Attackers compromised a key npm maintainer's account through sophisticated phishing, injecting malicious code into 19 popular packages with over 2.6 billion weekly downloads. The malware hijacks cryptocurrency transactions by rewriting wallet addresses in real-time. This represents one of the largest software supply chain attacks in history, impacting developers globally.

In an unprecedented software supply chain assault, threat actors have compromised 19 critical npm packages with 2.6 billion weekly downloads by hijacking a maintainer's credentials through a meticulously crafted phishing campaign. The attack—confirmed by the compromised maintainer—marks one of the largest-scale ecosystem breaches targeting JavaScript developers.
The Phishing Vector
The attack began with emails impersoning npm's official support, sent from [email protected] (a domain mimicking npmjs.com). The message threatened account suspension unless users "updated" their two-factor authentication credentials:
"Our records indicate that it has been over 12 months since your last 2FA update... Accounts with outdated 2FA credentials will be temporarily locked starting September 10, 2025"
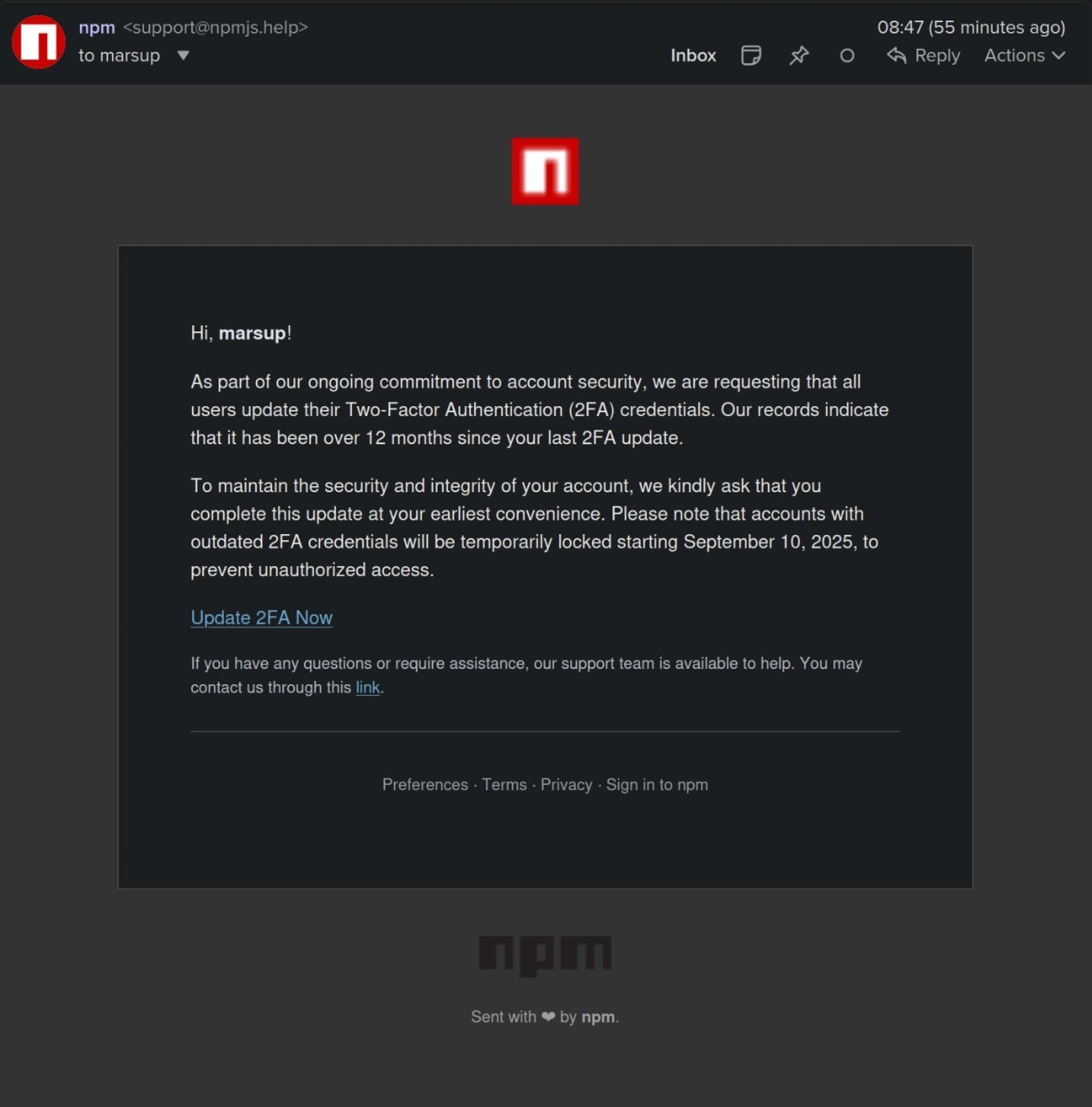 Phishing email used in the attack (Credit: Nicolas Morel)
Phishing email used in the attack (Credit: Nicolas Morel)
Victims who entered credentials on the fake npm login portal had their credentials sent to https://websocket-api2[.]publicvm.com, enabling full account takeover. Multiple maintainers report receiving identical phishing attempts.
Malware Mechanics: Crypto-Jacking in Real-Time
After compromising accounts, attackers injected malicious code into index.js files of high-dependency packages including:
chalk(300M weekly downloads)debug(358M weekly downloads)ansi-styles(371M weekly downloads)supports-color(287M weekly downloads)
// Simplified malware workflow
1. Inject browser interceptor into client-side applications
2. Monitor for crypto transactions (Ethereum, Bitcoin, Solana, etc.)
3. Replace destination wallet addresses with attacker-controlled addresses
4. Hijack transactions before user signing
The malware operates stealthily by:
- Altering website content in real-time
- Tampering with API calls
- Manipulating transaction signing processes
"What makes it dangerous is that it operates at multiple layers," explains Charlie Eriksen of Aikido Security. "It rewrites payment destinations so funds go to attacker accounts without user awareness."
Ecosystem Implications
This attack continues a dangerous trend:
- July 2025:
eslint-config-prettier(30M+ weekly downloads) compromised - March 2025: Ten npm packages converted into info-stealers
With npm hosting over 2.1 million packages, maintainer account security has become the weakest link. The incident exposes critical vulnerabilities in open-source maintenance models where single points of failure can impact billions of installations.
Developer Action Required
Immediate steps for mitigation:
- Audit dependencies for the 19 compromised packages
- Revoke npm publish tokens and enforce mandatory 2FA
- Monitor for suspicious crypto transaction behavior in web apps
The npm security team is investigating, but this breach underscores an urgent need for stronger supply chain safeguards—including artifact signing, automated malware scanning, and maintainer security training. As attacks grow in sophistication, the entire JavaScript ecosystem must confront its collective security responsibility.
Source: Sergiu Gatlan, BleepingComputer

Comments
Please log in or register to join the discussion