible Server is not passive. Azure actively validates resource providers in all referenced subscriptions, not just where the PostgreSQL server lives.
Why This Matters for Enterprise Architecture
This requirement has significant implications for enterprise cloud architecture patterns. Many organizations follow a hub-and-spoke model where:
- A central networking subscription hosts shared VNets and Private DNS zones
- Application teams have separate subscriptions for their resources
- Central IT manages networking infrastructure
In this common pattern, the PostgreSQL deployment fails silently because Azure cannot validate the resource provider registration across subscription boundaries. The error message provides no indication of this dependency, leading to hours of troubleshooting.
The Technical Mechanics
Azure's validation process works as follows:
- When deploying PostgreSQL Flexible Server with VNet injection, Azure identifies all cross-subscription dependencies
- It checks for the Microsoft.DBforPostgreSQL resource provider registration in each referenced subscription
- If any referenced subscription lacks this registration, the deployment fails
- The failure occurs before any networking validation, resulting in the generic error
This behavior ensures that Azure can properly orchestrate resources across subscription boundaries, but it creates a hidden dependency that's not immediately obvious from the documentation or portal experience.
Resolution and Prevention
The solution is straightforward once identified: register Microsoft.DBforPostgreSQL in every subscription involved in the deployment. The customer's deployment succeeded immediately after this registration, with no other changes required.
For prevention, organizations should:
Pre-deployment validation: Before any private PostgreSQL deployment, verify resource provider registration across all involved subscriptions
Documentation: Include cross-subscription resource provider requirements in landing zone documentation
Automation: Incorporate resource provider validation into Infrastructure as Code (IaC) pipelines, ARM templates, or Bicep deployments
Centralized management: Consider registering commonly used resource providers in networking subscriptions during initial setup
Step-by-Step Troubleshooting Guide
For teams encountering this issue, follow this systematic approach:
Step 1: Identify Cross-Subscription Dependencies
- Determine if the VNet is in a different subscription than the PostgreSQL server
- Check if the Private DNS zone is in yet another subscription
- Map all subscription boundaries involved in the deployment
Step 2: Validate Resource Provider Registration
- Navigate to each subscription in the Azure Portal
- Go to "Resource providers" in the left navigation
- Search for "Microsoft.DBforPostgreSQL"
- If status shows "NotRegistered," click "Register"
- Wait for the registration to complete (may take several minutes)
Step 3: Retry Deployment
- After registration completes in all subscriptions
- Re-run the PostgreSQL Flexible Server deployment
- The internal error should no longer occur
Broader Implications for Azure Architecture
This issue highlights several important considerations for Azure architecture:
Resource provider registration is a cross-subscription concern: Many Azure services have similar cross-subscription dependencies that aren't well-documented
Error messaging needs improvement: Generic "Internal error" messages obscure the real issue and waste significant troubleshooting time
Centralized networking patterns require careful planning: Hub-and-spoke architectures must account for resource provider registration in central networking subscriptions
Automation becomes essential: Manual validation across subscriptions is error-prone; automation should enforce these prerequisites
Best Practices for Enterprise Deployments
To avoid this issue in future deployments, implement these practices:
Subscription readiness checklist: Create a standard checklist for new subscriptions that includes registering commonly used resource providers
Network subscription hardening: In central networking subscriptions, register resource providers for all services that might use the shared infrastructure
IaC validation: Add resource provider registration checks to your deployment pipelines before attempting resource creation
Documentation standards: Update your landing zone documentation to explicitly call out cross-subscription resource provider requirements
Monitoring and alerting: Set up alerts for resource provider registration status changes in critical subscriptions
The Bigger Picture
This PostgreSQL deployment issue is symptomatic of a broader challenge in cloud architecture: the gap between conceptual architecture patterns and their practical implementation details. While hub-and-spoke networking models are well-understood, the operational details like resource provider registration often get overlooked until they cause production issues.
The lesson extends beyond PostgreSQL: whenever designing cross-subscription architectures, consider all implicit dependencies, not just the obvious ones. Resource providers, permissions, and service-specific requirements can create hidden failure points that only surface during deployment.
For Azure customers, this means adopting a more defensive approach to infrastructure deployment: validate all prerequisites, including those that seem like they should "just work," and build comprehensive automation that handles these cross-subscription dependencies automatically.
By understanding and addressing these hidden requirements, organizations can move from reactive troubleshooting to proactive deployment success, ensuring that their PostgreSQL Flexible Server deployments and other cross-subscription resources work reliably from the start.
Comments
Please log in or register to join the discussion