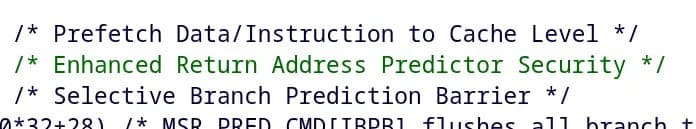
Linux 7.0's KVM hypervisor gains AMD ERAPS virtualization support, enabling guests to fully utilize the enhanced Return Stack Buffer for improved security and performance on Zen 5 processors.
The Linux 7.0 kernel brings significant KVM virtualization enhancements, with one of the most notable additions being support for AMD's Enhanced Return Address Predictor Security (ERAPS) feature. This security technology, introduced with Zen 5 processors, addresses a critical limitation in virtualized environments where guests were previously constrained to using only 32 entries of the Return Stack Buffer (RSB), regardless of the host's capabilities.
With Linux 7.0, KVM now allows virtual machines to access the full 64-entry RSB available on Zen 5 hardware. This enhancement is particularly significant for security-conscious environments and high-performance computing workloads where accurate branch prediction and return address security are paramount. The ERAPS feature helps prevent certain types of return-oriented programming attacks by maintaining a more robust prediction mechanism for return addresses in virtualized contexts.
Beyond ERAPS support, the KVM updates in Linux 7.0 include several other important improvements across different architectures. The x86 implementation now supports giving guests full ownership of Performance Monitoring Unit (PMU) hardware, which enables more accurate performance profiling and debugging within virtual machines. Additionally, there's support for new Intel CPU instructions and various fixes that improve overall stability and compatibility.
The AMD Secure Encrypted Virtualization - Secure Nested Paging (SEV-SNP) implementation also receives attention in this release. The KVM code now includes support for fetching SEV-SNP certificates from user-space, which simplifies the management of encrypted virtual machines and enhances the flexibility of security configurations in cloud and enterprise environments.
LoongArch architecture users will benefit from improved feature detection capabilities and lazy-load support for the Floating Point Unit (FPU) and binary translation register state. These optimizations reduce the overhead associated with context switches and improve the efficiency of virtual machine operations on Loongson processors.
RISC-V KVM sees substantial improvements with support for Zalasr, Zilsd, and Zclsd extensions in guest virtual machines. The addition of transparent huge page support for hypervisor page tables represents a significant performance optimization, reducing the overhead of memory management for large-scale virtualized deployments.
ARM architecture receives preliminary work for guest Generic Interrupt Controller version 5 (GICv5) support, along with various improvements to the protected Kernel-based Virtual Machine (pKVM) implementation. These changes lay the groundwork for enhanced interrupt handling and security features in future ARM-based virtualized environments.
IBM's s390 architecture benefits from improved performance in nested virtualization scenarios and completely new memory management code. These changes are particularly relevant for mainframe virtualization, where nested virtualization is commonly used for testing, development, and multi-tenant environments.
The comprehensive nature of these KVM improvements demonstrates the Linux kernel community's commitment to maintaining KVM as a competitive, feature-rich hypervisor across diverse hardware architectures. The ERAPS support specifically addresses a long-standing limitation in AMD virtualization, bringing Zen 5's security features to their full potential in virtualized environments.
For system administrators and developers working with Linux virtualization, these changes in Linux 7.0 represent meaningful improvements in both security and performance. The ability to leverage the full RSB capacity in virtualized environments, combined with the other architectural improvements, makes Linux 7.0 an attractive option for deploying secure, high-performance virtual machines across various hardware platforms.
Comments
Please log in or register to join the discussion