The Kyowon Group, a major South Korean conglomerate with over 9.6 million registered accounts, has confirmed that attackers exfiltrated data during a ransomware attack that crippled approximately 600 of its 800 servers. The incident, which occurred on January 14th, represents the latest in a string of high-profile breaches targeting South Korean companies and raises serious questions about the exposure of sensitive customer information across the country's digital infrastructure.
The Kyowon Group, one of South Korea's largest conglomerates spanning education, publishing, digital learning tools, and hospitality services, has officially confirmed that attackers stole data during a ransomware attack that struck its infrastructure on January 14, 2026. The breach, which began around 10 a.m. local time, has impacted approximately 600 out of the company's 800 servers, representing a catastrophic 75% infrastructure compromise.
Attack Scope and Impact
Kyowon's initial response came after customers noticed widespread service outages earlier this week. The company immediately notified Korea's Internet & Security Agency (KISA) and began working with external security experts to assess the damage. According to Korean media reports, the scale is staggering: over 9.6 million registered accounts, corresponding to approximately 5.5 million individual users, may have had their personal information exposed to threat actors.
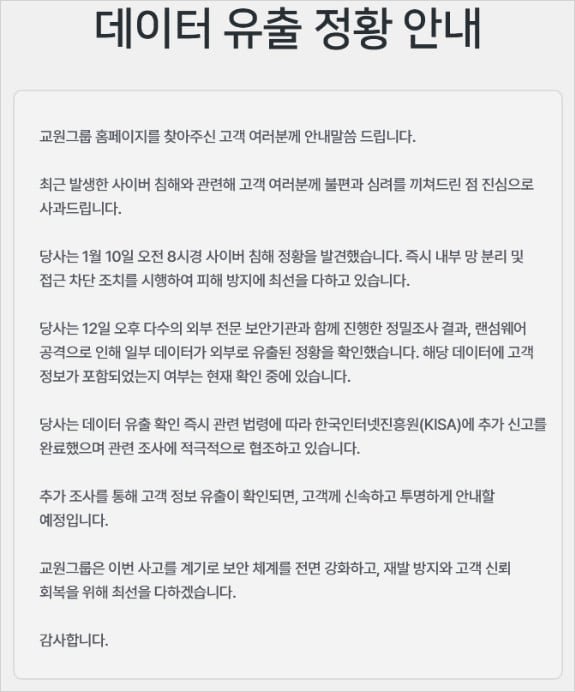
The company's latest statement, published on their official website, confirms data exfiltration but stops short of definitively stating whether customer information was among the stolen records:
"The KyoWon Group has confirmed the existence of an external data leak and is conducting a detailed investigation in cooperation with relevant authorities and security experts to determine whether customer information was actually included. If the leak is confirmed, the company plans to provide transparent information."
The South Korean Breach Pattern
The Kyowon incident is not isolated. It fits into a disturbing pattern of large-scale cyberattacks targeting major South Korean corporations throughout 2025 and early 2026:
- December 2025: E-commerce giant Coupang suffered a breach affecting 33.7 million customers, later traced to an ex-employee who retained system access
- Late 2025: Korean Air exposed staff information in a cybersecurity incident
- May 2025: SK Telecom disclosed a malware breach dating back to 2022 that exposed USIM data for 27 million subscribers
- May 2025: Luxury brand Dior's Korean operations leaked customer order information
This cascade of breaches suggests systemic vulnerabilities across South Korea's digital infrastructure, particularly affecting companies that hold vast repositories of citizen data.
Technical Implications and Restoration Efforts
Kyowon is currently working to restore its online services, with the company reporting that restoration efforts are in their "final stages." However, the 75% server compromise rate indicates that attackers had sustained, privileged access to the network before deployment of the ransomware payload.
The absence of a ransomware group claim as of this writing is noteworthy. Several possibilities exist:
- Negotiations in progress: The attackers may be in direct negotiations with Kyowon
- Independent threat actors: The attack could be the work of a lesser-known or new group
- False flag operation: The ransomware may have been deployed to obscure a different motive (espionage, sabotage)
- Law enforcement pressure: Groups increasingly avoid public claims to reduce attention
What Customers Should Monitor
For the millions potentially affected, the immediate concern is the type of data that may have been exfiltrated. As an education and publishing conglomerate with digital learning tools, Kyowon likely holds:
- Personal Identifiable Information (PII): Names, birthdates, addresses, phone numbers
- Educational records: Student performance data, learning progress, assessment results
- Payment information: Credit card details, billing addresses for subscription services
- Authentication credentials: Hashed passwords, security questions, account recovery data
- Family information: Parent/guardian details linked to child accounts
Practical Security Measures for Affected Users
Until Kyowon provides definitive confirmation about what data was stolen, customers should take these precautionary steps:
Immediate Actions:
- Change passwords for any Kyowon accounts and any other accounts using the same credentials
- Enable multi-factor authentication where available
- Monitor financial statements for unusual activity
- Be vigilant for phishing attempts referencing Kyowon services
Medium-term Monitoring:
- Sign up for breach notification services like Have I Been Pwned
- Consider credit monitoring if payment information was stored
- Watch for official Kyowon communications about the breach scope
Broader Lessons for Enterprise Security
The Kyowon breach highlights several critical enterprise security gaps:
1. Employee Access Management: The Coupang breach demonstrated that former employees retaining access is a real threat. Kyowon's attack vector remains unknown, but insider threats and privilege creep are common in large organizations.
2. Server Segmentation: With 600 of 800 servers compromised, the attack suggests inadequate network segmentation. In a properly segmented environment, ransomware should not be able to propagate across the entire infrastructure.
3. Backup Strategy: The company's ability to restore services suggests they had backups, but the timeline indicates restoration is complex. Organizations need immutable, offline backups that can be restored quickly.
4. Detection Gaps: The attack was discovered after service outages became apparent, suggesting that detection mechanisms failed to identify the initial compromise or data exfiltration in progress.
What Comes Next
Kyowon faces a critical 72-hour window under South Korea's Personal Information Protection Act to report the breach details to authorities if customer data is confirmed stolen. The company has promised transparency, but the actual scope may take weeks to fully determine.
For security professionals, this incident serves as another reminder that ransomware has evolved beyond simple encryption. Modern attacks combine data theft with infrastructure destruction, creating double extortion scenarios where even organizations with solid backups face pressure to pay.
The lack of a public claim from a known ransomware group may indicate the attackers are using a private negotiation strategy, which could mean Kyowon is facing significant pressure to pay to prevent data publication. Alternatively, if this is an independent operation, the data may already be for sale on dark web markets.

Industry Response and Recommendations
Security experts recommend that South Korean companies review their posture in light of this breach pattern:
- Implement Zero Trust Architecture: Assume breach and verify every access request
- Conduct Privileged Access Audits: Regularly review and revoke unnecessary permissions
- Deploy Data Loss Prevention (DLP) Tools: Monitor for unusual data exfiltration patterns
- Establish Incident Response Playbooks: Pre-plan ransomware scenarios with clear decision trees
- Engage with Threat Intelligence: Monitor for indicators of compromise related to South Korean targets
The Kyowon Group's experience will likely become a case study in ransomware response and the importance of rapid, transparent communication with affected customers. As the investigation continues, the security community will be watching closely for technical details about the attack vector and the specific ransomware family involved.
For now, millions of South Korean families await definitive answers about whether their personal information has been compromised, while the country's corporate sector grapples with yet another reminder that cybersecurity is no longer optional—it's existential.
Related Resources:

Comments
Please log in or register to join the discussion