A sophisticated supply chain attack targeting the n8n workflow automation platform has exposed eight malicious packages on the npm registry designed to steal OAuth credentials from developers' systems. The attack exploits the trust model of community integrations to access centralized credential vaults, marking a significant escalation in threats against workflow automation tools that store sensitive API keys and tokens for multiple services.
A new supply chain attack targeting the n8n workflow automation platform demonstrates how threat actors are evolving beyond traditional credential theft to exploit the centralized nature of modern development tools. Security researchers from Endor Labs discovered eight malicious packages on the npm registry that masquerade as legitimate n8n community integrations, with the specific goal of stealing OAuth tokens and API keys stored within these workflow platforms.
The attack represents a fundamental shift in supply chain threats. Rather than targeting individual developer credentials, these malicious packages exploit workflow automation platforms that act as centralized credential vaults. n8n instances typically store OAuth tokens, API keys, and sensitive credentials for dozens of integrated services—including Google Ads, Stripe, and Salesforce—in a single location, making them high-value targets.
The Malicious Packages
The identified packages, which have since been removed from npm, used various naming patterns to appear legitimate:
- n8n-nodes-hfgjf-irtuinvcm-lasdqewriit (4,241 downloads) - Masqueraded as a Google Ads integration
- n8n-nodes-ggdv-hdfvcnnje-uyrokvbkl (1,657 downloads)
- n8n-nodes-vbmkajdsa-uehfitvv-ueqjhhhksdlkkmz (1,493 downloads)
- n8n-nodes-performance-metrics (752 downloads)
- n8n-nodes-gasdhgfuy-rejerw-ytjsadx (8,385 downloads)
- n8n-nodes-danev (5,525 downloads)
- n8n-nodes-rooyai-model (1,731 downloads)
- n8n-nodes-zalo-vietts (4,241 downloads)
The most downloaded package, "n8n-nodes-gasdhgfuy-rejerw-ytjsadx," reached 8,385 installations before detection. Authors behind these packages—using aliases like "kakashi-hatake," "zabuza-momochi," "dan_even_segler," and "diendh"—have also published other suspicious packages that remain available on npm, including:
- n8n-nodes-gg-udhasudsh-hgjkhg-official (2,863 downloads)
- n8n-nodes-danev-test-project (1,259 downloads)
- @diendh/n8n-nodes-tiktok-v2 (218 downloads)
- n8n-nodes-zl-vietts (6,357 downloads)
Attack Mechanism
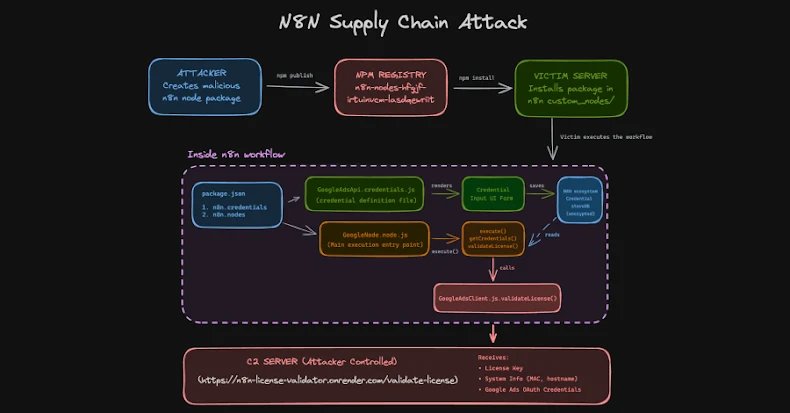
The malicious packages operate as legitimate n8n integrations, displaying proper configuration screens and saving credentials in encrypted format to the n8n credential store. This behavior makes detection difficult during initial testing. The attack unfolds in several stages:
- Installation: Developers install the package believing it's a legitimate integration
- Configuration: The package presents a configuration interface that appears authentic
- Credential Storage: OAuth tokens are saved in encrypted format to n8n's credential store
- Exfiltration: When the workflow executes, the malicious code decrypts tokens using n8n's master key and sends them to attacker-controlled servers
This approach exploits a critical architectural weakness: community nodes run with the same privileges as n8n itself. According to Endor Labs researchers Kiran Raj and Henrik Plate, "There is no sandboxing or isolation between node code and the n8n runtime."
Why This Attack Is Significant
The n8n attack represents several important escalations in supply chain security:
1. Targeting Credential Aggregators: Instead of stealing individual credentials, attackers target platforms that centralize access to multiple services. A single compromised n8n instance can yield credentials for Google Ads, Stripe, Salesforce, and other critical services.
2. Exploiting Trust Models: Community nodes rely on trust in the package author and review process. The attackers weaponized this trust by creating packages that appear functional while hiding malicious behavior.
3. Persistent Access: Once OAuth tokens are stolen, attackers can maintain access to connected services even after the malicious package is removed, unless tokens are explicitly revoked.
4. Difficult Detection: The malicious behavior only triggers during workflow execution, making static analysis insufficient. The packages pass basic security scans because the malicious code is obfuscated or triggered by specific conditions.
Security Implications for n8n Users
The attack exposes fundamental security issues with n8n's community node architecture:
- File System Access: Malicious nodes can read and write files on the host system
- Environment Variable Access: All n8n environment variables are accessible
- Network Access: Unrestricted outbound connections to exfiltrate data
- Credential Decryption: Direct access to decrypted API keys and OAuth tokens during execution
- No Isolation: Complete integration with n8n's runtime environment
As the Endor Labs researchers noted: "For attackers, the npm supply chain offers a quiet and highly effective entry point into n8n environments."
Recommended Mitigations
For Self-Hosted n8n Instances
Immediate Actions:
Disable Community Nodes: Set the environment variable
N8N_COMMUNITY_PACKAGES_ENABLEDtofalseto prevent installation of community packagesAudit Existing Installations: Review all installed community nodes and remove any that appear suspicious or are not actively used
Revoke and Rotate Credentials: For any potentially compromised n8n instance:
- Revoke all OAuth tokens for connected services
- Generate new API keys and credentials
- Update all workflows with new credentials
Review Workflow Logs: Check execution logs for unexpected network connections or file access patterns
For Cloud Users
- Contact n8n support to verify if your instance may have been affected
- Monitor connected service accounts for unauthorized access
- Consider temporarily disabling workflows that use community nodes
Long-term Best Practices
Package Evaluation:
- Scrutinize Metadata: Check package author names, publication dates, and download counts. New packages from unknown authors warrant extra caution
- Review Source Code: For critical integrations, examine the actual code before installation
- Prefer Official Integrations: Use only packages from verified n8n maintainers when possible
- Check for Security Scans: Verify packages have been scanned by tools like ReversingLabs Spectra Assure
Architectural Considerations:
- Credential Segregation: Consider using separate n8n instances for different sensitivity levels
- Network Segmentation: Restrict outbound network access from n8n execution environments
- Monitoring: Implement logging and alerting for unusual workflow behavior
- Regular Audits: Schedule periodic reviews of all installed packages and their permissions
Broader Industry Context
This attack highlights a growing trend where threat actors target platforms that aggregate access to multiple services. Similar attacks have affected:
- CI/CD platforms: Compromised build tools can access deployment credentials
- Package managers: Malicious libraries can steal environment variables
- Development tools: Extensions and plugins with broad system access
The n8n case is particularly concerning because workflow automation platforms are increasingly used to orchestrate critical business processes. A successful attack can compromise:
- Financial services (payment processing, accounting)
- Marketing operations (ad platforms, analytics)
- Customer relationship management (CRM systems)
- Internal business logic (database access, API integrations)
Detection and Response
Organizations using n8n should implement the following detection mechanisms:
Network Monitoring:
- Monitor for outbound connections from n8n instances to unknown domains
- Alert on large data transfers from n8n servers
- Track API calls to integrated services for anomalous patterns
File System Monitoring:
- Watch for unexpected file reads in n8n directories
- Monitor for new executable files in workflow directories
Credential Monitoring:
- Track OAuth token usage patterns
- Alert on authentication failures from integrated services
- Monitor for credential access attempts outside normal workflow execution
Conclusion
The n8n supply chain attack represents a maturation of supply chain threats, moving from individual credential theft to exploiting platforms that centralize access to multiple services. For organizations using workflow automation tools, this underscores the need to treat these platforms as critical infrastructure requiring robust security controls.
The attack's success relies on a fundamental trust assumption: that community-contributed packages are safe. While community ecosystems provide valuable functionality, they also introduce significant risk when those packages have broad system access without proper isolation.
Organizations should immediately audit their n8n installations, disable community nodes if not strictly necessary, and implement comprehensive monitoring. More broadly, this incident should prompt evaluation of security controls for any platform that aggregates credentials or provides broad system access to third-party extensions.
The npm registry has removed the identified packages, but the authors remain active. Security teams should continue monitoring for new malicious packages targeting n8n and similar workflow automation platforms.
References:
Comments
Please log in or register to join the discussion