Search Results: "FP"
Found 77 articles

Hardware
PlayStation 6 Rumors Suggest 4K 120 FPS with Ray Tracing Target
3/8/2026
Regulation
AnsiSaver Brings Back the Art of the BBS Era with macOS Screensaver
3/8/2026

Hardware
PS5 Gets Linux Treatment: Modder Runs GTA 5 Enhanced Edition with Ray Tracing at 60 FPS
3/7/2026
Rust
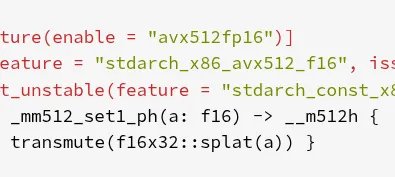
Rust 1.94 Brings AVX-512 FP16 Intrinsics and Array Windows to Stable Channel
3/6/2026

Hardware
Crimson Desert PS5 Pro Performance Promises 4K/60 FPS with PSSR 2 Upscaling
3/5/2026

Hardware
Lenovo Legion Tab Gen 5 Gaming Benchmarks Reveal Impressive Performance
3/5/2026

Trends
Assassin's Creed Unity gets free 60 FPS patch as Ubisoft officially teases Black Flag Resynced remake and outlines future AC roadmap
3/5/2026

Hardware
Cisco Catalyst C1300-12XS Review: A 12-Port 10GbE Managed Switch for Modern Networks
3/4/2026