Spanish tech retailer PcComponentes denies hacker claims of a 16-million record breach but confirms credential stuffing attacks compromised customer accounts, prompting new security measures.

Spanish tech retailer PcComponentes has publicly refuted claims by a hacker known as 'daghetiaw' who purported to have stolen 16.3 million customer records from the company's systems. In an official statement, the company confirmed investigating the alleged breach but found no evidence of unauthorized database access, stating that "the figure of 16 million supposedly affected customers is false" since their active user base is significantly smaller.
The hacker had leaked 500,000 records on cybercrime forums 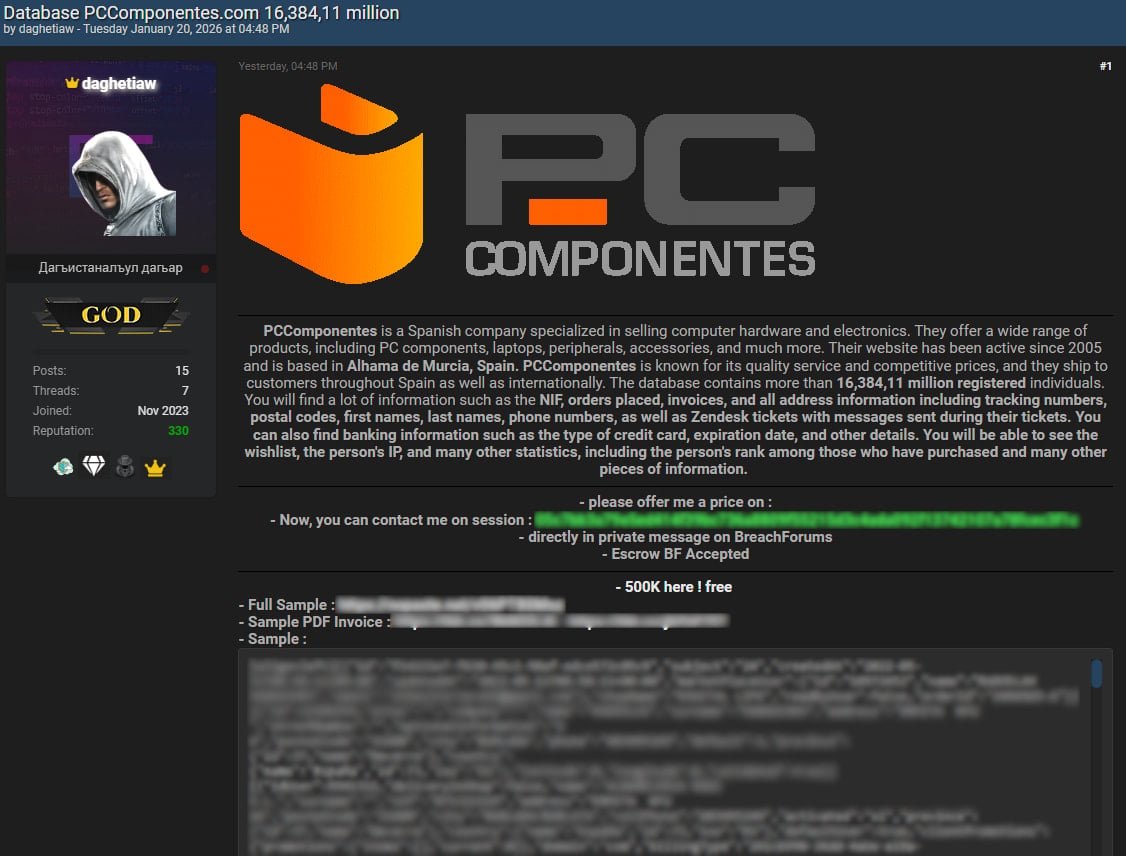 and offered the remaining data for sale. Samples included order details, physical addresses, full names, phone numbers, IP addresses, product wish-lists, and customer support messages exchanged via Zendesk. PcComponentes emphasized that financial data and passwords weren't exposed since they aren't stored on their systems.
and offered the remaining data for sale. Samples included order details, physical addresses, full names, phone numbers, IP addresses, product wish-lists, and customer support messages exchanged via Zendesk. PcComponentes emphasized that financial data and passwords weren't exposed since they aren't stored on their systems.
Threat intelligence firm Hudson Rock provided crucial context, revealing that the leaked credentials likely originated from historical infostealer malware infections rather than a fresh breach. "Every single email we checked from the threat actor's sample was found in existing infostealer logs," their analysis noted. Some compromised credentials dated back to 2020, suggesting attackers collected login pairs from infected devices over several years.
PcComponentes confirmed attackers exploited these credentials through automated credential stuffing attacks - systematically testing stolen username/password combinations from other breaches against their login portal. This resulted in unauthorized access to some accounts, exposing:
- First and last names
- National ID numbers
- Physical addresses
- IP addresses
- Email addresses
- Phone numbers
In response, the retailer implemented layered defenses:
- Added CAPTCHA verification on all login pages
- Made two-factor authentication (2FA) mandatory for all accounts
- Invalidated all active user sessions
- Automatically logged out all customers
Security experts emphasize these practical protections:
- Enable 2FA immediately: PcComponentes now requires this, but users should activate it across all sensitive accounts
- Use unique passwords: Password managers like Bitwarden or KeePass prevent credential reuse
- Monitor account activity: Watch for suspicious logins using tools like Have I Been Pwned
- Verify phishing attempts: Treat unexpected emails referencing PcComponentes orders with suspicion
The company hasn't disclosed exact numbers of compromised accounts but confirmed the impact is substantially smaller than the hacker's claims. This incident highlights how credential stuffing attacks exploit poor password hygiene across multiple services, turning minor breaches elsewhere into access to high-value accounts.

Comments
Please log in or register to join the discussion