Australian authorities warn that state-sponsored hackers continue to exploit a critical 2023 Cisco IOS XE vulnerability to implant BadCandy webshells on unpatched devices. Over 150 Australian systems remain compromised despite available patches, with attackers systematically re-infecting routers after reboots. The campaign highlights systemic patching failures and ongoing infrastructure risks in critical networks.
Unpatched Cisco Devices Under Siege: Australia Warns of Persistent BadCandy Webshell Attacks

October 31, 2025 — The Australian Signals Directorate (ASD) has issued an urgent alert about ongoing state-sponsored cyberattacks targeting unpatched Cisco IOS XE devices across the country. Attackers are exploiting the critical CVE-2023-20198 vulnerability—patched by Cisco two years ago—to implant BadCandy, a Lua-based webshell granting root-level control of compromised routers and switches.
Anatomy of an Enduring Threat
The 10/10 severity flaw enables remote attackers to create privileged accounts on Cisco devices via the web interface. Despite Cisco's October 2023 patch and subsequent warnings, thousands of internet-exposed systems remain vulnerable globally. Public exploit availability shortly after disclosure fueled mass exploitation, with BadCandy becoming the payload of choice for persistent access:
-- Simplified BadCandy webshell functionality
function execute_command(cmd)
local handle = io.popen(cmd)
local result = handle:read("*a")
handle:close()
return result
end
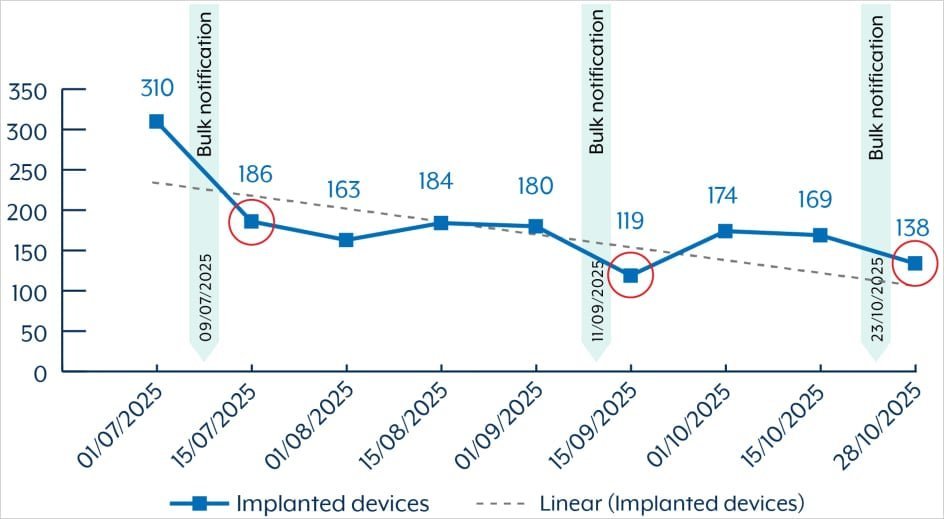
Graph: BadCandy infection trends in Australia (Source: ASD)
The Reinfection Cycle
Alarmingly, ASD reports over 150 Australian devices still host active BadCandy implants as of late October 2025, down from 400+ infections observed since July. The webshell's volatility—it disappears on reboot—belies its persistence:
"Attackers detect removal and re-exploit unpatched devices within hours. Without fundamental remediation, patching is like bailing water from a leaking boat," an ASD spokesperson noted.
This re-infection pattern confirms threat actors maintain infrastructure monitoring and automated re-compromise capabilities. The ASD attributes recent activity to sophisticated state-sponsored groups, including China-linked 'Salt Typhoon' (aka Volt Typhoon), previously implicated in attacks against North American telecom providers.
Global Implications and Mitigation
While targeted in Australia, the campaign underscores universal risks:
- Patching gaps: Critical vulnerabilities linger for years in network infrastructure
- Webshell evolution: Lightweight implants evade traditional detection
- State actor persistence: Espionage groups prioritize operational network access
Cisco's hardening guide recommends:
- Immediate patching of IOS XE systems
- Disabling the HTTP/S web interface on internet-facing devices
- Implementing strict access control lists (ACLs)
The ASD is directly notifying victims and collaborating with ISPs to trace unclaimed devices. For administrators, this incident reinforces non-negotiable principles: patch critical infrastructure promptly, assume compromise after exposure, and validate mitigations through traffic analysis. As webshell tactics evolve, so must defenses at networking's frontlines.
Source: BleepingComputer

Comments
Please log in or register to join the discussion