Hackers are auctioning what they claim is 860GB of Target's internal source code and developer documentation, obtained from the retailer's private Git server. After BleepingComputer contacted Target, the company's git.target.com infrastructure disappeared from the internet, lending credibility to the breach claims.
A threat actor is offering for sale what appears to be a massive trove of Target Corporation's internal source code, developer documentation, and infrastructure details. The alleged breach centers on Target's private Git server, which has gone offline following media inquiries about the incident.

The Breach Claims
Last week, an unknown attacker began posting evidence of their access to Target's internal development environment in private hacking communities. To substantiate their claims, they published multiple repositories on Gitea, a self-hosted Git service similar to GitHub, containing samples of what they described as "the first set of data to go to auction."
The sample repositories had revealing names that suggest they contain legitimate internal Target projects:
- wallet-services-wallet-pentest-collections
- TargetIDM-TAPProvisioingAPI
- Store-Labs-wan-downer
- Secrets-docs
- GiftCardRed-giftcardui
Each repository included a file named SALE.MD that functioned as a detailed manifest, listing tens of thousands of files and directories purportedly included in the complete dataset. According to these listings, the full archive spans approximately 860 GB.
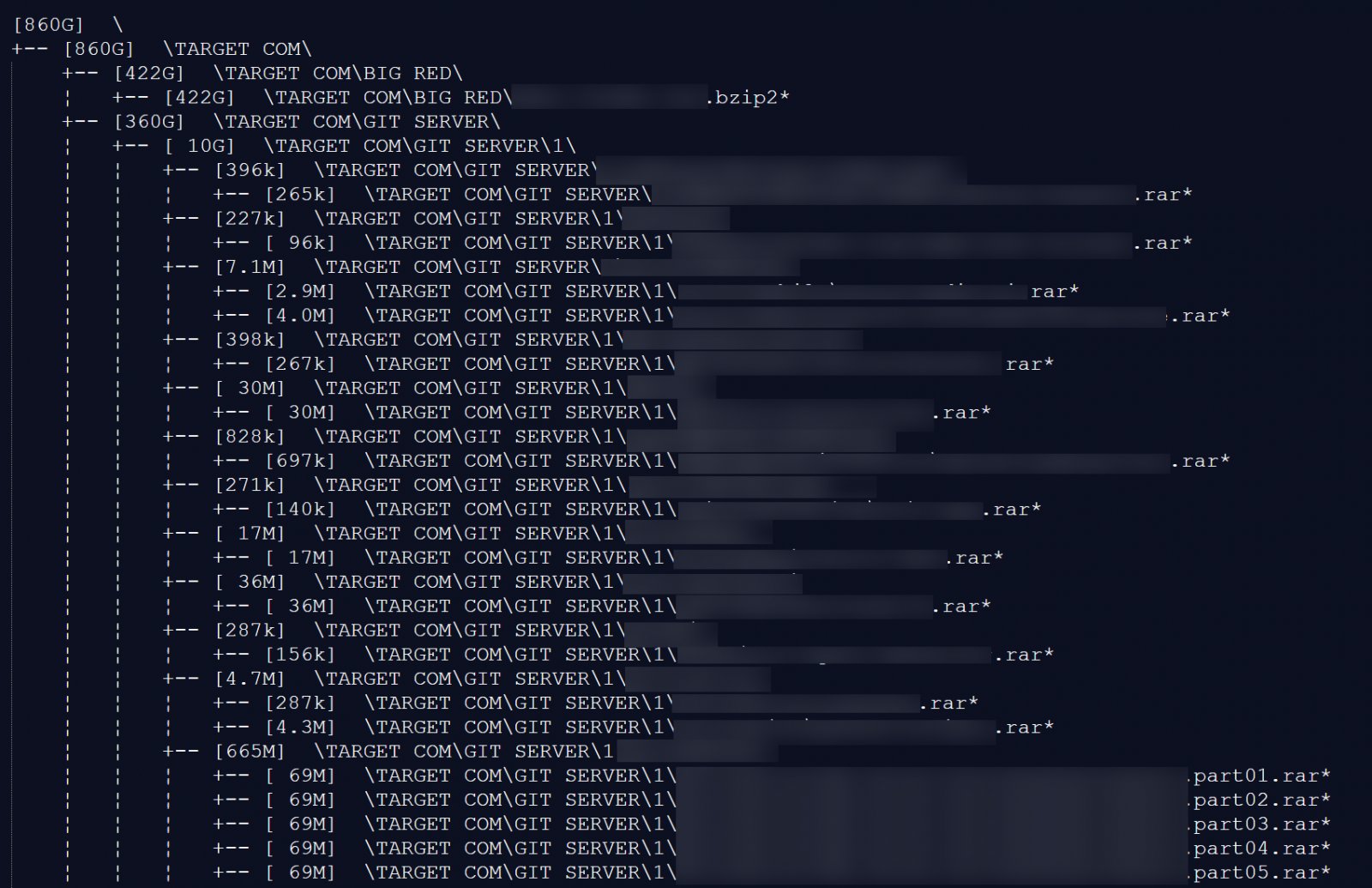
Evidence of Authenticity
Several factors point toward the leaked material originating from Target's actual private infrastructure rather than being fabricated or sourced from public repositories:
Internal References: The commit metadata and documentation reference the names of internal Target development servers and multiple current Target lead and senior engineers. The presence of real employee names in version control metadata is difficult to fake convincingly.
Private Infrastructure Links: The files contain links to internal Target platforms, including confluence.target.com, the company's internal wiki system. These URLs would not appear in open-source or public code repositories.
Directory Structure: The organization of repositories and the SALE.MD file structure are consistent with a large enterprise Git environment, not typical open-source project layouts.
No GitHub Match: The contents do not match any of Target's known open-source projects available on GitHub, suggesting the material—if authentic—originated from private development infrastructure.
Timeline and Target's Response
When BleepingComputer contacted Target with questions about the alleged breach last Thursday, the company did not immediately provide a substantive response. However, by Friday and Saturday, several changes occurred:
- All Gitea repositories hosting the sample code returned 404 errors, consistent with a takedown request
- Target's Git server at
git.target.combecame completely inaccessible from the internet
Prior to going offline, git.target.com redirected users to a login page, requiring connection through Target's corporate VPN or secure network. The sudden disappearance of the entire subdomain following media contact suggests Target took emergency containment measures.
Search engine caches reveal that some resources from git.target.com were indexed by Google at some point, indicating the server may have served public assets or had misconfigured access controls. However, this doesn't definitively prove the recent claims are related to that exposure.
What's at Stake
If the breach claims are accurate, the potential impact extends far beyond intellectual property theft:
Developer Credentials: Version control metadata often contains API keys, authentication tokens, and credentials embedded in configuration files or commit history. Even if these have been rotated, historical commits may expose patterns and infrastructure details.
Infrastructure Mapping: Internal server names, API endpoints, and network architecture details provide attackers with a blueprint for targeting other systems.
Security Vulnerabilities: Developer documentation frequently includes notes about security weaknesses, workarounds, or planned fixes—information that could be weaponized.
Supply Chain Attack Surface: The wallet-services and GiftCardRed repository names suggest these projects handle payment processing and gift card systems, potentially exposing transaction infrastructure.
Historical Context
Target's most significant publicly disclosed security incident remains the 2013 breach, where attackers compromised payment card data and personally identifiable information for up to 110 million customers. That breach cost the company hundreds of millions of dollars in settlements, security upgrades, and lost business.
While the current incident appears different in nature—targeting development infrastructure rather than customer payment systems—the potential for cascading effects is substantial. Source code access can enable sophisticated supply chain attacks, backdoor insertion, or facilitate breaches of production systems.
Practical Takeaways for Security Teams
This incident highlights several critical areas for organizations using Git-based development infrastructure:
1. Git Server Security Posture
Self-hosted Git servers require the same security rigor as production systems. Common misconfigurations include:
- Allowing public access to private repositories
- Insufficient network segmentation
- Lack of multi-factor authentication enforcement
- Absence of audit logging and monitoring
2. Secrets Management in Version Control
Even with private repositories, sensitive data often accumulates in Git history:
- Rotate credentials and keys stored in repositories
- Use git-secrets or similar tools to prevent accidental commits
- Implement pre-commit hooks that scan for sensitive patterns
- Consider using secret management systems like HashiCorp Vault or AWS Secrets Manager
3. Incident Response for Code Theft
Organizations should prepare specific playbooks for source code exposure:
- Immediate isolation of affected Git infrastructure
- Forensic analysis of access logs and commit patterns
- Assessment of what data was actually exposed vs. what attackers claim
- Credential rotation across all referenced systems
- Communication plans for stakeholders and potentially affected partners
4. Monitoring for Data Exfiltration
Detecting unauthorized access to development infrastructure requires:
- Baseline normal repository access patterns
- Alert on unusual clone volumes or data transfers
- Monitor for access from unexpected IP addresses or regions
- Track creation of new admin accounts or permission changes
5. Git Server Hardening
Specific technical controls for self-hosted Git:
- Enforce VPN or zero-trust network access
- Implement IP allowlisting for sensitive repositories
- Use repository-level access controls and branch protection
- Enable comprehensive audit logging
- Regular security assessments of Git hosting platforms
What Comes Next
Target has not yet officially confirmed whether a breach occurred or the scope of any potential exposure. The company's rapid takedown of the Git server and sample repositories suggests they are treating the claims seriously.
For security researchers and professionals, this incident serves as a reminder that development infrastructure often receives less security attention than production systems, yet contains equally sensitive information. The 860 GB figure, if accurate, represents years of development work, architectural decisions, and potentially sensitive operational data.
Organizations using self-hosted Git solutions should review their configurations immediately, paying particular attention to authentication requirements, network exposure, and secrets management practices.
If you are a Target employee or have additional information about this incident, you can contact BleepingComputer confidentially through their tip line or via Signal.
Related Resources:

Comments
Please log in or register to join the discussion