Spain's largest energy provider, Endesa, confirmed hackers accessed customer contract data including personal identification, contact details, and banking information for millions of customers. While the company claims no evidence of fraud yet, threat actors are allegedly selling a 1TB database containing 20 million records on dark web forums.
Spain's largest electric utility company has confirmed a significant security incident that potentially impacts millions of customers across the Iberian Peninsula. Endesa, which distributes gas and electricity to more than 10 million customers in Spain and Portugal, disclosed that unauthorized actors gained access to its commercial platform and extracted sensitive contract-related information.

What Happened
Endesa detected unauthorized access to its commercial platform, specifically affecting the Energía XXI operator. According to the company's official notification, despite implemented security measures, hackers successfully exfiltrated personal data tied to customer energy contracts. The breach appears to have targeted a commercial platform rather than core operational systems, meaning electrical distribution and billing services remain unaffected.
The company responded immediately by blocking access to compromised internal accounts, preserving log records for forensic analysis, and establishing elevated monitoring for suspicious activity. Endesa has notified the Spanish Data Protection Agency and other relevant authorities, as required under GDPR and Spanish data protection law.
Data Exposed: What Customers Lost
The breach exposed a concerning breadth of personal information that could enable multiple attack vectors:
- Basic identification details: Full names and demographic information
- Contact information: Physical addresses, phone numbers, and email addresses
- National identity numbers (DNI): Spain's primary identification document number
- Contract details: Specific energy service agreements and account information
- Payment information: Bank account details including IBAN numbers
Crucially, Endesa emphasizes that account passwords were not compromised. However, the combination of DNI numbers and IBANs creates a particularly risky scenario for Spanish citizens, as these two data points are frequently used together to verify identity for financial transactions and government services.
The Company's Response and Risk Assessment
Endesa's official stance is cautiously optimistic. In their notification, they state: "As of the date of this communication, there is no evidence of any fraudulent use of the data affected by the incident, making it unlikely that a high-risk impact on your rights and freedoms will materialize."
Despite this reassurance, the company is taking a proactive approach:
- Direct customer notification: All affected customers are being contacted directly
- Vigilance recommendations: Customers are urged to watch for identity impersonation, data theft, and phishing attempts
- Reporting mechanism: A dedicated phone number has been established for reporting suspicious activity
- Ongoing investigation: The company promises additional updates as the forensic analysis continues
The Dark Web Complication
While Endesa was managing the official response, threat actors on dark web forums began advertising what they claim is a stolen Endesa database. The listing, which appeared last week, offers:
- Approximately 1TB of SQL databases
- Claims of 20 million customer records
- Exclusive sale to a single buyer
- Sample data to verify authenticity
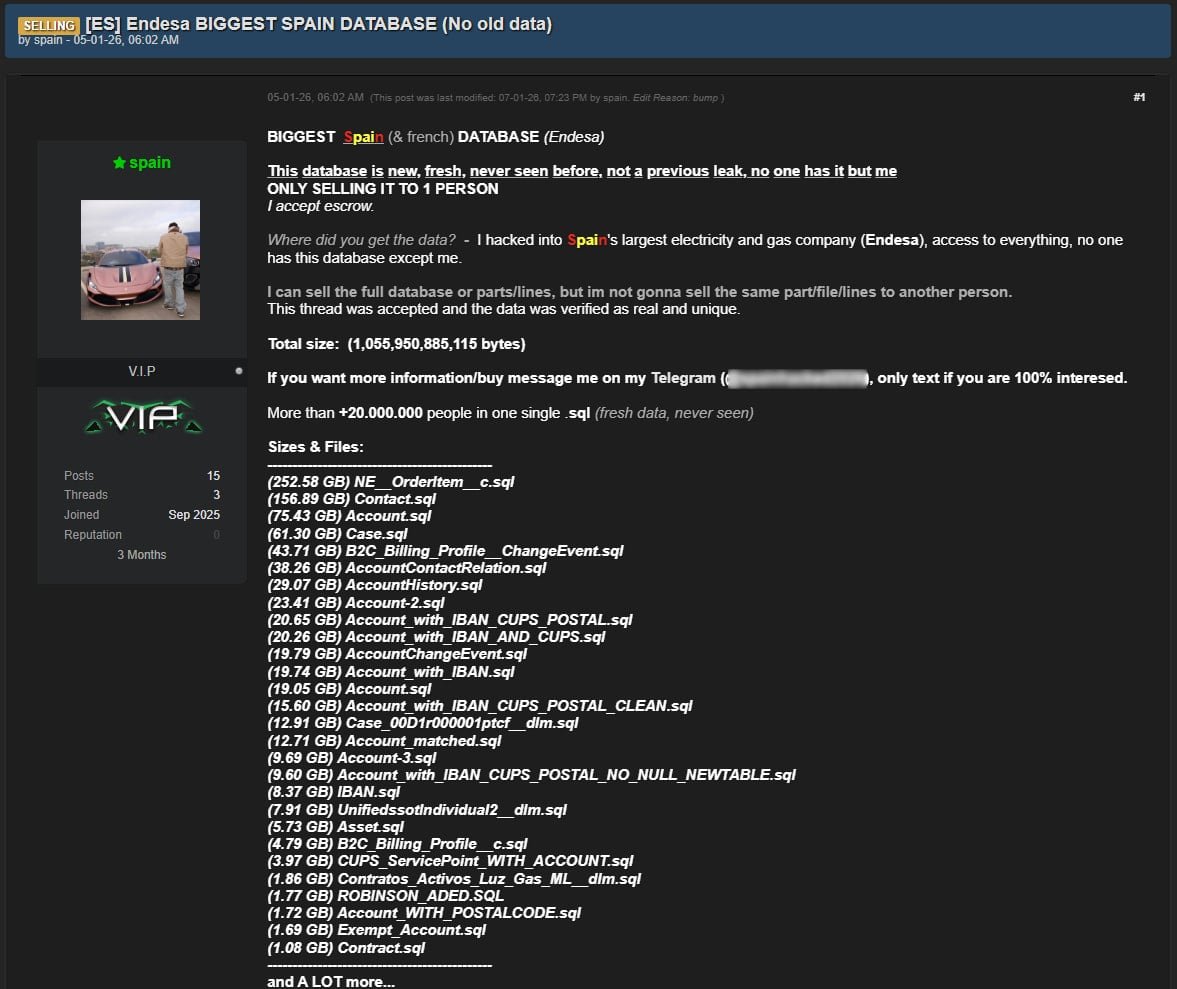
The sample data presented by the sellers aligns with the data types Endesa confirmed were accessed. BleepingComputer contacted Endesa for comment on these specific allegations, but the company's spokesperson was limited to sharing the official statement, neither confirming nor denying the dark web claims.
This creates a significant secondary risk: even if Endesa's internal monitoring hasn't detected fraud yet, the data could already be in criminal hands and awaiting the right buyer.
Why This Breach Matters
The Endesa breach represents a textbook example of modern data breach risks:
Identity theft potential: Spanish DNI numbers are powerful identity tools. Combined with contact information and contract details, criminals can impersonate victims to open fraudulent accounts, apply for loans, or access government services.
Financial fraud: IBAN numbers provide direct access to bank accounts. While criminals cannot withdraw funds without additional authentication, they can use this information for sophisticated social engineering attacks against banks or to set up fraudulent direct debits.
Phishing precision: With detailed contract information, attackers can craft highly convincing phishing emails that reference specific account details, service agreements, and billing cycles.
Long-term exposure: Unlike a credit card number that can be cancelled, DNI numbers and IBANs are permanent identifiers that remain valuable to criminals for years.
Practical Steps for Affected Customers
If you're an Endesa or Energía XXI customer, consider these immediate actions:
Monitor your accounts: Check bank statements weekly for unauthorized transactions. Set up transaction alerts if your bank offers them.
Verify all communications: Be extremely cautious of emails, calls, or texts claiming to be from Endesa. Attackers with contract details can make communications appear legitimate. Always verify through official channels.
Watch for DNI misuse: Monitor your credit report and be alert for accounts or services opened in your name. Spanish citizens can check their credit through institutions like ASNEF.
Enable two-factor authentication: Ensure your bank accounts and email use strong two-factor authentication, preferably app-based rather than SMS.
Report suspicious activity: Use the phone number provided in Endesa's notification to report any suspected fraud attempts.
Consider a fraud alert: Contact your bank to flag your account for additional verification, especially if you notice any unusual activity.
Broader Implications
This breach highlights several ongoing trends in cybersecurity:
Critical infrastructure vulnerability: Energy companies hold some of the most sensitive customer data yet often prioritize operational uptime over security, creating attractive targets for attackers.
The exclusivity sale model: Offering data to a single buyer reduces the chance of widespread immediate fraud but doesn't eliminate the risk. It also suggests the attackers understand the data's value and are seeking maximum profit.
GDPR notification timing: Endesa's disclosure appears timely under GDPR requirements, which mandate notification within 72 hours of becoming aware of a breach. This contrasts with companies that delay disclosure, potentially facing larger fines.
Operational vs. data systems separation: The fact that customer services remain operational demonstrates good network segmentation, but also shows that data systems may have been less protected than operational ones.
What Comes Next
Endesa has promised to notify customers if the ongoing investigation reveals additional details. The Spanish Data Protection Agency will likely conduct its own investigation to determine if Endesa implemented adequate security measures under GDPR requirements.
If the dark web sales claims prove true, the data may circulate among criminal networks for months or years, creating ongoing risks for affected customers. The exclusivity sale could delay widespread fraud, but doesn't eliminate it.
For Endesa, this breach represents both a technical failure and a reputational challenge. As Spain's largest energy provider and part of the Enel Group, the company will face scrutiny over its security investments and incident response capabilities.
For customers, vigilance is now a long-term requirement. The combination of DNI, IBAN, and contract data creates a persistent identity risk that requires ongoing monitoring rather than a one-time fix.
The Endesa breach serves as a reminder that even large, essential service providers with significant security investments remain vulnerable to determined attackers. As energy companies increasingly digitize their operations and customer interactions, the attack surface expands, making comprehensive security programs not just recommended, but essential.
Related: Endesa official notification | Spanish Data Protection Agency | GDPR breach guidance

Comments
Please log in or register to join the discussion