A critical flaw in the popular Post SMTP WordPress plugin allows low-privileged users to access email logs and hijack administrator accounts. With over half of installations still unpatched, this exposes widespread risks in third-party plugin security and update practices.

A medium-severity vulnerability (CVE-2025-24000) in the Post SMTP plugin—used by over 400,000 WordPress sites—has left approximately 200,000 websites susceptible to complete administrative takeover. The flaw, discovered by a researcher and reported to PatchStack on May 23, stems from inadequate access controls in the plugin's REST API endpoints. Unlike typical security checks that validate user roles, Post SMTP versions up to 3.2.0 only verified login status, allowing even low-privileged subscribers to view sensitive email logs.
How the Exploit Unfolds
Attackers can leverage this flaw in a straightforward but devastating chain: A subscriber initiates a password reset for an administrator account, intercepts the reset email via the exposed logs, and uses it to seize control. This bypasses WordPress's core security layers, turning a routine function into a weapon. As one expert from PatchStack noted, "Broken access control remains a top vector for web attacks, especially in plugins handling critical infrastructure like email."
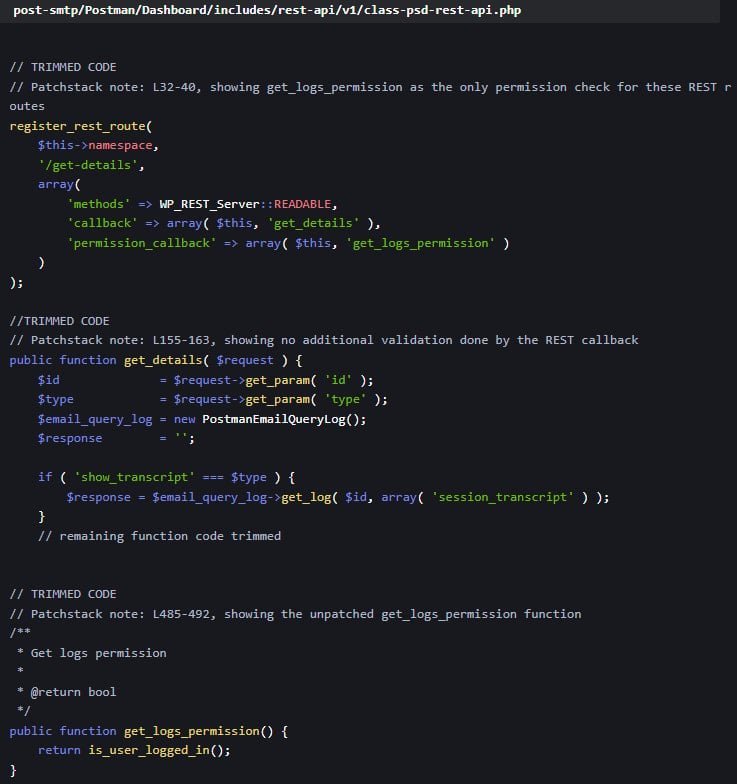 The vulnerable code snippet in Post SMTP's permissions function, which lacked role-based checks. (Source: PatchStack)
The vulnerable code snippet in Post SMTP's permissions function, which lacked role-based checks. (Source: PatchStack)
Patch and Persistent Risks
Developer Saad Iqbal addressed the issue by adding privilege validations in the get_logs_permission function, releasing a fix in version 3.3.0 on June 11. Despite this, WordPress.org data shows only 48.5% of users have updated, leaving 200,000+ sites exposed. Alarmingly, 24.2% (96,800 sites) run outdated 2.x versions, which harbor additional unpatched vulnerabilities. This lag underscores a troubling pattern in WordPress ecosystems, where convenience often trumps security hygiene.
Why This Matters for Developers
Beyond the immediate threat, this incident highlights systemic challenges:
- Supply Chain Risks: Plugins like Post SMTP, which replace core functions (e.g.,
wp_mail()), become single points of failure. A compromise here can cascade across entire sites. - Update Fatigue: With 51.5% of users delaying patches, automated update mechanisms and monitoring are non-negotiable for administrators.
- API Security: The flaw exemplifies why REST endpoints must enforce strict role-based access, not just authentication.
As the WordPress plugin economy grows, this breach serves as a stark reminder that trust in third-party tools demands rigorous vetting and proactive maintenance. For now, administrators should immediately upgrade to Post SMTP 3.3.0 and audit user privileges—because in cybersecurity, complacency is the real vulnerability.
Source: BleepingComputer

Comments
Please log in or register to join the discussion