A new attack technique called ConsentFix combines ClickFix-style social engineering with OAuth consent phishing to hijack Microsoft accounts. Discovered by Push Security in December 2025, the attack bypasses traditional authentication controls by exploiting first-party Microsoft apps and legacy scopes. Security researchers have identified 11 vulnerable applications and linked the campaign to Russian state-affiliated APT29.
ConsentFix: A New Evolution in OAuth Phishing Attacks
In December 2025, the Push Security research team discovered and blocked a novel attack technique they named ConsentFix. This method merges ClickFix-style social engineering with OAuth consent phishing to hijack Microsoft accounts. The campaign was detected across a large network of compromised websites where attackers injected malicious payloads, affecting multiple customer estates.

The attack technique prompted victims to share an OAuth authorization code with attackers via a phishing page. Attackers then entered this code into a target application on their own device to complete the authorization handshake and take over the account. By hijacking OAuth, attackers effectively bypass identity-layer controls like passwords and MFA, including phishing-resistant authentication methods like passkeys, because the attack sidesteps the authentication process entirely.
How ConsentFix Works: The Technical Breakdown
ConsentFix operates through a carefully orchestrated sequence that exploits legitimate OAuth flows:
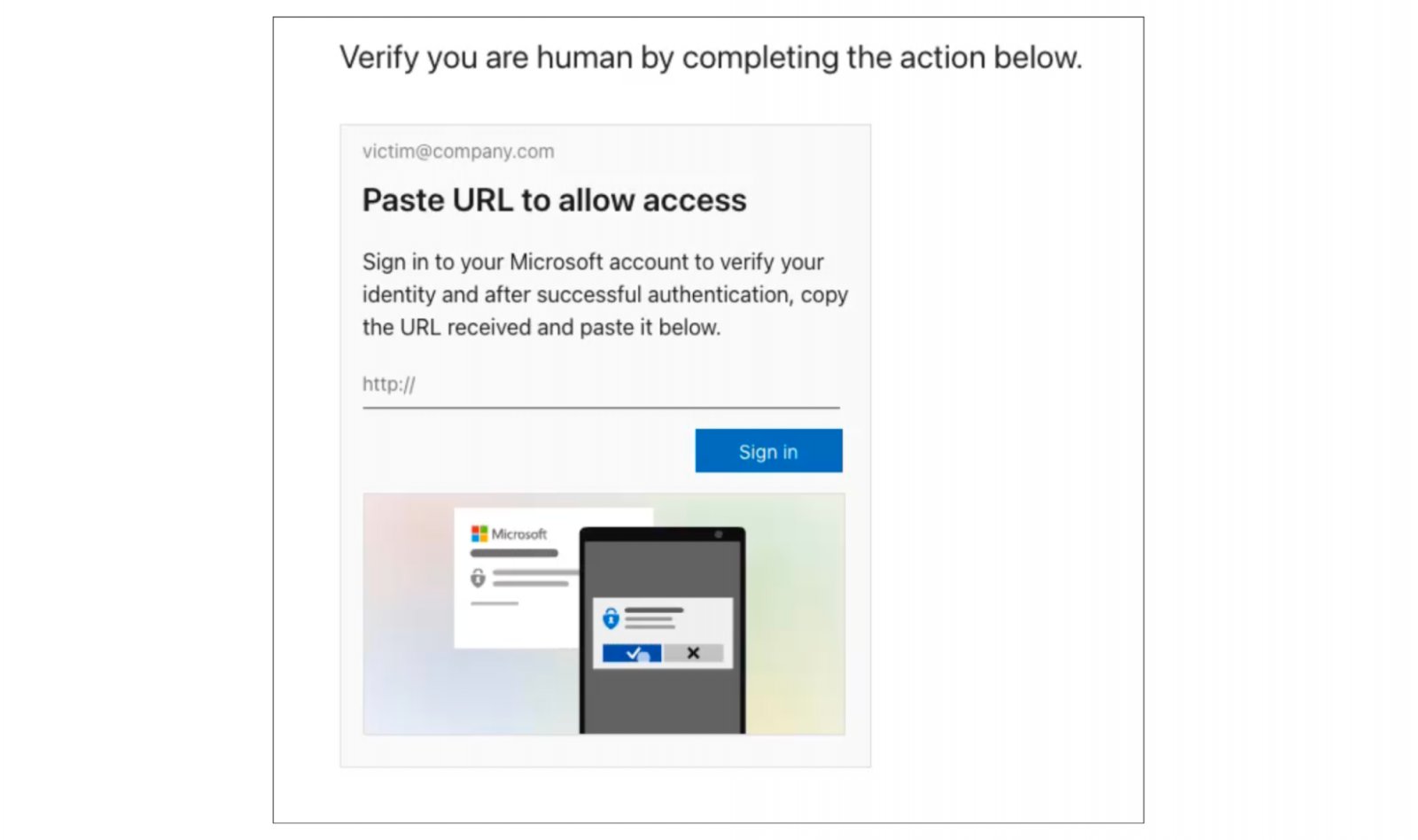
Initial Delivery: Victims are served a page requiring verification that they are human by pasting a URL into the phishing page.
Legitimate Login: Clicking the "Sign In" button opens a genuine Microsoft login page. If the user is already logged into their normal browser (which is typical for working users), their account information pre-populates, requiring no additional authentication.
Authorization Code Generation: Selecting their account redirects them to a localhost URL containing an OAuth authorization code. This code is then posted back to the original phishing page to complete the attack.
Token Exchange: Once attackers receive the URL, they exchange it for an access token or refresh token for the targeted application—in this case, Azure CLI.
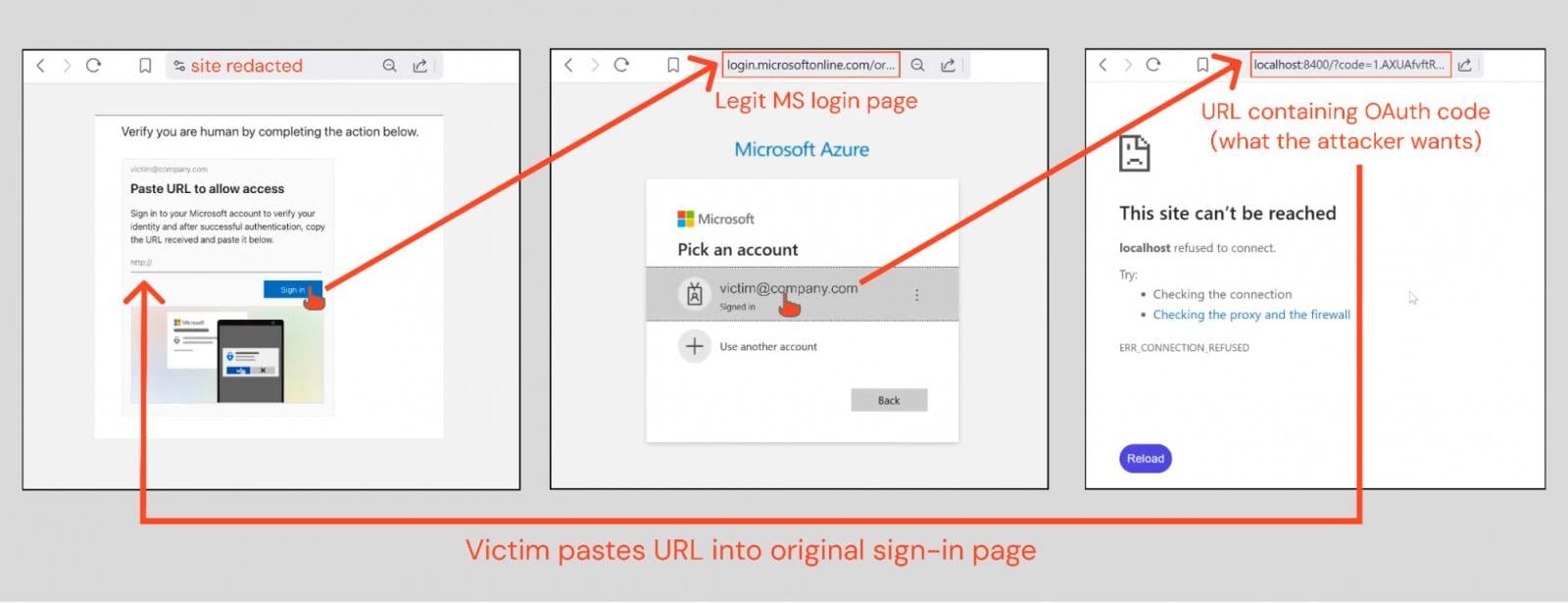
The attack essentially hijacks the authorization flow that occurs when a user logs into Azure CLI, a command-line client for managing Azure AD/Entra ID environments. However, attackers use the victim's information to log in on their own device instead.
Why ConsentFix Is Particularly Dangerous
Unlike typical OAuth attacks that connect primary workspace accounts to fraudulent third-party applications, ConsentFix targets first-party Microsoft apps that cannot be restricted in the same way and are pre-consented in every tenant. This means users can authenticate to them without admin approval.
The technique also leverages legacy scopes outside default logging parameters to evade detection. These scopes target applications with known Conditional Access policy exclusions, meaning default controls designed to block malicious OAuth grants don't apply. Organizations may lack logging to detect the attack, and conditional access policy exclusions render many expected controls ineffective.
Campaign Attribution and Evolution
Recent intelligence links this campaign to Russian state-affiliated APT29, corroborated by threat researchers collaborating with Push Security. This attribution aligns with the stealthy tactics observed, which extend beyond typical criminal phishing campaigns.
The technique appears to be an evolution of a previously identified Russia-affiliated campaign documented by Volexity. That earlier campaign featured a manual version where victims were social-engineered via email to open Microsoft URLs, copy localhost responses, and send them back to attackers via email.
Community Response and Researcher Contributions
The security community responded rapidly to ConsentFix. Within days, security researcher John Hammond posted an improved version on his YouTube channel, demonstrating a slick implementation where the URL containing the Microsoft authorization code was generated in a pop-up browser window that could be drag-and-dropped into the phishing page. This smoother implementation significantly increases the likelihood of victim success.
Fabian Bader and Dirk-jan Mollema from Glueck Kanja identified 11 additional first-party apps vulnerable to ConsentFix that also have known Conditional Access exclusions:
- Microsoft Azure CLI: 04b07795-8ddb-461a-bbee-02f9e1bf7b46
- Microsoft Azure PowerShell: 1950a258-227b-4e31-a9cf-717495945fc2
- Microsoft Teams: 1fec8e78-bce4-4aaf-ab1b-5451cc387264
- Microsoft Whiteboard Client: 57336123-6e14-4acc-8dcf-287b6088aa28
- Microsoft Flow Mobile PROD-GCCH-CN: 57fcbcfa-7cee-4eb1-8b25-12d2030b4ee0
- Enterprise Roaming and Backup: 60c8bde5-3167-4f92-8fdb-059f6176dc0
- Visual Studio: 872cd9fa-d31f-45e0-9eab-6e460a02d1f1
- Aadrm Admin Powershell: 90f610bf-206d-4950-b61d-37fa6fd1b224
- Microsoft SharePoint Online Management Shell: 9bc3ab49-b65d-410a-85ad-de819febfddc
- Microsoft Power Query for Excel: a672d62c-fc7b-4e81-a576-e60dc46e951d
- Visual Studio Code: aebc6443-996d-45c2-90f0-388ff96faa56
Updated Recommendations for Security Teams
Traditional security tools provide limited protection against browser-native attacks like ConsentFix. Organizations must shift their detection surface to the browser itself. Here are specific mitigations:
Enable Critical Logging
- Activate logging for the deprecated AADGraphActivityLogs. Without this, you cannot detect the attack through Microsoft's standard logging infrastructure.
Hunt for Specific Indicators
- Search logs for the identified Application IDs listed above
- Monitor Resource IDs for Windows Azure Active Directory (00000002-0000-0000-c000-000000000000) and Microsoft Intune Checkin (26a4ae64-5862-427f-a9b0-044e62572a4f)
Reduce Attack Surface
- Create Service Principals for each vulnerable app
- Restrict authorized users/groups for each Service Principal
- Block CLI tool access via Conditional Access policy with exclusions only for authorized users/groups
Community Resources
- Elastic detection rules for ConsentFix created by the community
- Glueck Kanja's mitigation and hunting guidance
The Future of ConsentFix
Based on the rapid iteration speed demonstrated by security researchers and the breadth of exploitable applications and scopes, both red teams and criminals will likely adopt ConsentFix into their TTPs. New variants are expected imminently, if not already circulating.
Browser-Based Detection: The Only Reliable Approach
ConsentFix demonstrates why IoC-based detection is insufficient. Attackers can trivially bypass signature-based defenses by modifying their infrastructure. The only reliable detection method analyzes the end-to-end process of webpages loading and running in browsers, plus how users interact with pages, to spot universal indicators of malicious activity.
This approach mirrors how EDR works for endpoint attacks but applies it to the browser context. Organizations need real-time blocking capabilities that can intercept attacks as they happen, not just post-incident detection.
For teams managing Microsoft environments, implementing browser-native security monitoring is no longer optional—it's essential for defending against evolving OAuth attacks that exploit legitimate authentication flows.
This article was sponsored and written by Push Security, which detected and blocked ConsentFix across customer environments using behavioral threat detection powered by deep browser telemetry.

Comments
Please log in or register to join the discussion