Developer Alejandro Armas has created a collection of UEFI-based games that block system boot until users successfully complete gameplay challenges, implementing a novel security-through-gaming approach.

Linux developer Alejandro Armas (mycroftsnm) has released a unique collection of five UEFI games designed to gatekeep system boot access behind gameplay challenges. Hosted in the UEFIGame GitHub repository, these games implement a strict "Win → Boot, Lose → Shutdown" policy that physically powers down the system upon failure. Developed over 10 months, the project leverages UEFI's pre-boot execution environment to create what amounts to a mandatory gaming checkpoint before OS initialization.

Technical Implementation and Game Mechanics
Each game utilizes UEFI's native graphics capabilities and input handling to create distinct challenge formats:
- User Evaluation for Ineptness: Requires solving arithmetic problems (0-99 addition). Incorrect answers trigger immediate shutdown.
- Insult Sword Fighting: Monkey Island-inspired dialogue battles where users must select correct comebacks from a customizable
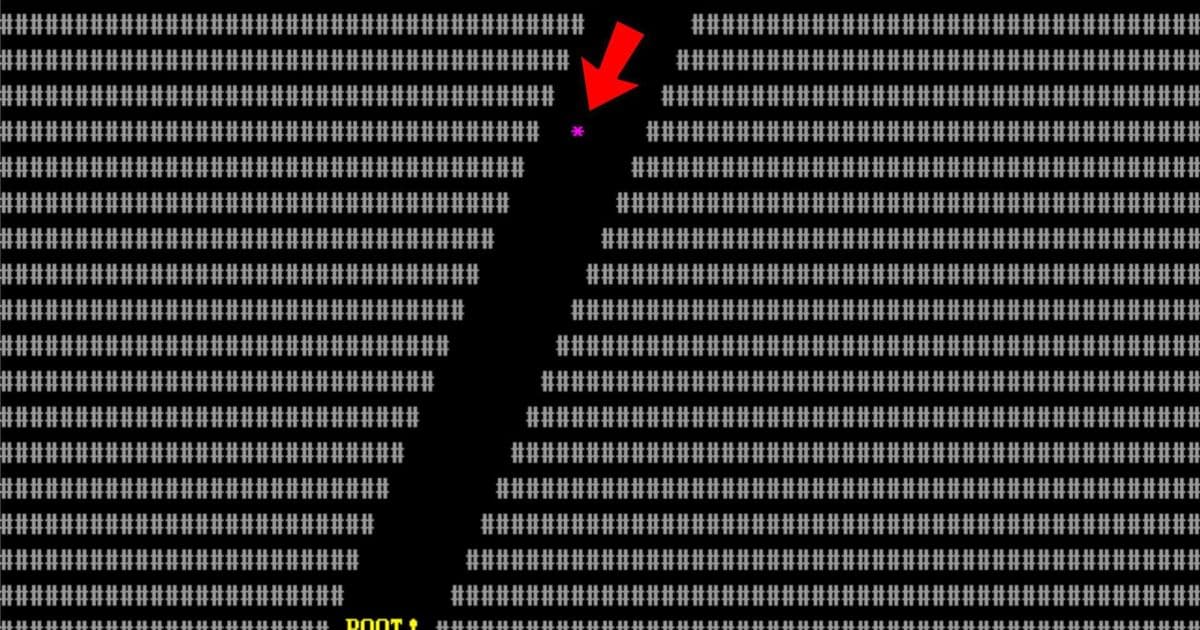
insults.txtfile. - Fall To Boot: Vertical scroller with procedurally generated tunnels where collision with walls prevents boot.
- Age Verification: 1980s pop-culture trivia quiz filtering users based on cultural knowledge.
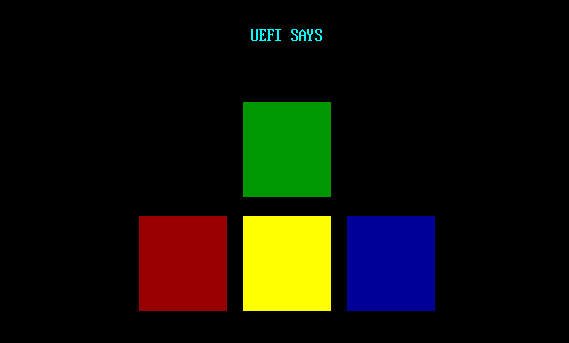
- UEFI Says: Pattern-matching memory game testing recall under time pressure.
All games execute directly within the UEFI environment before any operating system loads, using the GOP (Graphics Output Protocol) for rendering and EFI drivers for input processing. The shutdown mechanism leverages ACPI commands, ensuring no bypass without hardware intervention.
Firmware Security Implications
This project highlights UEFI's expanded capabilities compared to legacy BIOS systems. Modern UEFI implementations provide:
- Graphics output support (1280x1024 resolution in these games)
- File system access for configuration files
- Pre-OS networking capabilities
- Extended driver support
While primarily a novelty project, the concept demonstrates potential security applications. Forcing user interaction before boot could theoretically augment authentication systems—though current implementations prioritize entertainment over robust security. Unlike traditional password prompts, gameplay challenges resist brute-force attacks by varying requirements dynamically.
Market Context and Development Effort
Armas' 10-month development timeline reflects UEFI programming complexities. Unlike OS-level development, UEFI coding requires:
- Working with limited memory resources (typically <1MB during early initialization)
- Absence of standard libraries
- Direct hardware manipulation
The project joins niche UEFI applications like Inkbox Software's Zaxxon recreation, demonstrating firmware's expanding role beyond basic hardware initialization. While not commercially viable currently, such projects highlight how UEFI's Turing-complete environment enables creative system-level innovations.
For demonstration videos and installation instructions, visit the UEFIGame GitHub repository.
Comments
Please log in or register to join the discussion