Security researchers uncover a sophisticated attack chain exploiting Microsoft Application Virtualization scripts to bypass security controls and deliver Amatera infostealer malware through steganographic payloads.

A new malware campaign is exploiting Microsoft's enterprise virtualization technology to deliver information-stealing payloads while evading detection, security researchers at BlackPoint Cyber warn. The attack combines fake CAPTCHA checks with abuse of trusted Windows components to ultimately deploy the Amatera infostealer.
Microsoft Application Virtualization (App-V) allows enterprises to run applications in isolated virtual environments without local installation. Attackers are now abusing the SyncAppvPublishingServer.vbs script - a legitimate App-V component - to proxy malicious PowerShell execution through Microsoft's trusted wscript.exe binary.
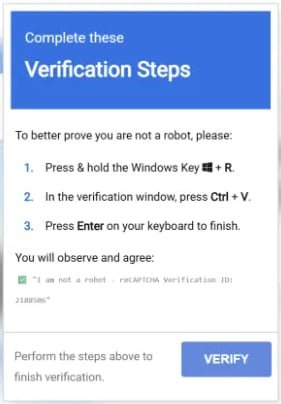
The attack begins with victims encountering fake CAPTCHA verification pages that instruct them to manually paste a command into the Windows Run dialog. This command executes the App-V script, which initiates a multi-stage attack chain designed to bypass security measures:
- Environment Validation: The script verifies manual execution and checks for unchanged clipboard contents to evade sandbox environments
- Stalling Tactics: When analysis environments are detected, the malware enters infinite wait loops to waste automated resources
- Covert Configuration: Attackers retrieve base64-encoded configuration data from public Google Calendar events
- Steganographic Delivery: PNG images hosted on public CDNs contain hidden payloads extracted via LSB steganography
- Memory Execution: Decrypted PowerShell payloads execute native shellcode directly in memory
The final payload is Amatera, an information stealer malware-as-a-service (MaaS) operation based on the ACR infostealer. According to Proofpoint researchers, Amatera has shown increasing sophistication in recent updates. Once active, it collects browser credentials and system data, communicating with command-and-control servers via HTTP POST requests.
Defense Recommendations
BlackPoint Cyber researchers recommend these mitigation strategies:
- Restrict access to Windows Run dialog via Group Policy
- Remove App-V components if not actively used in your environment
- Enable PowerShell module logging for execution monitoring
- Monitor outbound connections for mismatches between HTTP Host headers/TLS SNI and destination IPs
- Implement network segmentation to limit potential lateral movement
This attack demonstrates attackers' growing sophistication in abusing trusted enterprise components. The combination of App-V script abuse, steganographic payload delivery, and manual execution bypasses creates significant detection challenges, underscoring the need for layered defenses and user education about social engineering tactics.

Comments
Please log in or register to join the discussion