A critical authentication bypass vulnerability in the GNU InetUtils telnetd server, present for over a decade, is now being actively exploited by attackers seeking root access on legacy systems. The flaw, tracked as CVE-2026-24061, allows attackers to bypass login authentication by manipulating the USER environment variable, highlighting the persistent risks of maintaining legacy network services.
A coordinated exploitation campaign has been observed targeting a critical authentication bypass vulnerability in the GNU InetUtils telnetd server that has remained undetected for 11 years. The vulnerability, designated CVE-2026-24061, was publicly disclosed on January 20, 2026, and multiple exploit examples are already circulating in the wild.
The Technical Mechanism
The flaw resides in how telnetd handles environment variables when spawning the /usr/bin/login process. According to Simon Josefsson, an open-source contributor who reported the issue, the vulnerability stems from unsanitized environment variable handling. Specifically, telnetd passes the user-controlled USER environment variable directly to login(1) without any sanitization.
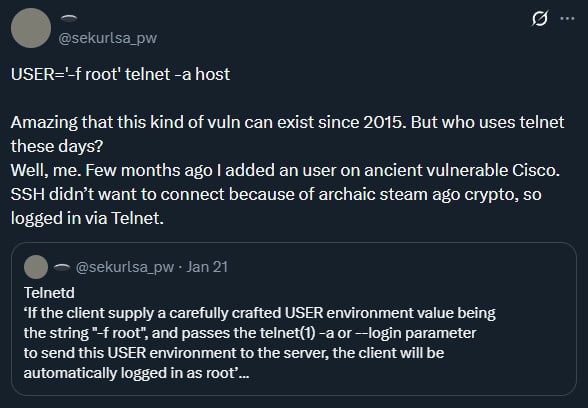
This creates a dangerous attack vector: by setting USER to -f root and connecting with the telnet -a command, an attacker can completely skip the authentication process and obtain root shell access. The -f flag in the login command typically forces a login without password authentication, and when combined with root privileges, gives attackers immediate administrative control.
Affected Systems and Timeline
The vulnerability affects GNU InetUtils versions 1.9.3 (released in 2015) through 2.7. The issue was patched in version 2.8, released shortly after the vulnerability was reported. This means the flaw has been present in production systems for approximately 11 years, since the release of version 1.9.3 in 2015.
GNU InetUtils is a collection of classic network client and server tools maintained by the GNU Project. The package includes:
- telnet/telnetd
- ftp/ftpd
- rsh/rshd
- ping
- traceroute
These tools are distributed across multiple Linux distributions and are particularly common in legacy Unix systems, embedded devices, and industrial control environments.
Why Telnet Persists in Modern Infrastructure
Despite Telnet's well-documented security weaknesses—primarily its lack of encryption—many systems still include it for compatibility reasons. The protocol remains prevalent in several specific contexts:
Industrial Sector: Telnet's simplicity and low overhead make it attractive for industrial control systems where computational resources may be limited and reliability is paramount.
Legacy Device Management: Many organizations maintain telnet connections to manage older network equipment. As one user confirmed, telnet is still used "to connect to older Cisco devices that are way past 'End of Life.'"
Embedded and IoT Devices: On legacy and embedded devices, telnet can run for years without updates. This makes it common in IoT devices, industrial sensors, cameras, and Operational Technology (OT) networks where maintenance cycles are extended.
Current Exploitation Activity
Threat monitoring firm GreyNoise has detected real-world exploitation activity leveraging CVE-2026-24061. Between January 21 and 22, they observed attacks from 18 unique attacker IPs across 60 Telnet sessions. All activity was deemed 100% malicious, with attackers sending 1,525 packets totaling 101.6 KB.
The attacks abuse the Telnet IAC (Interpret As Command) option negotiation to inject USER=-f <user> and grant shell access without authentication. GreyNoise notes that most activity appears automated, though they observed a few "human-at-keyboard" cases.
In 83.3% of observed attacks, threat actors targeted the 'root' user specifically. Post-exploitation activities included:
- Automated reconnaissance
- Attempts to persist SSH keys
- Deployment of Python malware
However, these post-exploitation attempts failed on observed systems due to missing binaries or directories, suggesting the attackers were probing systems without fully understanding their configuration.
Mitigation Strategies
Organizations with potentially vulnerable systems have several options:
Immediate Patching: Upgrade to GNU InetUtils version 2.8 or later. This is the most effective solution that eliminates the vulnerability while maintaining telnet functionality.
Service Disabling: For systems where telnet is not required, disable the telnetd service entirely. This removes the attack surface completely.
Network Hardening: Block TCP port 23 on all firewalls to prevent external access to telnet services. This is particularly important for internet-facing systems.
Network Segmentation: For industrial and OT environments where telnet cannot be immediately disabled, implement strict network segmentation to isolate vulnerable devices from broader networks.
Security Implications
This vulnerability demonstrates several critical security principles:
Legacy Protocol Risks: Even well-known insecure protocols like Telnet continue to pose threats when maintained in production environments.
Long-Lived Vulnerabilities: Security flaws can persist undetected for years, even in widely used open-source software.
Attack Surface Expansion: As organizations modernize their infrastructure, legacy components often remain in place for compatibility, creating hidden attack vectors.
Automated Exploitation: Once vulnerabilities are publicly disclosed, automated exploitation tools can quickly target vulnerable systems, as seen in the coordinated campaign observed by GreyNoise.
Recommendations for Security Teams
Inventory Assessment: Conduct a comprehensive inventory of systems running GNU InetUtils, particularly focusing on embedded devices, industrial systems, and legacy infrastructure.
Patch Management: Prioritize patching for internet-facing systems and those in critical infrastructure environments.
Monitoring Enhancement: Implement network monitoring for Telnet traffic on port 23, particularly for unusual IAC option negotiations or authentication bypass attempts.
Compensating Controls: For systems that cannot be immediately patched, implement additional monitoring and access controls around telnet services.
Long-term Planning: Develop migration plans to replace Telnet with SSH or other encrypted alternatives, particularly for systems handling sensitive data or critical operations.
The exploitation of CVE-2026-24061 serves as a reminder that security vulnerabilities in legacy protocols and components can remain dormant for years before being discovered and exploited. Organizations must balance the practical needs of maintaining legacy systems with the security requirements of modern infrastructure, implementing both immediate mitigations and long-term modernization strategies.
While current exploitation appears limited in scope, the availability of public exploits and the simplicity of the attack vector suggest that opportunistic attackers will likely increase their targeting of vulnerable systems. Security teams should act promptly to assess their exposure and implement appropriate protections before attackers optimize their attack chains for broader deployment.

Comments
Please log in or register to join the discussion