Search Results: "VPN"
Found 65 articles

Cybersecurity
Iranians Turn to Starlink and Decentralized Apps Amid Severe Internet Blackout
3/2/2026
Regulation
KDE Plasma 6.7 Preps Rounded Style UI Enhancement For QtWidgets-Based Apps
2/28/2026

Regulation
Nokia Patent Injunction Forces Acer and Asus German Website Shutdown, Crippling Customer Support Access
2/19/2026

Regulation
Spanish Court Orders VPN Providers to Block Football Piracy Sites
2/18/2026
Vulnerabilities
CISA Adds Four Known Exploited Vulnerabilities to Catalog
2/17/2026

Privacy
Russia's Digital Iron Curtain: How the Max Super-App Is Centralizing State Surveillance
2/16/2026
Security
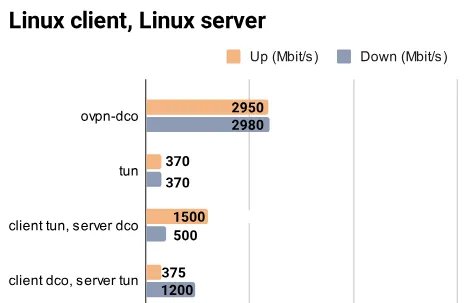
OpenVPN 2.7 Released With Multi-Socket Server & DCO Linux Kernel Driver Support
2/11/2026

Hardware
TP-Link Omada VPN Gateway ER8411 Review: 10Gbps Performance with Enterprise Features
2/9/2026