A sophisticated Linux malware framework designed specifically for cloud environments signals a strategic shift in cyberattacks, prioritizing stealthy infrastructure control over endpoint compromise.

The emergence of VoidLink represents more than just another malware variant; it signifies a fundamental reorientation of offensive cyber operations toward the infrastructure underpinning modern digital ecosystems. This cloud-native Linux malware framework, analyzed in depth by Check Point Research, diverges from traditional Windows-focused threats by targeting the very environments where organizations deploy their most critical applications and services. Its architecture reveals a sophisticated understanding of cloud operations, containerization, and defensive evasion techniques that collectively redefine what constitutes a high-value target in contemporary cybersecurity.
Cloud-Native Architecture
Unlike malware retrofitted for cloud environments, VoidLink exhibits intentional design choices optimized for cloud infrastructure from inception. Its environment-aware execution enables dynamic adaptation based on the specific cloud provider, virtualization technology, or container runtime it detects. This situational awareness allows it to mimic legitimate cloud operations with remarkable fidelity, embedding malicious activity within normal administrative processes. The framework's cloud-first approach reflects threat actors' recognition that compromising the infrastructure layer delivers broader strategic advantages than traditional endpoint-focused attacks.
Modular Expansion Capabilities
VoidLink functions as an extensible attack platform rather than a monolithic payload. Its plug-in architecture supports over 30 interchangeable modules that threat actors can dynamically deploy based on reconnaissance findings. This includes capabilities for:
- Credential harvesting from cloud metadata services and local configurations
- Lateral movement across container clusters and virtual networks
- Forensic countermeasures that erase execution traces
- Container escape and privilege escalation techniques
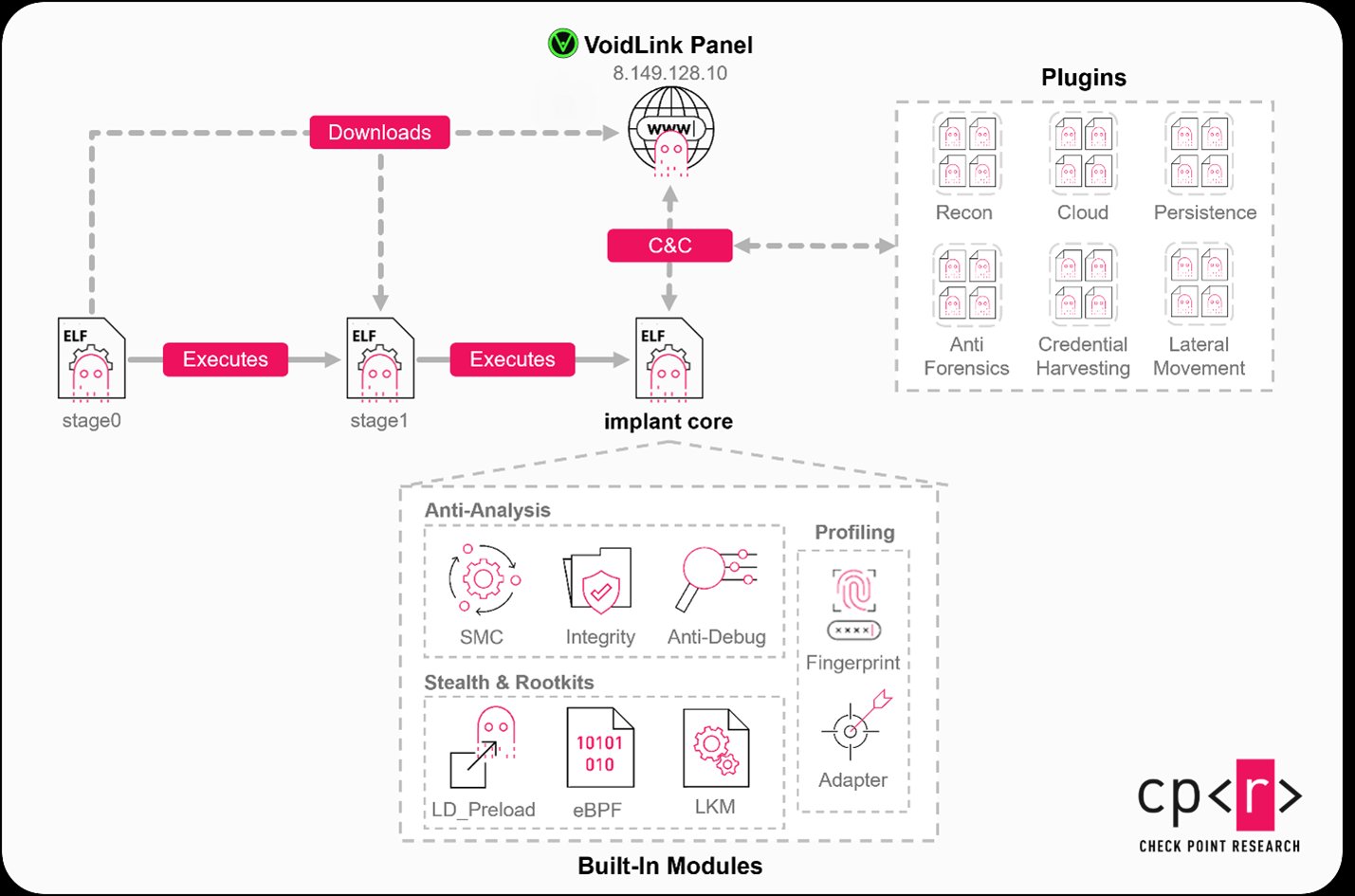
Figure: VoidLink's modular architecture enables targeted capability deployment
The framework's API-driven design enables operators to remotely deploy new functionality without reinstalling core components. This extensibility transforms VoidLink into a persistent threat platform that evolves alongside defensive measures, maintaining operational relevance long after initial compromise.
Context-Aware Stealth Mechanisms
VoidLink's most distinctive capability lies in its adaptive operational security. The framework conducts real-time environmental assessments to detect security controls like:
- Endpoint detection and response (EDR) agents
- Cloud workload protection platforms
- System integrity monitoring tools
Based on this analysis, VoidLink dynamically modulates its behavior—slowing operations in heavily monitored environments while accelerating activity in less-secured contexts. This context-sensitive stealth represents a significant evolution beyond static evasion techniques. Additional security features include runtime memory encryption for critical components and a self-destruct mechanism triggered by analysis attempts.
Professional Development Indicators
Analysis suggests VoidLink originates from Chinese-affiliated actors, evidenced by coding patterns, infrastructure management practices, and targeting preferences. The framework demonstrates professional-grade development including:
- Multi-language implementation combining Golang, C, and Python
- Version-controlled development cycles
- Dedicated command-and-control infrastructure
- Web-based operator console for centralized management
While no confirmed in-the-wild deployments have been observed, the framework's completeness suggests operational readiness. Its design parallels legitimate security tools like Cobalt Strike, raising concerns about potential proliferation among cybercriminal groups despite possible nation-state origins.
Strategic Implications for Defenders
VoidLink fundamentally challenges conventional security assumptions about Linux and cloud environments:
- Infrastructure as Primary Target: Cloud management layers now represent higher-value targets than individual endpoints
- Detection Gap: Traditional endpoint security provides limited visibility into orchestrated container activities
- Persistence Model: Ephemeral cloud resources require malware designed for persistent infrastructure access
Defenders must recalibrate security postures by:
- Implementing cloud-native detection that analyzes orchestration APIs
- Enforcing strict network segmentation for management interfaces
- Monitoring container runtime behaviors for anomalous activities
- Validating cloud configuration against infrastructure-as-code templates
As organizations migrate critical operations to cloud environments, frameworks like VoidLink demonstrate that threat actors are simultaneously shifting their focus upward in the technology stack. This evolution demands equivalent advancement in defensive approaches that recognize cloud infrastructure as both a strategic asset and a primary attack surface.
For comprehensive technical analysis, see the full VoidLink research report.

Comments
Please log in or register to join the discussion