Fed up with escalating cloud expenses, a developer migrated their self-hosted services to a home server using Proxmox, prioritizing encryption, automation, and resilience. By leveraging Ansible and OpenTofu, they crafted a reproducible setup that safeguards against theft, hardware failure, and costly cloud dependencies. This deep dive reveals how strategic over-engineering empowers flexible experimentation with Kubernetes while slashing operational costs.
For years, many tech enthusiasts have relied on cloud providers or VPS solutions for self-hosting personal projects. But as costs balloon and control diminishes, a quiet rebellion is brewing—one centered on the humble homelab. One developer’s journey to reclaim autonomy, detailed in a recent post, showcases how meticulous automation transforms a mini-PC into a fortress of self-sufficiency. The goal? Eliminate recurring cloud fees while building a secure, adaptable playground for innovation.
Why Ditch the Cloud? The Calculus of Control
The catalyst was straightforward: frustration. A Raspberry Pi 4 buckled under encrypted backups, prompting a shift to a Minisforum UM880 Plus mini-PC. At €600, this hardware investment aimed to sidestep perpetual cloud subscriptions. But the move wasn’t just about frugality—it was about risk mitigation and learning. Hosting services locally meant accepting threats like burglary (risking data theft) or hardware failure (risking downtime). The solution? A trifecta of defenses:
- Full-disk encryption via LUKS to protect data if the physical server was stolen.
- Automated, versioned provisioning using Ansible and OpenTofu for rapid recovery.
- IP-KVM integration for remote Wake-on-LAN, ensuring accessibility even during outages.
Proxmox Virtual Environment emerged as the hypervisor of choice, enabling virtual machines (VMs) for isolated experimentation—crucial for safely exploring Kubernetes (k3s/k8s) without cloud bills spiraling out of control.
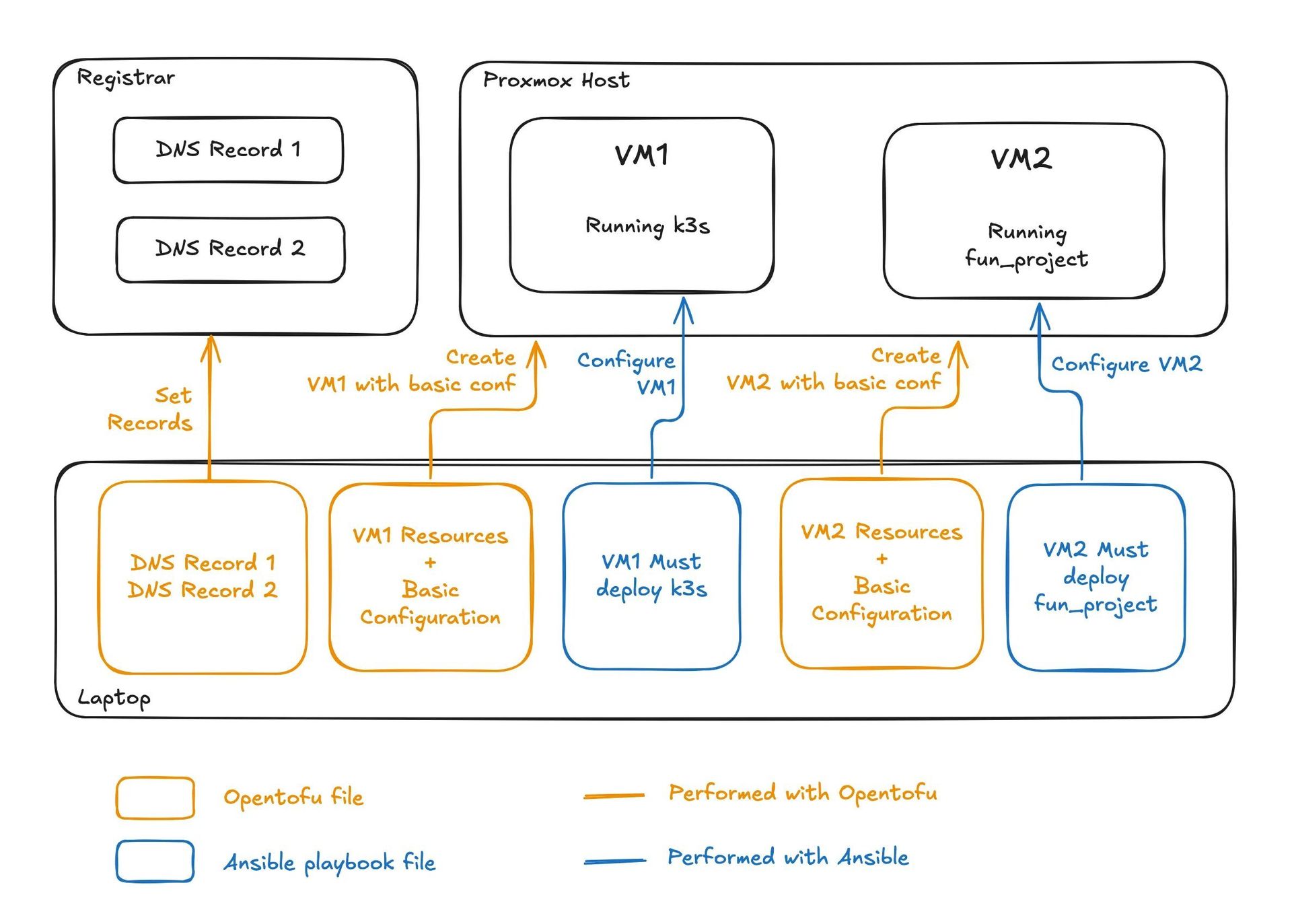
The Blueprint: Automation as the Backbone
The real genius lies in treating infrastructure as disposable. Proxmox itself and its VMs are ephemeral; only service data and configurations are backed up. This philosophy demanded robust IaC (Infrastructure as Code) tooling:
- OpenTofu (a Terraform fork) defines VM specs, networks, and DNS records declaratively.
- Cloud-init handles initial VM setup (users, SSH keys).
- Ansible enforces state across systems, from package installs to network configurations.
Here’s a snippet of OpenTofu spinning up a Debian VM for a k3s node:
resource "proxmox_virtual_environment_vm" "k3s-main" {
name = "k3s-main"
description = "Production k3s' main VM"
node_name = "proximighty"
cpu { cores = 4 }
memory { dedicated = 4096 }
disk {
size = 50
file_id = proxmox_virtual_environment_download_file.debian_cloud_image.id
}
}
Meanwhile, Ansible playbooks automate Proxmox host setup. For example, configuring a network bridge (vmbr0) to replace the physical NIC’s IP duties:
- name: Create bridge interface vmbr0
ansible.builtin.copy:
src: vmbr0
dest: /etc/network/interfaces.d/vmbr0
Overcoming Hurdles: Encryption and the Proxmox Quirks
Deploying Proxmox on encrypted Debian proved trickier than expected. The official installer lacks encryption support, necessitating a manual Debian install first. Worse, Proxmox installations sometimes bricked the system due to networking conflicts. The culprit? A missing static IP configuration. As documented, boot failures vanished once a fixed IP was assigned—a lesson in the perils of overlooked defaults.
Automation rescued reproducibility. An Ansible playbook now handles everything post-Debian install: adding Proxmox repos, installing kernels, removing bloat (like the Debian kernel and ntp packages), and enforcing reboots. Crucially, it manages LUKS encryption unlocks via manual input during reboots (with KVM) or Dropbear for headless setups.
Why This Matters Beyond the Living Room
This isn’t just a hobbyist’s tinkering—it’s a template for infrastructure resilience. By codifying every step, the homelab becomes portable. If hardware dies, services can temporarily migrate to cloud VMs using the same IaC. Later, they can repatriate to new hardware seamlessly. This approach dovetails with industry shifts toward hybrid environments and vendor-agnostic tooling.
Moreover, the setup democratizes advanced learning. Kubernetes experiments, often costly in the cloud, run risk-free on local VMs. As the author notes: "I won’t know what I’m doing while learning, and cloud providers get expensive fast."
The Payoff: Freedom Through Foresight
With Proxmox automated via Ansible and VMs orchestrated by OpenTofu, the homelab evolves from a cost-saving tactic into a strategic asset. It balances security (encryption, backups), flexibility (on-demand VMs for R&D), and operational simplicity. For developers and SREs, such setups aren’t over-engineering—they’re essential practice for an era of unpredictable costs and escalating threats. As cloud giants hike prices, the quiet hum of a well-automated homelab might just be the sound of liberation.
Source: ergaster.org
Comments
Please log in or register to join the discussion