An exploration of hosting a contemporary website on a 25-year-old Sun Netra X1 SPARC server using OpenBSD, examining the technical feasibility, security implications, and philosophical motivations behind reviving obsolete hardware.

When cloud computing dominates modern web infrastructure, the notion of hosting a production website on hardware manufactured before the iPhone existed seems deliberately anachronistic. Yet this precise challenge drives a fascinating technical experiment: Serving web content from a Sun Netra X1 SPARC server released in 2001. Beyond novelty, this project illuminates meaningful considerations about hardware longevity, minimalist computing, and security paradigms often overlooked in contemporary web development.
Hardware Resurrection

The Netra X1 represents enterprise computing from a different era: A single 500MHz UltraSparcIIe processor, 1GB of ECC SDRAM, and IDE hard drives. Originally deployed at Ford Motor Company, this decommissioned server presented immediate challenges. Its deafening stock fans required replacement with Noctua alternatives and custom 3D-printed mounts to achieve residential noise levels. More critically, the absence of video output necessitated network booting via PXE/TFTP/NFS since neither USB nor optical drives were bootable options. These constraints highlight how profoundly hardware interfaces have shifted over two decades.
Software Selection Philosophy

Faced with unsupported legacy Solaris versions, OpenBSD 7.8 emerged as the optimal operating system. Its security-first design philosophy aligned with the project's threat model, while continuing SPARC64 support demonstrated the BSD ecosystem's commitment to niche architectures. The installation consumed merely 55MB RAM post-boot—a testament to OpenBSD's frugality. Package management via pkg_add delivered essential utilities (git, vim, rsync) and even Rust toolchain support, though the web server selection proved deliberate: OpenBSD's native httpd over alternatives like nginx. This integrated solution offered automatic chroot isolation and simplified configuration—critical for minimizing attack surfaces.
Security Through Obscurity and Architecture
Exposing any home-hosted service demands rigorous security, particularly when using obsolete hardware potentially vulnerable to unpatchable exploits. The implementation employed layered defenses:
- Network Isolation: Cloudflare Tunnels created outbound-only connections from the SPARC server through a modern intermediary host (handling TLS termination externally)
- Firewall Hardening: OpenBSD's
pfenforced default-deny policies, permitting SSH only from internal subnets and HTTP solely from the tunnel proxy - Service Minimization: Disabling all non-essential daemons and limiting
httpdto static file serving eliminated dynamic execution risks - Content Simplicity: Pure HTML/CSS avoids client-side JavaScript vulnerabilities entirely
This architecture demonstrates how deliberate constraints can compensate for inherent hardware vulnerabilities.
Development Workflow Innovations
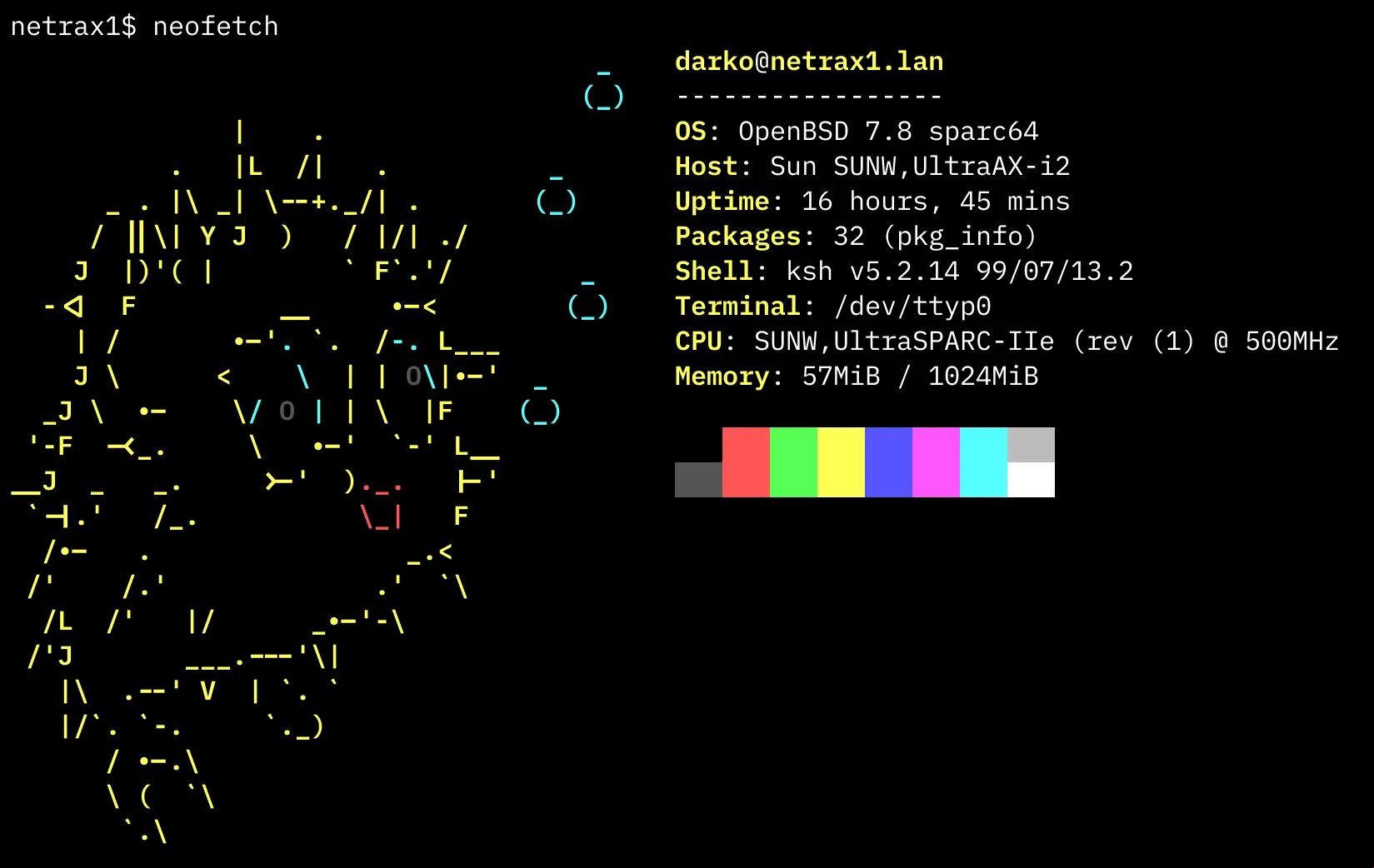
The website itself—a retro-styled about page featuring neofetch system output—emerged from an unconventional development approach. Rather than manual coding, specialized AI agents collaborated: A primary Rust-focused agent delegated frontend work to a subordinate agent trained explicitly for vanilla HTML/CSS generation. This division of labor reflects emerging patterns in AI-assisted development, where task-specific sub-agents outperform generalist models for specialized outputs.
Countering the Obvious Critiques
Why undertake such a project when Raspberry Pis or cloud instances offer cheaper, faster alternatives? Three motivations emerge:
- Sustainability: Reviving functional hardware prevents e-waste, extending device lifespans beyond planned obsolescence
- Security Education: Constrained environments force rigorous security practices often abstracted away in platform-as-a-service solutions
- Historical Preservation: Maintaining operational knowledge of SPARC architecture and OpenBSD's cross-platform capabilities
Broader Implications

This experiment transcends nostalgia. It demonstrates how contemporary tunneling solutions like Cloudflare's infrastructure enable secure exposure of legacy systems without compromising network security—a pattern applicable to industrial control systems or scientific instrumentation. The 55MB memory footprint challenges modern web bloat, while the fan modifications showcase how acoustic engineering can resurrect otherwise unusable hardware in residential settings.
Ultimately, projects like sparc.rup12.net represent more than technical curiosities. They question assumptions about necessary resources for web hosting while demonstrating that with careful security design, even twenty-five-year-old hardware can participate meaningfully in today's internet—not as museum pieces, but as functional nodes honoring computing's enduring foundations.

Comments
Please log in or register to join the discussion