Chinese-linked threat group Mustang Panda has updated its COOLCLIENT backdoor, deploying it alongside PlugX and LuminousMoth infections to target government entities across Asia with advanced surveillance capabilities.
Chinese-linked threat actor Mustang Panda has updated its COOLCLIENT backdoor malware and deployed it in a series of cyber espionage campaigns targeting government entities across Asia in 2025, according to new research from Kaspersky.
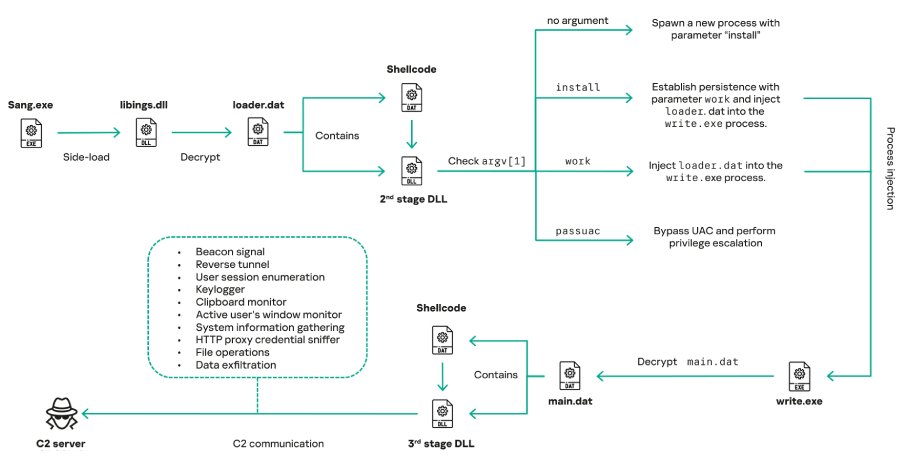
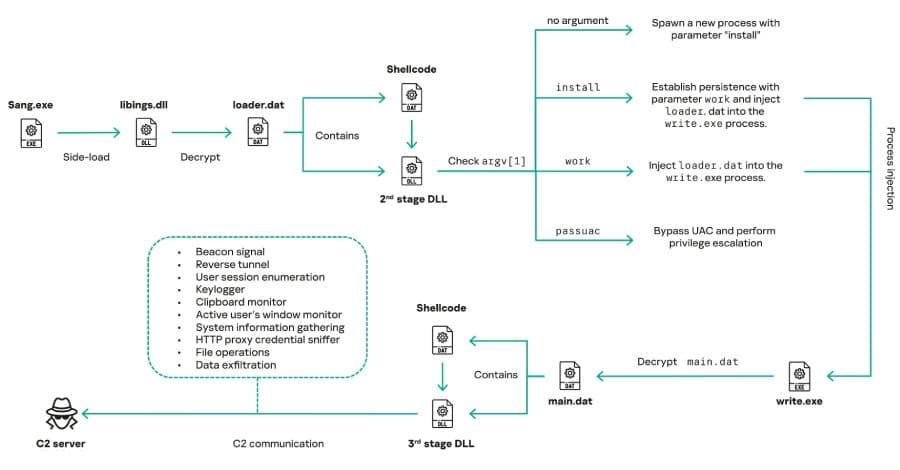
The attacks, which have been observed in Myanmar, Mongolia, Malaysia, and Russia, represent an evolution in Mustang Panda's tactics, with the group leveraging legitimate software for DLL side-loading to deliver the malware alongside encrypted loader files containing shellcode and in-memory DLL modules.
Evolution of COOLCLIENT Deployment
Between 2021 and 2025, Mustang Panda has systematically abused signed binaries from various software products for DLL side-loading attacks. The group has previously used executables from Bitdefender, VLC Media Player, Ulead PhotoImpact, and Sangfor to load malicious DLLs.
"COOLCLIENT was typically delivered alongside encrypted loader files containing encrypted configuration data, shellcode, and in-memory next-stage DLL modules," Kaspersky researchers explained. "These modules relied on DLL side-loading as their primary execution method, which required a legitimate signed executable to load a malicious DLL."
Campaigns observed in 2024 and 2025 have specifically abused legitimate software developed by Sangfor. One notable wave targeted Pakistan and Myanmar, delivering a COOLCLIENT variant that drops and executes a previously unseen rootkit.
Technical Capabilities of COOLCLIENT
The COOLCLIENT backdoor is designed for comprehensive data collection from infected endpoints. Its core functionality includes:
- System and user information gathering
- Keystroke logging
- Clipboard monitoring
- File operations (read, delete, compress, search)
- HTTP proxy credential theft from network traffic
- Reverse tunnel and proxy setup
- Dynamic plugin execution in memory
Supported Plugin Architecture
The malware supports several specialized plugins that extend its capabilities:
- ServiceMgrS.dll: Service management plugin to oversee all services on the victim host
- FileMgrS.dll: File management plugin for enumerating, creating, moving, reading, compressing, searching, or deleting files and folders
- RemoteShellS.dll: Remote shell plugin that spawns a "cmd.exe" process to allow operators to issue commands and capture resulting output
Broader Attack Ecosystem
COOLCLIENT is deployed as part of a larger toolkit that includes multiple stealer programs targeting browser credentials. Mustang Panda has been observed deploying three different stealers to extract saved login credentials from Google Chrome, Microsoft Edge, and other Chromium-based browsers.
In at least one case, the adversary ran a cURL command to exfiltrate the Mozilla Firefox browser cookie file ("cookies.sqlite") to Google Drive. These stealer programs have been detected in attacks against government sectors in Myanmar, Malaysia, and Thailand, suggesting their use in broader post-exploitation efforts.
Connection to Other Malware Families
The COOLCLIENT backdoor shares code-level similarities with a cookie stealer used by LuminousMoth, another malware family associated with Mustang Panda. This suggests potential tool sharing between these operational clusters.
Additionally, Mustang Panda has been identified using batch and PowerShell scripts to gather system information, conduct document theft activities, and steal browser login data.
The group also employs TONESHELL (aka TOnePipeShell), which has been used with varying capabilities to establish persistence and drop additional payloads like QReverse (a remote access trojan with remote shell, file management, screenshot capture, and information gathering features) and a USB worm codenamed TONEDISK.
Attribution and Context
Mustang Panda, also known by multiple aliases including Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Typhoon, has been active since at least 2021. The group's campaigns have historically targeted telecommunications operators, government entities, and organizations across Asia.
COOLCLIENT was first documented by Sophos in November 2022, with Trend Micro subsequently attributing the backdoor to Mustang Panda in 2023. The malware's ability to read/delete files, monitor clipboard and active windows, and execute additional plugins in memory makes it a versatile tool for espionage operations.
Implications for Government Security
The deployment of COOLCLIENT represents a significant escalation in Mustang Panda's capabilities, moving beyond traditional espionage goals toward active surveillance of user activity. The malware's comprehensive monitoring features—including keystroke capture, clipboard data collection, and proxy credential harvesting—indicate a shift toward more intrusive surveillance operations.
Government entities in affected regions should implement enhanced endpoint detection and response capabilities, monitor for suspicious DLL side-loading activities, and maintain strict software supply chain security practices to mitigate the risk of similar attacks.
For organizations concerned about similar threats, implementing application whitelisting, monitoring for unusual network connections, and regularly auditing system logs for signs of lateral movement can help detect and prevent such intrusions.
Comments
Please log in or register to join the discussion