While developers focus on securing network communications, the silent vulnerability of insecure local data storage in IoT companion apps leaves sensitive credentials and operational data exposed. This deep dive examines how architectural flaws in mobile apps can compromise entire IoT ecosystems, using a smart lock companion app as a case study.
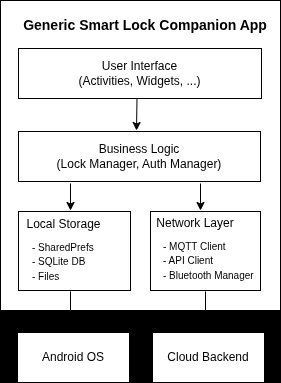
In the expanding landscape of connected devices, IoT companion applications serve as the critical bridge between physical hardware and user interfaces. While security teams rightly prioritize network communications and API endpoint protection, a more insidious vulnerability often lurks in plain sight: insecure data storage on mobile devices. This silent data leak—where sensitive information like device credentials, authentication tokens, and access codes are stored without proper protection—represents a significant threat that extends beyond mere privacy concerns to potentially enable unauthorized access, surveillance, or even life-threatening actions in critical IoT systems.

The Architecture of Risk
IoT companion applications persist sensitive data locally to ensure continuous operation during offline periods. This practice, while functionally necessary, creates a security challenge when implemented without proper safeguards. The data typically stored includes:
- Device identity and pairing data: Bluetooth pairing keys for local device communication and WiFi credentials for direct device access
- Authentication credentials: API access tokens (JWT, OAuth, bearer tokens) and user authentication state
- Operational data: Sensor readings, historical logs, and automation configurations
- Device access credentials: Smart lock PIN codes, camera stream credentials, and security system access codes
Android devices provide multiple storage mechanisms for IoT companion apps to persist data locally, each serving distinct functional purposes with different security characteristics. When improperly implemented, these mechanisms become sources of silent data leakage.
SharedPreferences: Located at
/data/data/[package]/shared_prefs/, this stores settings, tokens, and configuration values. Associated risks include XML-based plaintext key-value storage despiteMODE_PRIVATE:0600permissions.SQLite Database: Located at
/data/data/[package]/databases/, this stores device lists, relational data, and logs. Associated risks include an unencrypted binary format by default with broader0660permissions, adding group-level access to the existing apps' level permissions.Internal file storage: Located at
/data/data/[package]/files/, this stores configuration files and certificates. Associated risks include developer-defined formats without enforced encryption despite0600application level permissions.
{{IMAGE:3}}
Case Study: Smart Lock Companion App Vulnerabilities
Let's analyze vulnerabilities across these three local storage mechanisms through representative implementation examples in a smart lock companion app.
SharedPreferences Vulnerability
public void saveDeviceCredentials(Context context, String apiToken, String pin) {
SharedPreferences prefs = context.getSharedPreferences("device_prefs", Context.MODE_PRIVATE);
prefs.edit()
.putString("api_token", apiToken)
.putString("unlock_pin", pin)
.apply();
}
The corresponding XML file reveals the plaintext exposure:
<map>
<string name="api_token">eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...</string>
<string name="unlock_pin">987654</string>
</map>
This implementation suffers from two critical vulnerabilities: plaintext ASCII/UTF-8 encoding of the token and a readable XML structure that exposes data relationships.
SQLite Database Vulnerability
public class DeviceDatabaseHelper extends SQLiteOpenHelper {
@Override
public void onCreate(SQLiteDatabase db) {
db.execSQL("CREATE TABLE devices (" +
"id TEXT PRIMARY KEY, " +
"bluetooth_key TEXT, " +
"wifi_password TEXT)");
}
}
This database implementation introduces multiple security weaknesses: the standard SQLite format is readable by any SQLite client, historical access patterns are exposed, and there's no authentication mechanism at the database layer.
File Storage Vulnerability
public void saveDeviceConfig(Context context, JSONObject config) throws IOException {
File configFile = new File(context.getFilesDir(), "device_config.json");
FileOutputStream fos = new FileOutputStream(configFile);
fos.write(config.toString().getBytes(StandardCharsets.UTF_8));
fos.close();
}
This file storage approach creates vulnerabilities through plaintext JSON containing device keys, API endpoints, and credentials.
The Architectural Flaw
These vulnerabilities stem from a common architectural misconception: treating the app sandbox as sufficient protection. While Android's application sandbox provides isolation between apps, it does not inherently protect data from being extracted through various means including:
- Physical device access
- Malicious applications with appropriate permissions
- Backup and restore operations
- Debugging tools
- System-level vulnerabilities
The assumption that "private" storage equals "secure" storage represents a fundamental misunderstanding of mobile security principles. In IoT ecosystems where companion apps control physical devices, this misunderstanding can have catastrophic consequences.
Implications for Security Professionals
The impact of insecure data storage extends far beyond traditional privacy concerns. In IoT environments, compromised data can:
- Enable unauthorized physical access to secured spaces
- Allow surveillance through camera and microphone access
- Manipulate automation systems that control environmental conditions
- Compromise entire device networks through credential chaining
For security professionals, this vulnerability pattern highlights the importance of treating mobile apps as potential attack vectors rather than mere user interfaces. The security of IoT systems is only as strong as the security of their weakest component, which is often the mobile companion application.
Moving Forward: Beyond the Sandbox
Addressing this vulnerability requires a fundamental shift in how developers approach data storage in mobile applications. Security-by-obscurity through file permissions is insufficient. Instead, organizations must implement:
- Platform-provided encryption mechanisms like Android's EncryptedSharedPreferences
- Database-level encryption solutions
- Secure key management systems
- Runtime application self-protection (RASP) techniques
- Regular security audits focused on data persistence mechanisms
As IoT continues to permeate our homes, workplaces, and critical infrastructure, the security of companion applications becomes increasingly paramount. The silent vulnerability of insecure data storage represents not just a technical oversight but a potential gateway to widespread physical security breaches. Only by treating mobile apps with the same security rigor as the devices they control can we build truly secure IoT ecosystems.

Comments
Please log in or register to join the discussion