The 'shift left' security strategy has increased developer burnout while failing to improve security outcomes. Qualys research reveals 7.3% of public container images contain malware, highlighting systemic flaws in current approaches. The solution lies in shifting security responsibilities down to infrastructure teams through automation and 'golden paths'.

For nearly a decade, the security industry championed 'shift left' as the solution to secure software development. The premise was simple: integrate security earlier into the development lifecycle by empowering developers with security tools. Yet this approach has backfired spectacularly, creating friction between security and development teams while failing to stem the tide of vulnerabilities. Ivan Milenkovic, Vice President of Risk Technology EMEA at Qualys, explains: "Businesses demand fast, good, cheap and secure. When push comes to shove, 'fast' always wins."
The core problem lies in misaligned incentives. Developers face crushing pressure to deliver features rapidly, while security tools often introduce friction—slow scans, false positives, and disconnected workflows. Milenkovic observes: "If a developer's bonus depends on shipping features by Friday and the security scan blocks the build for four hours, they'll find a way around the scan." This conflict manifests dangerously in dependency management, where developers frequently pull public container images to accelerate work.
Qualys Threat Research Unit recently analyzed 34,000 container images from public registries like Docker Hub, revealing alarming trends:
- 7.3% (2,500 images) were confirmed malicious
- 70% contained cryptomining software
- 42% exposed more than five secrets (AWS keys, GitHub tokens, database credentials)
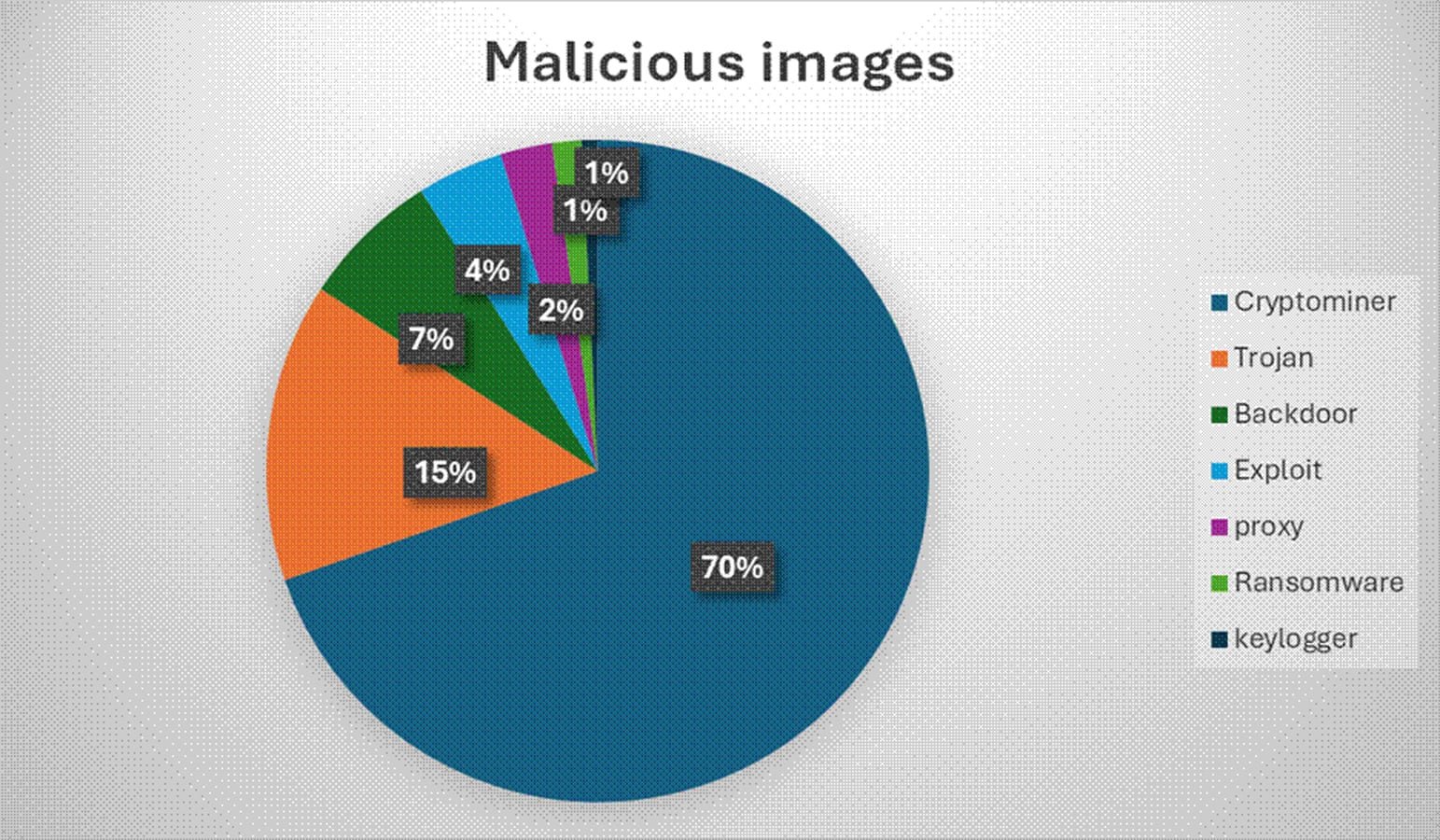
Typosquatting remains attackers' primary tactic—malicious images impersonating legitimate ones through slight name variations. "Telling developers to 'be more careful' isn't a security strategy," Milenkovic emphasizes. Even trusted registries operated by Docker, AWS, or Google offer no guarantee of safety, yet organizations treat them as curated libraries.
The solution isn't more developer burden, but a fundamental restructuring Milenkovic calls "shift down":
Establish Golden Paths: Provide pre-approved templates, base images, and CI/CD pipelines where security is automatic. Using these standardized resources makes security the path of least resistance.
Automate Enforcement: Platform engineering teams implement infrastructure-level guardrails:
- Admission controllers block non-compliant containers
- Infrastructure-as-Code policies enforce standards (e.g., Terraform modules requiring S3 versioning)
- Automated fixes (like PRs for vulnerable base images)
Runtime Autonomy: Security systems autonomously respond to threats—killing malicious pods instead of just alerting.
Clear Off-Ramp Processes: When developers need custom solutions, establish collaborative security reviews upfront rather than retrospective fixes.
This approach shifts cognitive load from developers to specialized platform teams. "Developers shouldn't need to know how vulnerability scanning works," notes Milenkovic. "They just need to know the door locks if they try to deploy critical vulnerabilities."
The shift down model acknowledges reality: security can't succeed when pitted against development velocity. By baking protection into infrastructure and automating responses, organizations finally align security with business objectives. As Milenkovic concludes: "We burn out developers when we pile security onto their existing load. The alternative is making security invisible until it's truly needed."
For technical teams implementing this approach, Qualys provides cloud-native application protection solutions that integrate vulnerability management and compliance across development pipelines. Platform engineers can explore enforcement frameworks like Crossplane compositions and Open Policy Agent for policy-as-code implementations.

Comments
Please log in or register to join the discussion