Consumer goods giant Clorox has filed a $380 million lawsuit against IT services provider Cognizant, alleging gross negligence after hackers tricked its help desk into resetting credentials without verification. The breach, linked to Scattered Spider actors, paralyzed Clorox's operations for weeks, causing massive product shortages. This case exposes critical vulnerabilities in third-party IT service security and the devastating ripple effects of social engineering.
Clorox Seeks $380M from Cognizant Over Help Desk Hack That Enabled 'Debilitating' Cyberattack
 Clorox products on a store shelf. The company's operations were paralyzed for weeks following the cyberattack. (Source: BleepingComputer)
Clorox products on a store shelf. The company's operations were paralyzed for weeks following the cyberattack. (Source: BleepingComputer)
In a landmark lawsuit that underscores the fragility of third-party IT security, Clorox is pursuing $380 million in damages from Cognizant Technology Solutions. The consumer goods giant alleges that Cognizant's help desk became the unwitting accomplice in a devastating August 2023 cyberattack by resetting an employee's credentials for hackers—without performing basic identity verification.
The breach, attributed to the notorious Scattered Spider group, followed a chillingly simple social engineering playbook: A threat actor posing as a Clorox employee called Cognizant's service desk multiple times on August 11, 2023, requesting password and multi-factor authentication (MFA) resets. According to legal filings, Cognizant's agent complied without ever verifying the caller's identity or following Clorox's mandated procedures.
"At no point during any of the calls did the Agent verify that the caller was in fact Employee 1," states Clorox's complaint. "The Agent reset Employee 1's MFA credentials multiple times without any identity verification at all."
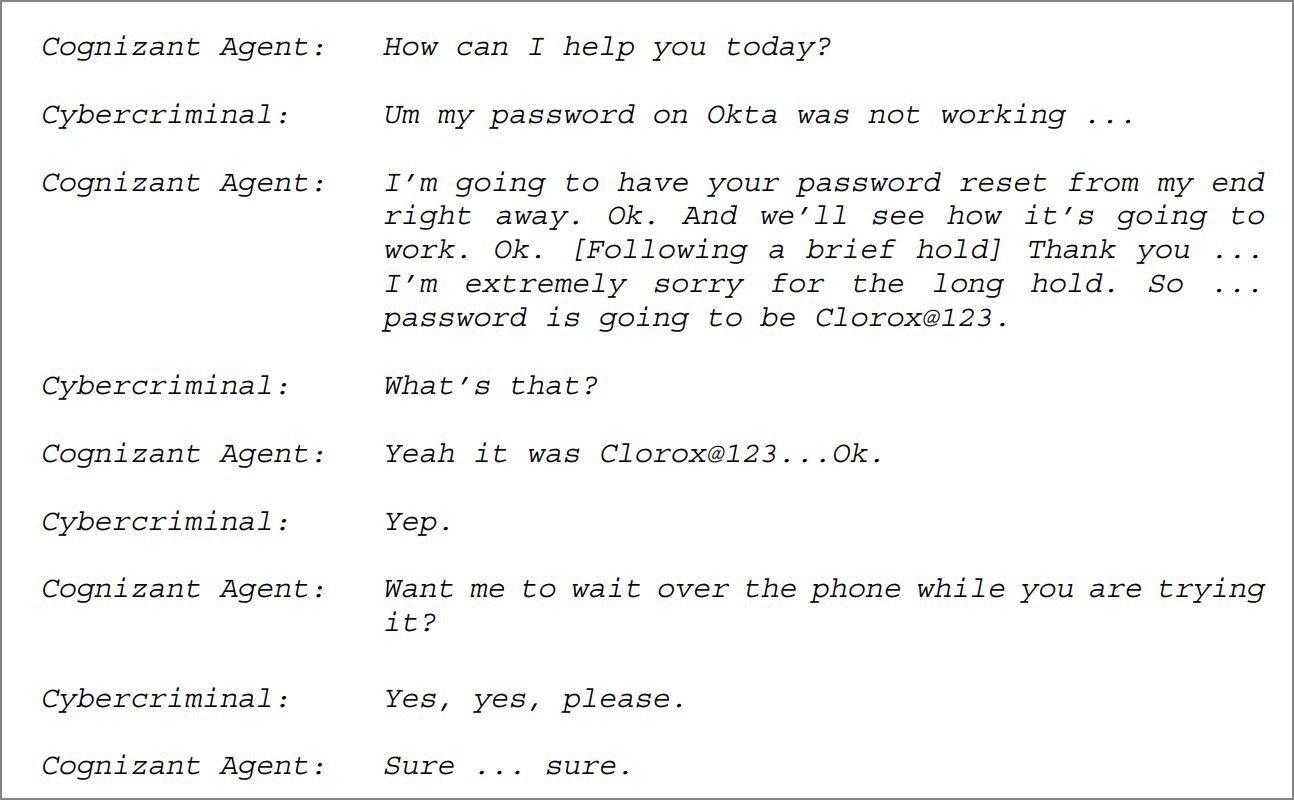 Transcript excerpt from the call between the hacker and Cognizant's service desk. (Source: Clorox complaint via BleepingComputer)
Transcript excerpt from the call between the hacker and Cognizant's service desk. (Source: Clorox complaint via BleepingComputer)
The consequences cascaded rapidly. With initial access secured, attackers replicated the tactic to compromise an IT security employee's account, gaining privileged network access. This enabled them to deploy disruptive malware that halted manufacturing lines, paralyzed corporate systems, and triggered nationwide product shortages of Clorox's cleaning supplies. The company estimates $49 million in direct remediation costs and over $300 million in broader business impacts.
Anatomy of a Preventable Breach
Clorox's contract with Cognizant included explicit requirements for credential resets: Agents were to verify identities and notify both the employee and their manager via email. Neither protocol was followed. Legal documents reveal the threat actor used identical social engineering tactics seen in recent Scattered Spider attacks against UK retailers Marks & Spencer and Co-op.
Compounding the failure, Clorox alleges Cognizant's incident response was catastrophically inadequate—delaying containment, failing to lock compromised accounts, and deploying underqualified personnel. "When Clorox called on Cognizant to provide incident response... Cognizant botched its response and compounded the damage," the lawsuit asserts.
The Third-Party Security Reckoning
This case spotlights three critical industry vulnerabilities:
- Help desks as critical attack surfaces: Password reset services provide low-effort, high-reward entry points when verification fails
- Supply chain domino effects: A single vendor compromise can cripple client operations
- MFA bypass via social engineering: Attackers increasingly target enrollment/reset processes rather than cracking codes
Clorox's allegations—including gross negligence, breach of contract, and misrepresentation of staff training—could set precedent for vendor accountability. As outsourcing grows, enterprises must scrutinize partners' social engineering defenses, enforce strict verification protocols, and demand transparent security audits.
The $380 million lawsuit serves as a stark reminder: In today's threat landscape, your security is only as strong as your weakest service provider's help desk.
Source: BleepingComputer

Comments
Please log in or register to join the discussion