Security researchers warn that fake Instagram password reset emails are circulating after cybercriminals obtained account data for 17.5 million users through API vulnerabilities, though Meta denies any system breach.
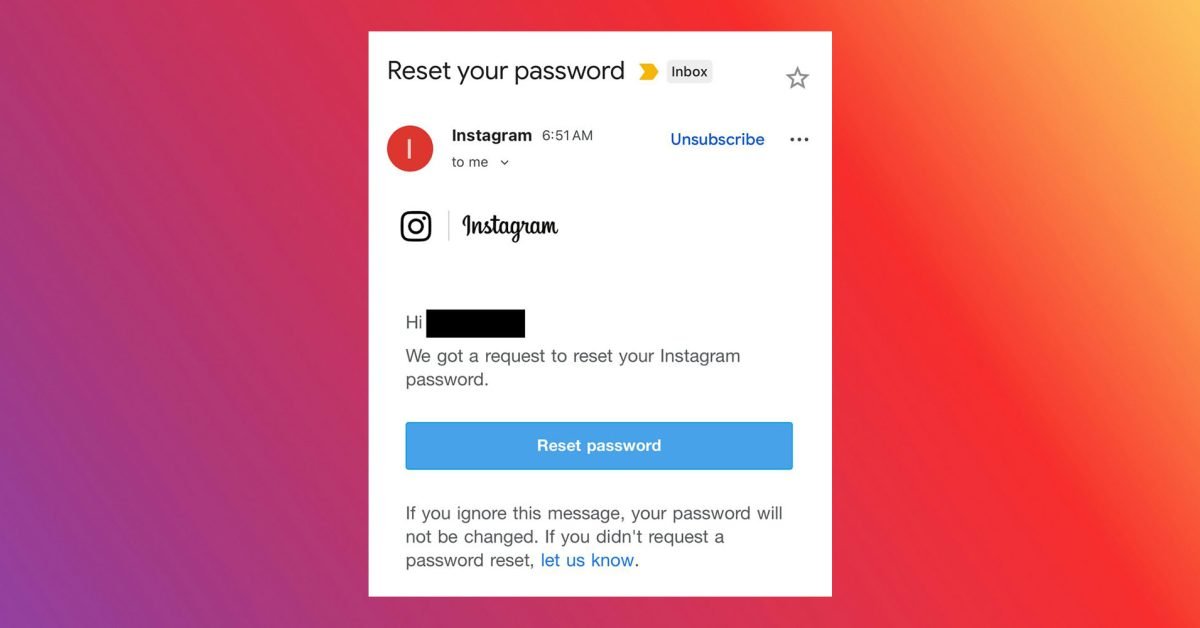
Security researchers at Malwarebytes have issued an alert about a widespread campaign targeting Instagram users through fraudulent password reset emails. If you've received an email claiming Instagram received a password reset request for your account, security experts unanimously advise ignoring it completely. This warning follows the discovery that cybercriminals obtained sensitive account details for approximately 17.5 million Instagram users.
According to Malwarebytes' dark web monitoring, stolen data includes usernames, physical addresses, phone numbers, and email addresses currently being sold to bad actors. The security firm attributes this compromise to an Instagram API vulnerability dating back to 2024 that allowed unauthorized data harvesting. Malwarebytes stated: "We discovered the breach during routine dark web scans tied to a potential incident related to an Instagram API exposure."
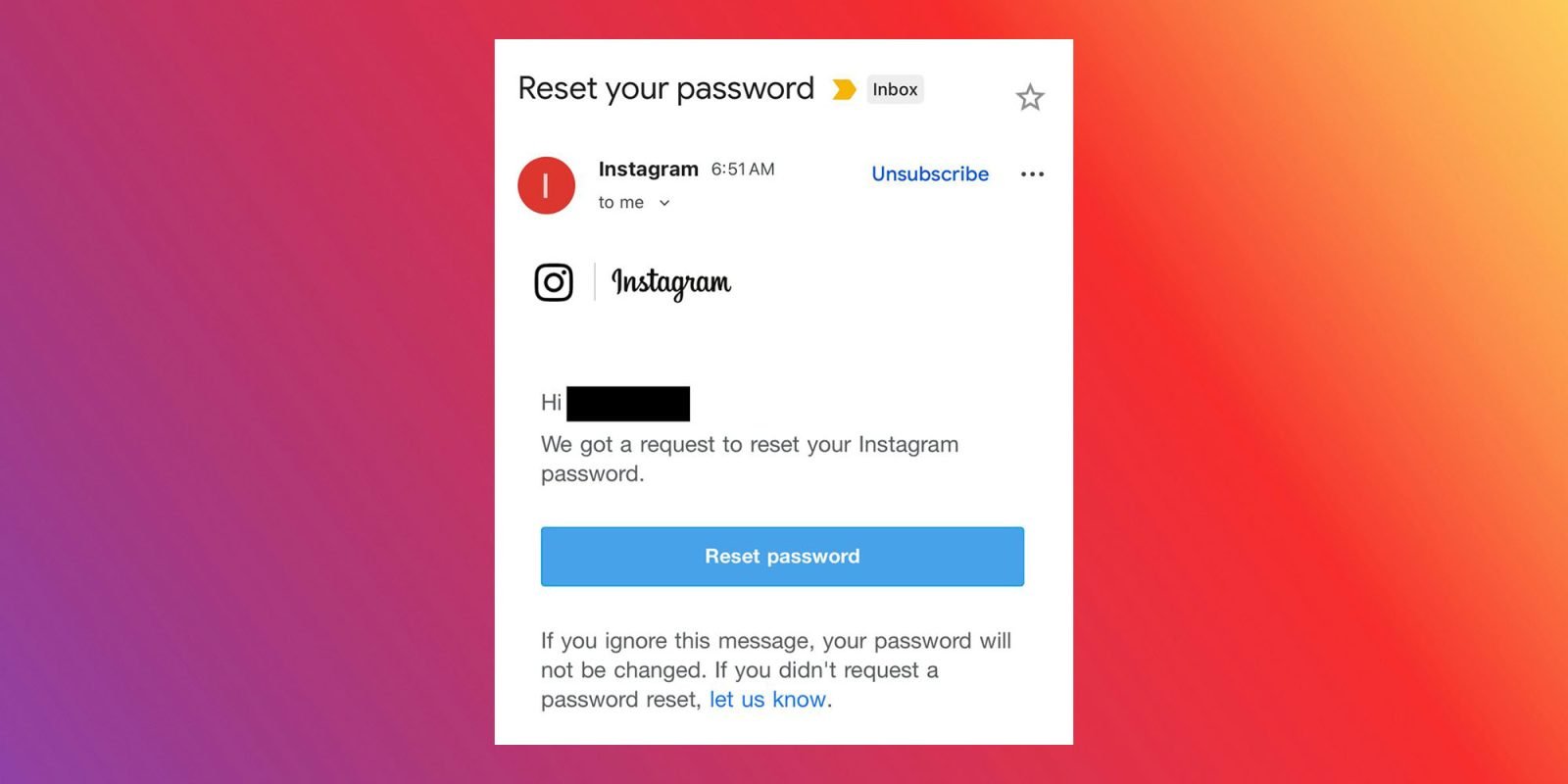
Meta has issued a conflicting statement, denying any breach of its systems: "We fixed an issue that let an external party request password reset emails for some people. There was no breach of our systems and your Instagram accounts are secure. You can ignore those emails." This position hinges on the technical distinction between a system breach and API misuse – where attackers exploited legitimate platform functions rather than hacking servers directly.
For affected users, the practical implications remain significant:
- Never click links in unsolicited password reset emails
- Avoid reusing compromised credentials across services
- Enable two-factor authentication in Instagram's Security settings
- Monitor accounts for suspicious login attempts
Security professionals emphasize heightened phishing risks following such incidents. Attackers often leverage stolen usernames and emails to craft convincing messages impersonating Meta. Always verify requests by logging directly into Instagram through its official app or website – never via email links.

While Meta maintains no passwords were compromised, the scale of exposed personal data creates secondary risks. Security analyst Troy Hunt notes: "Even without password access, attackers use personal details for targeted social engineering or credential stuffing attacks on other platforms where users recycle credentials."
For developers, this incident highlights critical API security considerations:
- Implement strict rate limiting on authentication endpoints
- Audit third-party app permissions regularly
- Monitor API usage patterns for abnormal spikes
- Consider requiring CAPTCHA for sensitive account actions
As investigations continue, users should remain vigilant but not panic. The simplest protection remains the original advice: Delete unexpected password reset requests without engagement. Regularly updating passwords and enabling 2FA provides robust protection regardless of breach origins.
Comments
Please log in or register to join the discussion