New scans reveal 266,000+ internet-exposed F5 BIG-IP appliances as federal agencies scramble to patch critical vulnerabilities following F5's admission that nation-state hackers stole source code and exploit details. CISA mandates emergency updates amid fears of imminent attacks.

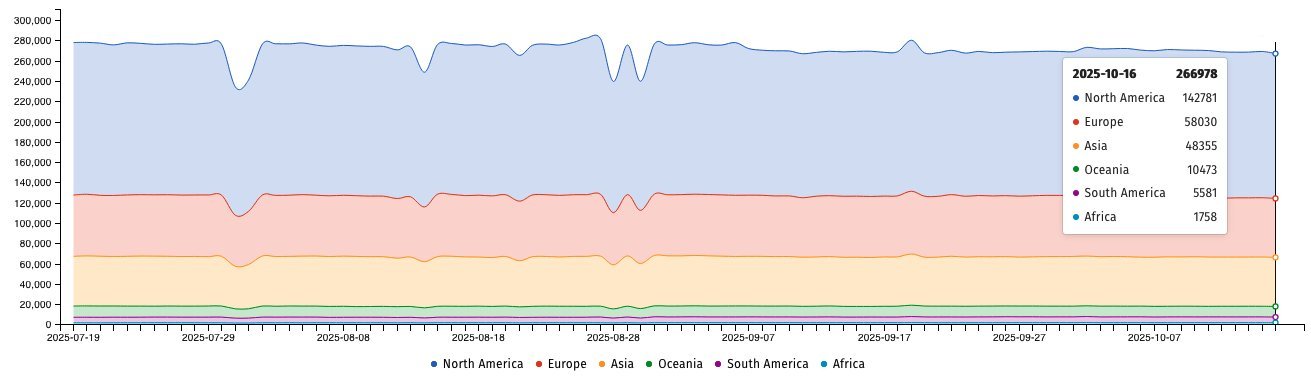
Internet scanning by the Shadowserver Foundation has identified 266,978 publicly exposed F5 BIG-IP instances globally, with over 142,000 in the United States alone. This discovery follows F5's disclosure that nation-state attackers breached its internal networks, stealing sensitive source code and details about unpatched vulnerabilities in its flagship application delivery controllers.
Critical Infrastructure Under Siege
F5 confirmed the breach on Wednesday, revealing attackers operated undetected for over a year before exfiltrating proprietary data. While the company stated there's "no evidence" of weaponized exploits currently, it simultaneously released patches for 44 vulnerabilities across its BIG-IP, F5OS, and BIG-IQ product lines.
"Though we have no knowledge of undisclosed critical or remote code execution vulnerabilities, we strongly advise updating your BIG-IP software as soon as possible," F5 warned customers.
Internal advisories seen by Bloomberg attribute the attack to China-linked UNC5291—a threat group notorious for exploiting Ivanti zero-days earlier this year. F5's threat-hunting guide references Brickstorm, a Golang backdoor previously deployed by UNC5291 to maintain persistence in compromised networks.
Federal Emergency Directive Issued
 F5 BIG-IP exposure heatmap (Source: Shadowserver)
F5 BIG-IP exposure heatmap (Source: Shadowserver)
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) responded with an emergency directive ordering federal agencies to:
- Patch all internet-facing F5 systems by October 22
- Decommission end-of-life appliances by October 31
- Inventory all F5 products and isolate management interfaces
Why BIG-IP Compromises Are Catastrophic
F5 appliances sit at the nerve center of enterprise networks—handling traffic routing, SSL decryption, and authentication for 48 of the Fortune 50 companies. A single compromised BIG-IP system enables attackers to:
- Steal credentials and API keys
- Pivot laterally across networks
- Deploy ransomware or wipers
- Eavesdrop on encrypted traffic
Security researchers note that F5 vulnerabilities have become prime targets for both nation-states and ransomware groups. The massive attack surface revealed by Shadowserver—particularly in financial services, government, and critical infrastructure—creates ripe conditions for exploitation of the stolen vulnerability intelligence.
F5 customers face a binary choice: patch immediately or risk becoming the next victim of credential harvesting, data exfiltration, or network takeover. With UNC5291's history of rapid weaponization, the countdown to active exploitation has likely already begun.
Source: BleepingComputer

Comments
Please log in or register to join the discussion