A webinar examining the security risks of agentic AI systems, focusing on Machine Control Protocols (MCPs), shadow API key management, and practical controls for securing AI agents without slowing development.
The security landscape shifted dramatically when AI agents evolved from simple code suggestions to autonomous execution. Tools like Copilot, Claude Code, and Codex now build, test, and deploy software end-to-end in minutes. This acceleration creates a security gap that most teams don't recognize until automation becomes an attack vector.
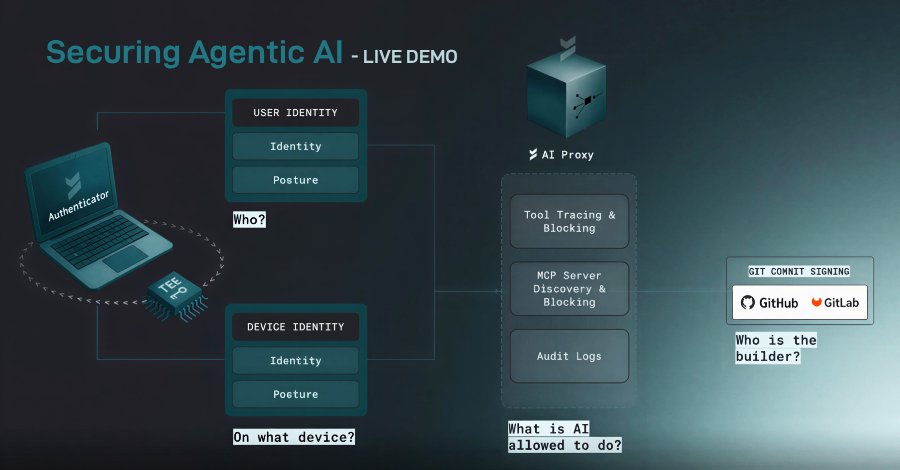
The MCP Control Plane Problem
Behind every agentic workflow sits the Machine Control Protocol (MCP) layer—systems that quietly decide what an AI agent can run, which tools it calls, which APIs it accesses, and what infrastructure it touches. When that control plane is compromised or misconfigured, the agent doesn't just make mistakes; it acts with authority across your entire stack.
The CVE-2025-6514 incident demonstrated this risk clearly. A flaw in a trusted OAuth proxy used by over 500,000 developers created a remote code execution path. No exotic exploit chain required. No noisy breach needed. Just automation doing exactly what it was allowed to do—at scale.
This incident reveals a fundamental truth: if an AI agent can execute commands, it can also execute attacks.
Why Traditional Identity Models Fail
Conventional identity and access management breaks down when agents act on your behalf. The webinar "Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl" addresses this gap directly. Led by the author of the OpenID whitepaper "Identity Management for Agentic AI," the session explores:
What You'll Learn
MCP Server Architecture: Understanding how MCP servers function in real environments reveals why they matter more than the model itself. These servers become the critical control point where security policy must be enforced.
Attack Surface Transformation: Malicious or compromised MCPs turn automation into an attack surface. The webinar demonstrates how these systems can be weaponized and what that means for your security posture.
Shadow API Key Proliferation: The sources of shadow API keys and detection methods. These credentials multiply silently when agents create new access tokens, store credentials in unexpected locations, or inherit permissions through nested tool calls.
Audit and Policy Enforcement: Practical approaches to auditing agent actions and enforcing policy before deployment, ensuring you maintain visibility and control.

The Sprawl Problem
Shadow API keys emerge from multiple vectors in agentic workflows:
- Tool Integration: When agents connect to new services, they often generate API keys that aren't tracked by central credential management
- Nested Execution: Agent tool calls can create temporary credentials that persist beyond the immediate task
- Developer Convenience: Teams may embed keys directly in agent configurations to bypass friction
- Credential Inheritance: Sub-agents or tools may receive copies of parent credentials without proper scoping
Traditional discovery methods fail because these keys don't exist in standard inventory systems. They live in agent configurations, tool caches, and temporary execution contexts.
Practical Controls Without Development Friction
The webinar focuses on controls that secure agentic AI without slowing development:
1. MCP Server Hardening
Treat MCP servers as critical infrastructure. Implement:
- Strict capability whitelisting
- Network segmentation
- Runtime monitoring
- Integrity verification
2. Credential Scoping and Rotation
- Use short-lived credentials with automatic expiration
- Implement principle of least privilege for each agent task
- Deploy credential vaults with agent-specific access policies
- Monitor for credential usage anomalies
3. Action Auditing
- Log every tool call, API access, and infrastructure change
- Establish baseline behavior patterns
- Implement real-time alerting for policy violations
- Create immutable audit trails for compliance
4. Pre-Deployment Policy Enforcement
- Scan agent configurations for exposed credentials
- Validate MCP permissions against organizational policies
- Test agent behavior in sandboxed environments
- Require security review for agents with infrastructure access

The Visibility Gap
Most organizations can't answer fundamental questions about their agentic AI:
- Which agents have access to production systems?
- What APIs can each agent call?
- Where are credentials stored and how are they rotated?
- What happens when an agent receives a malicious prompt?
This visibility gap becomes more dangerous as agentic AI adoption accelerates. The webinar provides frameworks for closing this gap without creating bureaucratic overhead.
Moving Forward
Agentic AI is already inside your pipeline. The question isn't whether to adopt these tools—it's whether you can see what they're doing and stop them when they go too far.
The security controls discussed in this webinar provide a path forward: secure the MCP control plane, eliminate shadow credentials, audit agent actions, and enforce policy without blocking innovation.
Registration Details
The webinar "Securing Agentic AI: From MCPs and Tool Access to Shadow API Key Sprawl" offers practical guidance for teams navigating this new security landscape. Registration is available for the live session, which will include demonstrations of real-world attack scenarios and defensive strategies.
For organizations already deploying agentic AI, this session provides immediate actionable controls. For those planning adoption, it offers a security-first framework that prevents the accumulation of technical debt and risk.
The automation revolution doesn't have to mean security chaos. But it does require rethinking how we secure systems that can write, test, and deploy their own code.
This webinar addresses the critical intersection of AI automation and cybersecurity, providing security teams with the knowledge needed to maintain control as agentic systems become standard development infrastructure.
Comments
Please log in or register to join the discussion