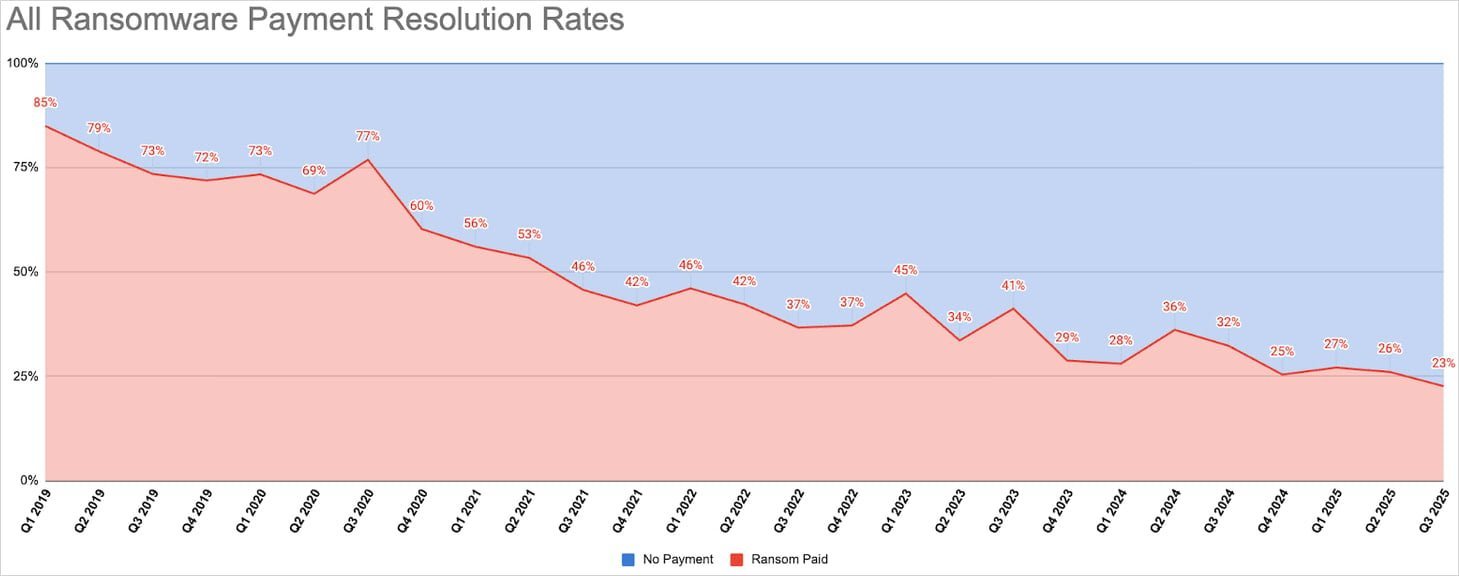
Ransomware profits have plummeted to unprecedented levels with only 23% of breached organizations paying attackers in Q3 2025. This six-year downward trend reflects improved cyber defenses and a strategic shift toward data exfiltration by threat actors. Security teams now face evolved tactics targeting mid-sized businesses through social engineering and software vulnerabilities.
The Unraveling Ransomware Economy: Why Hackers Are Losing Leverage

Ransomware gangs are facing an existential crisis as payment rates from victims collapse to just 23%—the lowest level ever recorded. According to Coveware's Q3 2025 threat report, this marks the culmination of a six-year downward trend accelerated by hardened enterprise defenses and global pressure against funding cybercriminals.
"Cyber defenders, law enforcement, and legal specialists should view this as validation of collective progress," states the report. "Each avoided payment constricts cyber attackers of oxygen."
The Data Exfiltration Pivot
The economics of ransomware have fundamentally shifted. With 76% of attacks now involving data theft—up from 58% in 2023—double extortion has become the norm. Yet this strategy is yielding diminishing returns: When attackers only steal data without encryption, payment rates plunge to 19%.
Average ransom payments fell to $377,000 (median: $140,000) as enterprises redirect funds toward prevention. "Large organizations recognize that ransom money is better spent strengthening defenses," the report notes, highlighting a strategic recalibration of security budgets.
Attackers Adapt: Precision Targeting and New Vectors
Facing revenue shortfalls, ransomware groups like Akira and Qilin—responsible for 44% of Q3 attacks—are shifting focus toward mid-sized companies deemed more likely to pay. Initial access vectors have also evolved dramatically:
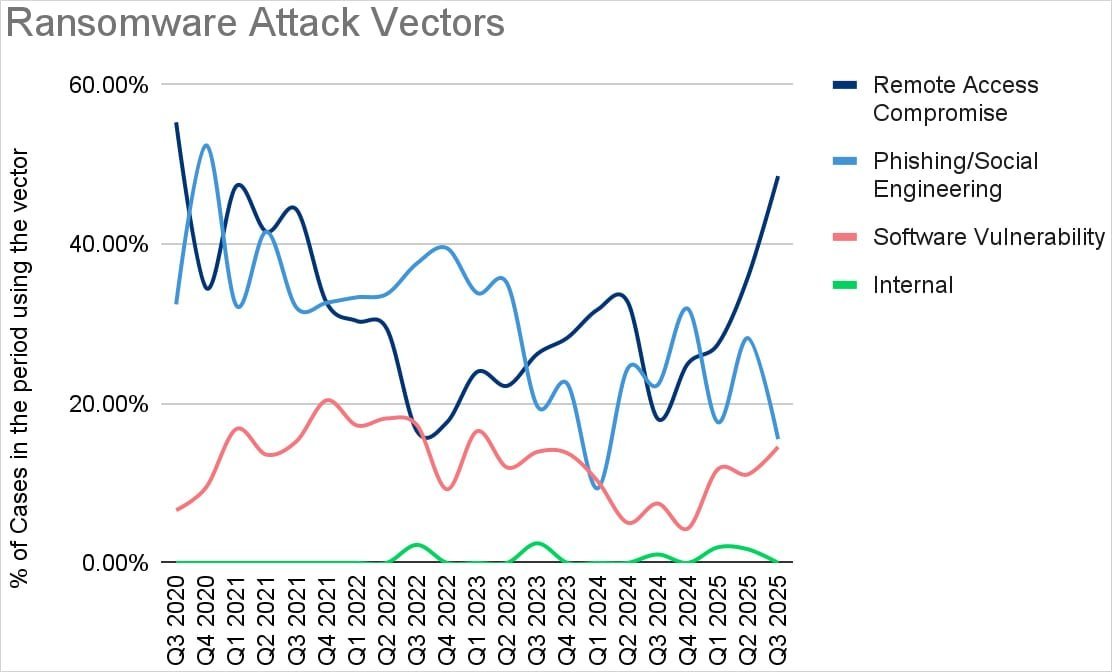
- Remote access compromises now lead at 32% of incidents
- Exploitation of software vulnerabilities surged by 87% year-over-year
- Email phishing declined as MFA adoption increased
Coveware warns that shrinking profits will drive more aggressive tactics: "Threat actors are likely to rely more on social engineering and insider recruitment, offering large bribes for initial access."
The Resilience Imperative
While the payment decline signals progress, the battlefield is transforming. Defenders must now prioritize:
- Data-centric security with robust encryption and access controls
- Vulnerability management for rapidly patching exploits
- Insider threat programs to counter bribed employees
As ransomware gangs hunt for oxygen in an increasingly arid landscape, security teams’ success hinges on sustaining pressure through technical resilience and refusing to fund criminal ecosystems.
Source: Coveware Q3 2025 Ransomware Report, BleepingComputer

Comments
Please log in or register to join the discussion