A comprehensive guide to designing Azure AI landing zones for multi-tenant enterprises, balancing shared services with tenant isolation while enabling cost transparency and rapid onboarding.
As enterprises race to adopt generative AI at scale, the architectural challenge isn't just about deploying models—it's about creating platforms that can serve multiple tenants securely while maintaining cost transparency and operational efficiency. The traditional approach of building everything from scratch for each tenant quickly becomes unsustainable, both financially and operationally.
The Multi-Tenant AI Platform Challenge
Consider the reality facing large enterprises today: they need to deliver AI capabilities across departments, business units, and even external partners, but each requires isolation, governance, and clear cost attribution. Building separate infrastructure for each tenant would be prohibitively expensive and complex to manage.
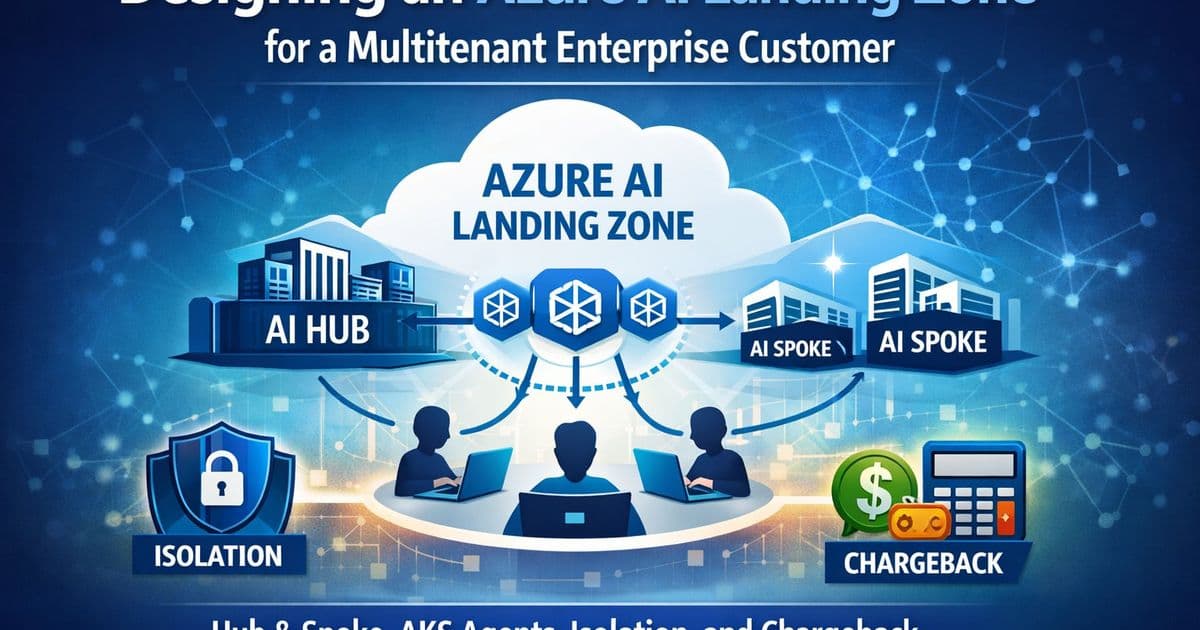
This is where the hub-and-spoke model shines. Rather than duplicating infrastructure, organizations can create a shared AI hub that hosts common capabilities—security controls, API gateways, monitoring, and even shared AI services—while maintaining isolated spokes for each tenant's specific needs.
Core Architecture Goals
The foundation of any successful enterprise AI platform rests on three non-negotiable requirements:
End-to-end tenant isolation across network, identity, compute, and data layers ensures that each tenant's information remains completely separate. This isn't just about security—it's often a regulatory requirement.
Secure, governed traffic flow from users to AI services means every request passes through consistent security controls, identity validation, and policy enforcement. No direct access to AI services bypasses these controls.
Transparent chargeback and showback mechanisms make it possible to attribute costs accurately, whether for shared hub resources or dedicated spoke services. This financial transparency is crucial for enterprise adoption.
Subscription and Management Group Design
The organizational structure mirrors the architectural separation. A typical enterprise layout might look like:
- Platform Management Group: Contains connectivity, management, and security subscriptions
- AI Hub Management Group: Houses the shared AI services subscription
- AI Spokes Management Group: Contains one subscription per tenant or business unit
This structure supports enterprise-scale governance while allowing teams to operate independently within defined guardrails. Each spoke subscription can have its own policies, budgets, and operational controls.
The AI Hub: Shared Services Control Plane
The AI Hub serves as the governed control plane for all AI consumption. Key components include:
Ingress and edge security: Azure Application Gateway with WAF provides the first line of defense, handling SSL termination, request routing, and OWASP protection.
Central egress control: Azure Firewall with forced tunneling ensures all outbound traffic is inspected and logged, preventing data exfiltration and enforcing compliance.
API governance: Azure API Management in private/internal mode acts as the identity and policy enforcement point, validating tenant context and applying quotas.
Shared AI services: Common deployments of Azure OpenAI, Azure AI Search, and other services reduce costs while maintaining security through proper isolation mechanisms.
Monitoring and observability: Centralized Azure Monitor and Log Analytics provide unified visibility across all tenants and services.
The AI Spoke: Tenant-Isolated Execution Plane
Each AI Spoke provides a completely isolated environment for tenant-specific workloads:
Network isolation: Dedicated VNets with private endpoints ensure no cross-tenant network access. All AI services are accessed via Private Link, eliminating public endpoints.
Identity isolation: Microsoft Entra ID with tenant-aware claims and conditional access policies enforce zero-trust principles at every layer.
Compute isolation: AKS clusters can be configured with namespace-per-tenant, dedicated node pools, or even separate clusters depending on compliance requirements.
Data isolation: Per-tenant storage accounts, databases, and vector indexes ensure complete data separation. Azure AI Search instances can be shared at the service level but isolated at the index level.
Network Architecture Deep Dive
The hub-and-spoke network design creates a spoke-to-spoke communication pattern through the hub. This means:
- All tenant traffic flows through the hub for inspection and policy enforcement
- Private DNS zones ensure service discovery without exposing public endpoints
- VNet peering connects spokes to the hub with proper routing rules
- Azure Firewall acts as the central traffic controller and inspection point
This design enables consistent security policies while maintaining the performance benefits of direct spoke-to-spoke communication when needed.
Identity and Access Management Strategy
Microsoft Entra ID serves as the central authentication authority, but the implementation goes deeper:
Application identities: Managed identities for Azure resources eliminate credential management and provide automatic token refresh.
Tenant context propagation: API Management validates and propagates tenant context to downstream services, enabling fine-grained authorization.
Conditional access: Policies can enforce device compliance, location-based restrictions, and risk-based authentication.
Least privilege: RBAC ensures users and services have only the permissions they need, following the principle of least privilege.
Secure Traffic Flow Implementation
The end-to-end traffic flow follows a strict pattern:
- Users access applications via Application Gateway + WAF
- Traffic is inspected and routed through Azure Firewall
- API Management validates identity, quotas, and tenant context
- AKS workloads invoke AI services over Private Link
- Responses return through the same governed path
This pattern provides full auditability, threat protection, and policy enforcement at every step.
AKS Multitenancy Options
The choice of AKS isolation strategy depends on tenant requirements:
Namespace-per-tenant: The default approach, cost-efficient and suitable for most scenarios. Provides logical isolation through Kubernetes namespaces.
Dedicated node pools: Offers medium isolation with reduced noisy-neighbor risk. Different node pools can have different VM sizes, OS configurations, and security policies.
Dedicated AKS clusters: Maximum isolation for high-compliance tenants, though at higher cost. Each tenant gets their own AKS cluster with separate control plane and worker nodes.
Most enterprises adopt a tiered approach, choosing the isolation level per tenant based on regulatory and risk requirements.
Cost Management and Chargeback
Effective cost management requires both technical and organizational approaches:
Tagging strategy: Mandatory tags include tenantId, costCenter, application, environment, and owner. These are enforced via Azure Policy across all subscriptions.
Chargeback approach:
- Dedicated spoke resources: Direct attribution via subscription and tags
- Shared hub resources: Allocated using usage telemetry from API Management and AKS
Cost data export: Azure Cost Management exports detailed usage data, which can be visualized using Power BI for showback and chargeback reporting.
Security Controls Checklist
A comprehensive security posture includes:
- Private endpoints for all AI services, storage, and search
- No public network access for sensitive services
- Azure Firewall for centralized egress and inspection
- WAF for OWASP protection
- Azure Policy for governance and compliance
- Microsoft Defender for Cloud for threat protection
- Azure Monitor for security monitoring and alerting
Deployment and Automation
Foundation deployment leverages Azure Landing Zone accelerators using Bicep or Terraform. The modular approach includes:
Foundation: Azure Landing Zone accelerators establish the management group hierarchy, policies, and networking foundation.
Workloads: Modular IaC for hub and spokes enables consistent deployment across environments.
AKS apps: GitOps using Flux or Argo CD provides automated deployment and configuration management.
Observability: Policy-driven diagnostics and centralized logging ensure consistent monitoring across all components.
Real-World Implementation Considerations
When implementing this architecture, several practical considerations emerge:
Onboarding automation: The tenant onboarding flow should be fully automated using landing zone vending models. This includes provisioning subscriptions, deploying VNets, configuring private DNS, and setting up monitoring.
Performance optimization: While the hub-and-spoke model provides security benefits, it can introduce latency. Careful network design and regional placement of services can minimize performance impact.
Cost optimization: Shared services in the hub reduce costs, but proper monitoring ensures no single tenant dominates shared resources. Usage quotas and throttling prevent abuse.
Compliance mapping: Different tenants may have different compliance requirements. The architecture should support varying levels of isolation and data residency based on regulatory needs.
The Path Forward
This Azure AI Landing Zone design provides a repeatable, secure, and enterprise-ready foundation for any large customer adopting AI at scale. By combining hub-and-spoke networking, AKS-based AI agents, strong tenant isolation, FinOps-ready chargeback, and Azure Landing Zone best practices, organizations can confidently move AI workloads from experimentation to production—without sacrificing security, governance, or cost transparency.
The key insight is that successful enterprise AI platforms aren't just about the technology—they're about creating an operational model that balances innovation with control, shared efficiency with tenant isolation, and rapid deployment with enterprise governance.
The architecture described here represents a mature approach to enterprise AI platform design, one that has been proven in production environments serving multiple tenants across various industries. As AI adoption continues to accelerate, organizations that invest in this type of scalable, secure platform will be best positioned to deliver AI value across their entire enterprise.
Comments
Please log in or register to join the discussion