Cybercriminals are increasingly recruiting insiders within financial institutions, telecom providers, and technology firms to bypass security defenses. Darknet advertisements offer payouts up to $15,000 for network access or sensitive data, creating a complex threat landscape. This shift demands enhanced monitoring and proactive defense strategies beyond traditional cybersecurity measures.
The New Frontline in Cybersecurity: Insider Recruitment on the Darknet

Cyber attackers have pivoted from brute-force attacks to a more insidious strategy: recruiting employees within targeted organizations. As revealed by Check Point Research, darknet forums host burgeoning marketplaces where insiders at banks, telecom giants, and tech firms are offered payments ranging from $3,000 to $15,000 for network access, sensitive data, or deliberate security sabotage. This trend represents a fundamental shift in the threat landscape, exploiting human vulnerabilities rather than technical flaws.
The Darknet's Recruitment Playbook
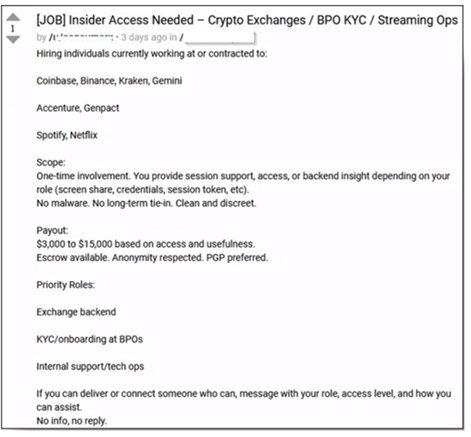
Recruitment ads on encrypted platforms blend transactional offers with psychological manipulation. One July 2025 post urged employees to "escape the endless work cycle" by collaborating with criminals, promising six-figure payouts. Others specifically target long-tenured staff at critical infrastructure providers, framing betrayal as a shortcut to financial freedom. These posts avoid complex jargon—opting for concise, actionable proposals that bypass traditional threat detection systems.
"When internal staff disable defenses or leak credentials, preventing attacks becomes exponentially harder," notes the Check Point report. "Monitoring the deep web for organizational mentions is now as critical as deploying advanced cyber prevention technologies."
High-Value Targets: From Crypto Exchanges to Central Banks
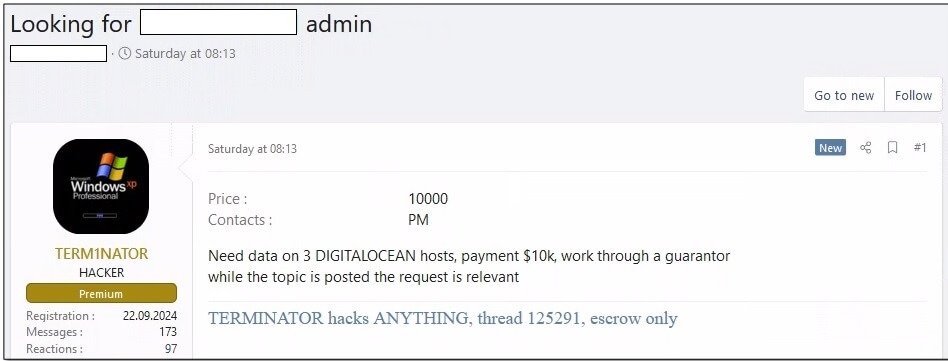
Financial institutions face acute risk, with darknet ads explicitly targeting the Federal Reserve's partner banks and European banking transaction systems. Cryptocurrency exchanges like Coinbase, Binance, and Gemini are similarly besieged—one listing offered $25,000 for a dataset of 37 million user records. Tech giants haven't escaped scrutiny, with recruitment efforts focused on Apple, Samsung, and cloud service providers. A Belgian enterprise software firm's employee data (credentials, roles, contact details) recently appeared for sale at $25,000.
Telecom Sabotage and Ransomware Syndicates
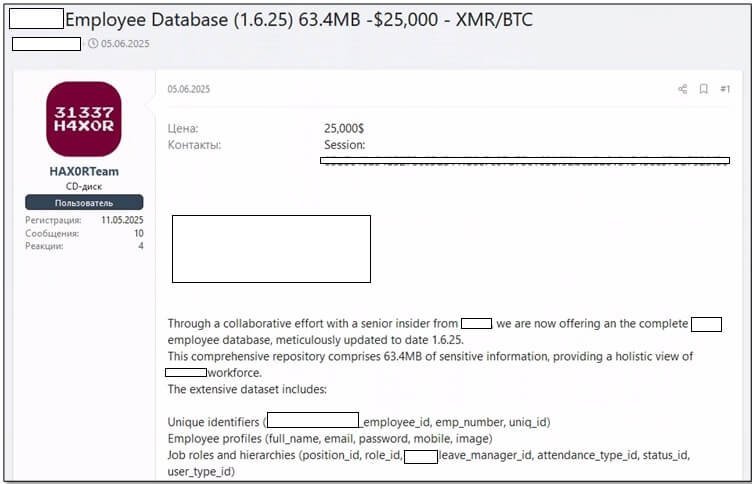
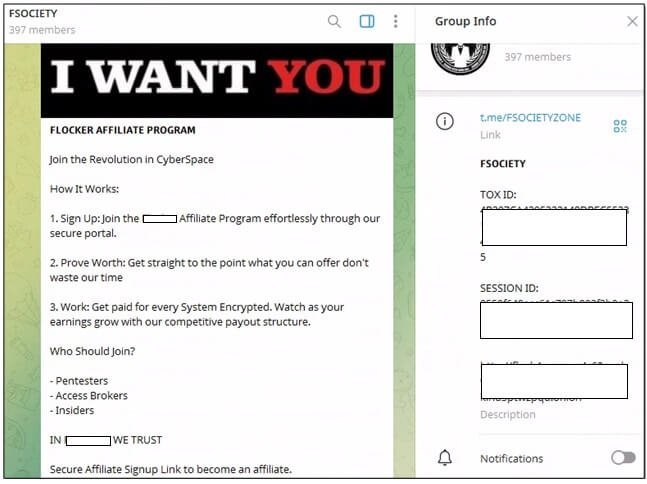
Telecom employees are prized for SIM-swapping operations, which circumvent two-factor authentication by hijacking SMS verification. Payouts here reach $10,000–$15,000 per insider collaboration. Meanwhile, ransomware groups like one observed in July (with 400+ members) now openly recruit through Telegram, inviting pentesters and access brokers to profit from each successful system encryption. Logistics sector insiders are also recruited for customs interference or shipment manipulation at lower tiers ($500–$5,000).
Why Insider Threats Defy Conventional Defenses
This recruitment surge highlights cybersecurity's Achilles' heel: trust. Insiders bypass firewalls, endpoint detection, and multi-factor authentication with legitimate credentials. The anonymity of cryptocurrency payments accelerates the trend, while motivations vary from financial desperation to ideological grievances. Consequences extend beyond immediate financial loss—regulatory penalties, customer attrition, and operational paralysis often follow breaches.
Building an Insider-Resilient Organization
Mitigating this threat requires layered human and technical strategies:
- Behavioral monitoring: Analytics detecting unusual data access patterns or after-hours activity
- Strict access governance: Zero-trust frameworks minimizing unnecessary privileges
- Darknet surveillance: Automated scanning for corporate data leaks or employee recruitment ads
- Cultural reinforcement: Continuous training emphasizing ethical responsibilities and attack recognition
As criminal enterprises professionalize their recruitment operations, organizations must treat insider risk as a core component of threat intelligence—not an HR anomaly. The most impregnable firewall crumbles when someone holds the keys.
Source: Check Point Research

Comments
Please log in or register to join the discussion