Cybersecurity researchers have uncovered a critical pattern: spikes in network reconnaissance, scanning, and brute-force attacks consistently precede the disclosure of new vulnerabilities by up to six weeks. GreyNoise's analysis of 216 events shows this correlation is strongest for edge devices from vendors like Palo Alto and Fortinet, offering defenders a rare early warning window. This insight transforms how organizations can anticipate threats and shift from reactive patching to proactive def
Malicious Activity Spikes Predict New Security Flaws in 80% of Cases, Study Reveals

In a revelation that could redefine cybersecurity defense strategies, threat monitoring firm GreyNoise has demonstrated that surges in malicious network activity are not random noise—they're a statistically significant harbinger of new security vulnerabilities. According to research based on data from GreyNoise's 'Global Observation Grid' (GOG), collected since September 2024, spikes in activities like targeted scanning, brute-forcing, and reconnaissance against edge devices precede the disclosure of new CVEs (Common Vulnerabilities and Exposures) in 80% of cases within six weeks. This pattern, identified across 216 high-confidence events after rigorous data filtering, provides defenders with an unprecedented opportunity to anticipate and mitigate threats before exploits materialize.
The Unmistakable Correlation: Data and Methodology
GreyNoise applied objective statistical thresholds to avoid bias, analyzing network traffic patterns tied to eight major enterprise edge vendors. Their findings revealed that 50% of observed spikes led to new CVEs within just three weeks, escalating to 80% by the six-week mark. As the researchers noted:
"Across all 216 spike events we studied, 50 percent were followed by a new CVE within three weeks, and 80 percent within six weeks. These are not anomalies—they're repeatable patterns that attackers exploit systematically."
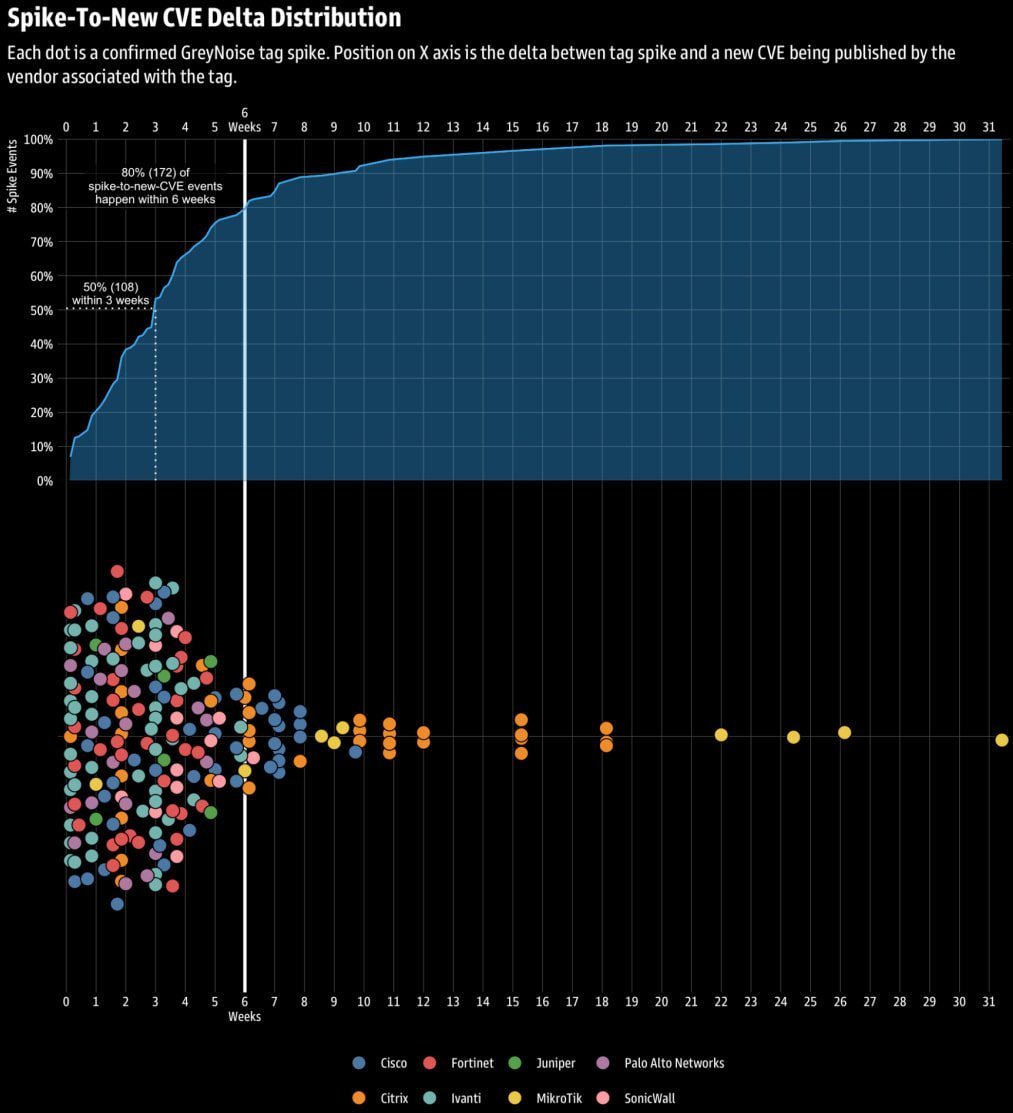
Spike activity and time of disclosure of new CVEs (Source: GreyNoise)
The correlation was particularly strong for products from Ivanti, SonicWall, Palo Alto Networks, and Fortinet, where state-sponsored actors frequently target edge devices for initial network access and persistence. Weaker links appeared with MikroTik, Citrix, and Cisco, though the overarching trend remains a universal red flag.
Why Attackers Trigger These Spikes
Contrary to assumptions, these pre-disclosure surges often involve attackers probing older, known vulnerabilities rather than undiscovered ones. GreyNoise explains that this activity serves dual purposes: it helps catalog exposed endpoints for future attacks and can inadvertently uncover new weaknesses. Researchers describe it as a "mine canary"—seemingly benign scans that signal deeper, impending threats. As such, dismissing this activity as failed breach attempts is a critical mistake. Instead, it represents reconnaissance that lays the groundwork for leveraging novel exploits once CVEs are public.
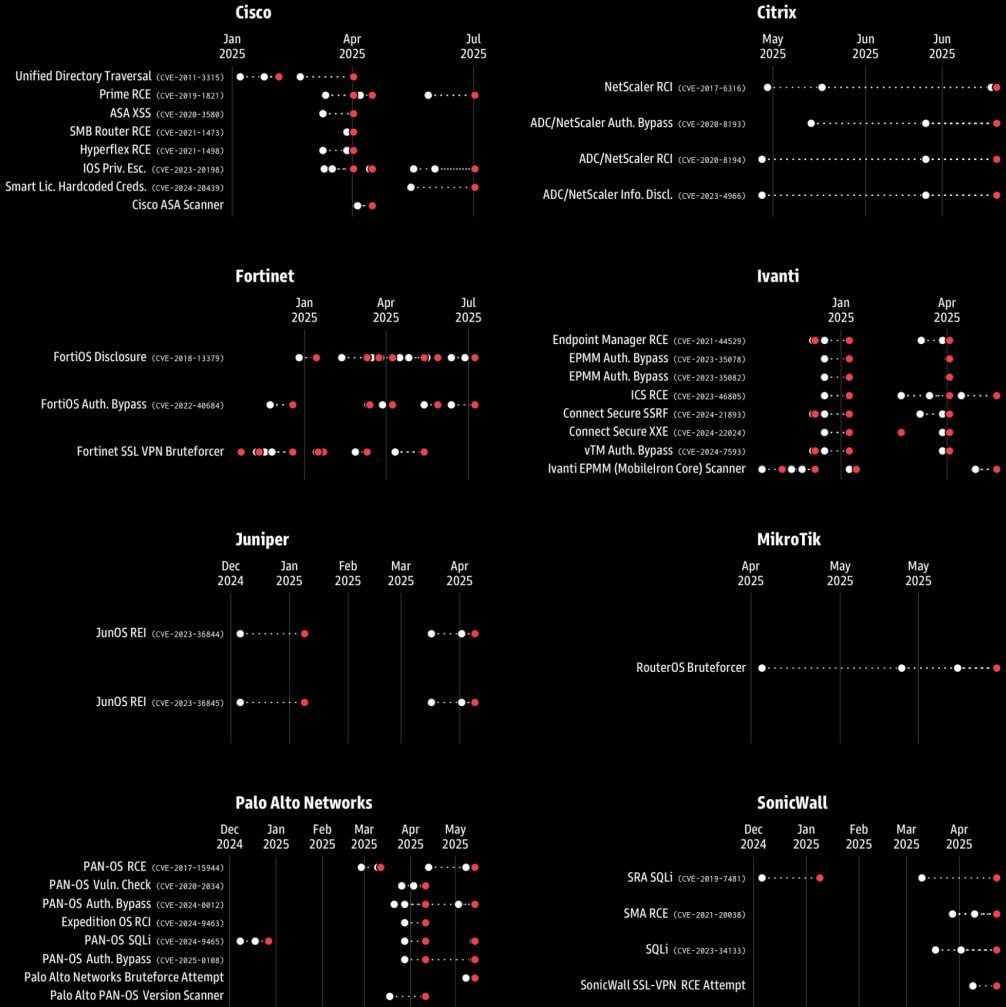
Activity spikes (white) and publication of new CVEs (red) (Source: GreyNoise)
Transforming Defense: From Reactive to Proactive
For security teams, this research is a game-changer. Traditionally, defenses activate only after CVE disclosures, creating a dangerous "patch gap" where attackers capitalize on unmitigated flaws. GreyNoise's findings flip this script, empowering defenders to use malicious spikes as early indicators. Recommendations include:
- Immediate IP Blocking: Quarantine scanning sources to disrupt reconnaissance chains.
- Enhanced Monitoring: Ramp up surveillance of edge devices during spikes, focusing on authentication logs and network traffic anomalies.
- System Hardening: Proactively isolate and fortify vulnerable components, even before specific flaws are known.
In a complementary development, Google's Project Zero has announced it will now disclose basic vulnerability details—such as affected vendors, products, and discovery timelines—within a week of identification, while withholding technical specifics that could aid attackers. This change aims to shrink the patch gap by giving admins advance notice to prepare mitigations.
The New Imperative: Anticipatory Security
GreyNoise's study underscores a broader shift in cybersecurity: the move from reactive firefighting to intelligence-driven anticipation. By treating malicious activity spikes as actionable warnings, organizations can build more resilient defenses, turning attacker behavior into a strategic advantage. In an era where edge devices are prime targets, this predictive approach isn't just innovative—it's essential for survival in the escalating cyber arms race.
Source: Research by GreyNoise, originally reported by BleepingComputer.

Comments
Please log in or register to join the discussion